What I want to achieve in this process is to create a single Microsoft Dataverse database inside a Microsoft Teams and allow a basic Power Automate to add data to it.

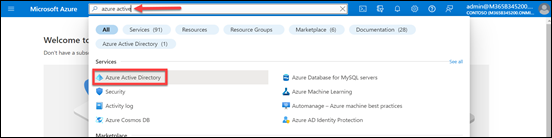
Firstly, navigate to a Microsoft Team in the environment (here Automation), and select the + (plus) icon along the menu on the right as shown above.

In the list of options that appears, search for, and select Power Apps as shown above.

The first interesting thing, once you do that, is you typically can only select from pre-existing Power Apps that are listed in the dialog. However, there is an option create an app in Power Apps that you can select towards the bottom of the dialog as shown above.

You should then see the dialog display, like the one above, telling you to wait while things get set up.

If this process gets hung up after a minute or two, just refresh the page in your browser. You should now see something like that shown above with a list of the Microsoft Teams on the left. If you select the Microsoft Team you want to put the Dataverse database into (here Automation) you should see that nothing is built yet in the information area on the right.
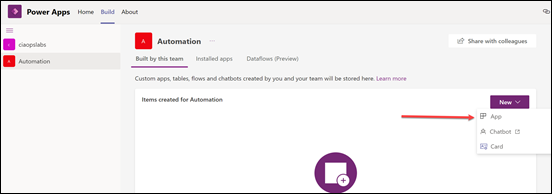
Select the New button on the right and then App from the options that appear as shown above.

If you take a quick peek at the Power Platform admin center, in a new browser tab, and then Environments from the menu on the left or use the direct link:
https://admin.powerplatform.microsoft.com/environments
You’ll see that a new Power Platform environment has been created matching the name of the Microsoft Team (here Automation).
As the Microsoft documentation on Power Platform environments says:
https://docs.microsoft.com/en-us/power-platform/admin/environments-overview
A Power Platform environment is a space to store, manage, and share your organization’s business data, apps, chatbots, and flows. It also serves as a container to separate apps that might have different roles, security requirements, or target audiences.
In essence, think of an environment as a container to store things you create in the Power Platform. When you create a Power Platform App inside a Microsoft Team, it creates them in a unique container.

The idea is that you should be able to easily switch between environments. However, if you navigate to the Power Platform service directly at:
https://make.powerapps.com/
You are not able to see the environment just created in Microsoft Teams as shown above for some reason. It seems the only environments you can see here are those created directly in the Power Apps make portal.

You can drill into the new Teams environment you just created in the Power Platform admin center by selecting it from the list. Information about the environment will be displayed as shown above.

If you return to your app creation process inside the Microsoft Team, you’ll now need to give your app a name (here Capture)

Typically, you build a full app here but for now all we want to create is a single database, so select the Data icon on the left (cylinder) as shown and then select the Create new table button to the right of it.

You’ll then be asked to give the table a name (here Id). If you open the Advanced settings option at the bottom of the dialog, you’ll see that there are not many additional options to select from.
Select the Create button to continue.

You should now see the table displayed as shown above. You’ll also notice that there is already a column called Name created. This is a bit like when you create a new SharePoint list and get a single column created for you as well.

If you try and edit this initial column by selecting the header and then the Edit column option from the menu that appears above,

you’ll find there are not a lot of options available. This maybe limiting or just annoying as it is in SharePoint, but for now just leave that column in place. You’ll just need to remember to put some data in it as it is a required field.

You can then add any addition columns you require. Here I’ve added the columns Domain, Date and Value. These are the fields I want to populate with custom data.

If I return to the previous screen you should now see the Dataverse database listed as shown above.

Returning to the Build page in Power Apps in Microsoft Teams, and selecting the Microsoft Team (here Automation), you should now see some entries in the Items created for Automation list on the right. Here, you should also see the database just created as noted above.

If you select the database directly from this screen you can drill in and see the table and any entries as shown above. No data appears in the table yet as none has been added.

The way to get data into the database here will be via a very basic Power Automate Flow. It is a good practice to create this also inside the same Power Platform environment in which the Dataverse database was just created. Do this via the Cloud Flows option on the left as shown above.

To create a Flow, select Cloud Flows, then from the menu at the top on the right select the + New button. From the options that appear select Cloud Flows then type of Flow desired (here an Instant Flow).

The process for creating a Flow is the same as if you were creating a stand alone Flow via the Power Automate service. In this case, simply add the Dataverse Add a new row action as shown above. Configure this action to connect to the Dataverse database created earlier (Ids), then add some random text for the required default Name field (Hello), then data for Date, Domain and Value as shown above.
Save and Run the Flow.

If everything is correct, the Flow should run without errors as shown above.

If you then look at the details of the database you should see that it now has data inside it as shown above.

You could also create a Flow directly from the Power Automate service, but remember to switch to the new Microsoft Teams environment that was created by adding a Power Automate app to the Microsoft Team before creating the Flow.

The final interesting item here is to look at the capacity of the new database in the Power Platform admin center where you’ll find that, although you have a total size of 2GB, about 25% has already been consumed by the system.
For more information about the Dataverse for Teams consult the Microsoft documentation here:
About the Microsoft Dataverse for Teams environment