Previous parts in this series have been:
Office 365 Mobile MDM – Modern Device Management with Microsoft 365 Business Premium–Part 1
Intune MDM – Modern Device Management with Microsoft 365 Business Premium – Part 2
Intune MAM – Modern Device Management with Microsoft 365 Business premium – Part 3
Endpoint Manager – Modern Device Management with Microsoft 365 Business Premium – Part 4
Baselines – Modern Device Management with Microsoft 365 Business Premium – Part 5
Deployment – Modern Device Management with Microsoft 365 Business Premium – Part 6
Autopilot admin – Modern Device Management with Microsoft 365 Business Premium – Part 7
Autopilot endpoint – Modern Device Management with Microsoft 365 Business Premium – Part 8
In part 3 I talked about Mobile Application Management (MAM) and in the last part, I talked about Windows deployment using Autopilot, now it is time to look at deploying applications to devices via Endpoint Manager.

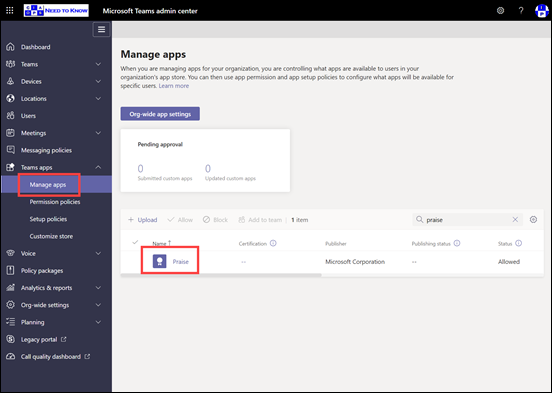
This tasks will be accomplished via the All apps option inside the Apps menu in Microsoft Endpoint Manager as shown above.

Here you’ll see a list of existing applications, but what you’ll typically need to do is select Add from the menu at the top to add a custom application.
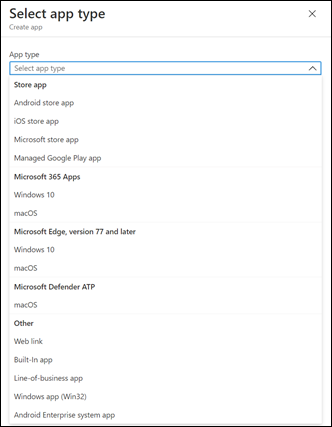
You’ll now need to select an app type, as you can see above, from the list that appears. Because we are dealing with applications across a wide range of platforms, you need to create a deployment policy for each app on each platform.

In this case, I’ll go with an application from the iOS store as shown above, just to keep things simple.

I’ll then need to select the link, as shown above, to Search the App Store for the desired application. Note that it doesn’t necessarily have to come from the store, but it is easier if it does.

Here, I’ll locate Microsoft Whiteboard as shown above and select it.

The details of the app are now populated as shown above. You can make any changes here you wish. Note, I have elected to feature this app in the Company Portal as well.

Next, I can target that application to be Required by users and or devices, which I have done as shown above. However, you see that it is possible to just make the application available (i.e. optional) for enrolled and non-enrolled devices as well as being able to uninstall the application if present.

You can now review the application settings and then press the Create button to complete the policy process.

In a short amount of time the device will process that policy as seen above. Here the user will be prompted that a required application will be installed. Press Install on device to continue.

The application will be installed.

The application is now ready for use on the device.

If you now look back at the All Apps area, as shown above, you should see the app that was just configured for deployment.

If you select this entry and then select Device install status, you should see a confirmation that the Status is installed as shown above.

If you take a look inside the Intune Company Portal App, you see the app is featured as shown above. The application can now be installed directly from here as well if needed.

To configure the settings for applications that are deployed, navigate to the the App configuration policies option as shown above and select the Add button that appears on the right.

Here, I will select Managed devices from the drop down menu that appears.

To keep things simple, I’ll choose to configure the Outlook app for iOS. This is because there are many different ways to configure applications, especially if they are not from Microsoft or not common apps like Outlook, Word, Excel, etc.
In this case, you need to click the Select app at the bottom of the page as shown.

Select the Outlook option from the menu that appears as shown.

Because this a ‘well-known’ app, I select Use configuration designer in the Configuration settings format field as shown. This presents a number of options I can now configure for that application.
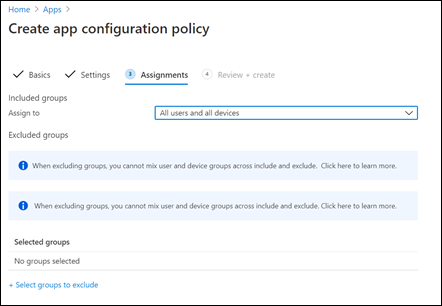
You’ll then need to allocate this application configuration policy as shown above. Again, to keep this example simple, the option for All users and all devices has been selected but you can get more granular if you wish.

You can now Review and Create the policy.

The policy should then appear in the list of App configuration policies as shown above. You can select the policy name at any time to return to editing the policy.

The main take away is that you can use Endpoint Manager to create deployment and configuration policies for the different applications on the different platforms and apply them quickly and easily. As shown above, this also extends to granular configuration of the Office suite of apps.
It is important to remember that there can be a lot to configure here if you consider individual apps on individual platforms, so be prepared for some set up initially. But, once complete, deployment and configuration going forward across all platforms is easy. The main benefit is that both deployment and configuration can be done directly across the Internet for both enrolled and non-enrolled devices give good management of devices in the environment.
Modern Device Management with Microsoft 365 Business Premium – Part 10