I have written before about how Azure can be used to backup files and folders quickly and shown how to set all that up here:
Azure Desktop Backup
Recently, Azure Backup was extended to now be able to do server services like Exchange, SQL, SharePoint etc:
Azure backup now does servers
This involves a different process to setup and so here is the walk through process of setting Azure Backup Server for Applications.

You’ll need to have an Azure Backup Vault already in place as the destination for your backups. You create this Azure Backup Vault in the Azure management console under the Recovery Services option. You can have as many Azure Backup Vaults as you wish and my personal practice is to have a separate vault for each machine. If you need to create a new vault I have detailed how to do this previously.

Once the vault has been created you’ll need to download the Azure Backup software. You can find this in the details for the Backup Vault as shown above. You need to download the Microsoft Azure Backup for Applications.
This will in effect take you to the following download link:
https://www.microsoft.com/en-us/download/details.aspx?id=49170

Which will allow you to download the software. Beware that the Backup for Applications software is about 3.2 GB in size. Why? Because it includes the Microsoft Data Protection Manager (DPM) and SQL 2014.

There are number of different files you need to download, as shown above. Place them all the same directory and then run MicrosoftAzureBackupInstaller.

The installation process will now commence. Select Next to continue.

The next step in the process is to expand the downloaded files into a single installation directory. You can customise this directory if desired. Select Next to continue.

Select Extract to continue.

The files will now commence extracting into the directory that you nominated.
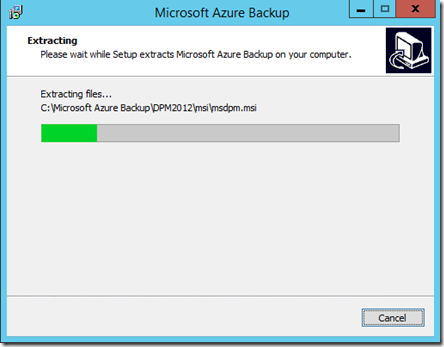
Be patient, the extraction process will take a few minutes.

When the extraction process is complete you are given the option to Execute setup.exe to install the software. Leave this option selected and press Finish.

The setup splash screen should now appear as shown above. From this screen select Microsoft Azure Backup under the Install column on the left.

The C++ Runtime will now be installed.

The setup screen should now appear as shown above. Select Next to continue.
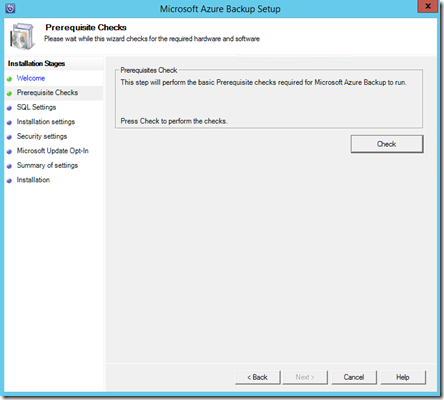
Select the Check button in the top right to ensure all the prerequisite software is installed.

If the prerequisites are met you should see a message confirming that as shown above. Select Next to continue.
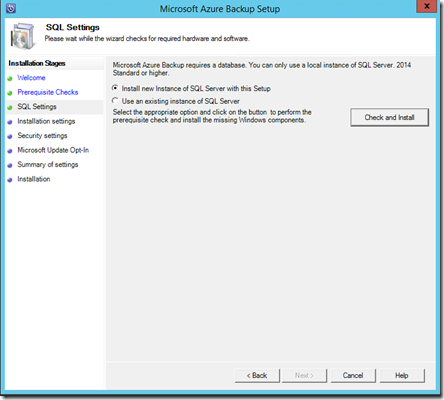
You’ll now need to specify an SQL server as part of the configuration. You can configure an existing SQL server on your network or you can elect to install a new instance on the current machine. If you select an existing SQL Server it will need to be running SQL 2014.
In most cases you’ll want to install a new instance of SQL 2014, so ensure that option is selected. Now select the Check and Install button in the top right.

Your system will then be checked. This should only take a minute or two.
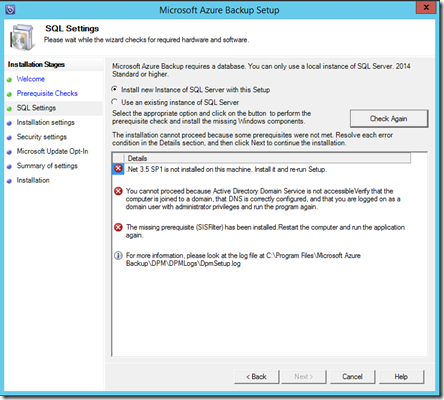
You’ll then see a report of the results. A couple of things to notice here:
– You need to install this software on a domain joined server
– You need to have .Net 3.5 SP1 installed
– You can install this software on a domain controller but if you do you’ll need to follow this guidance before proceeding:
https://technet.microsoft.com/en-us/library/ff399416.aspx

In this case the installation is on a member server and no critical issues were detected. Select Next to continue.

You’ll then be prompted to confirm your installation configuration.
Once you have made any modifications here select Next.

Now provide a password for the two accounts required to run services. Remember to record this password!
Select Next once you have entered a suitable password.

Select how you wish to manage updates and then Next to continue.
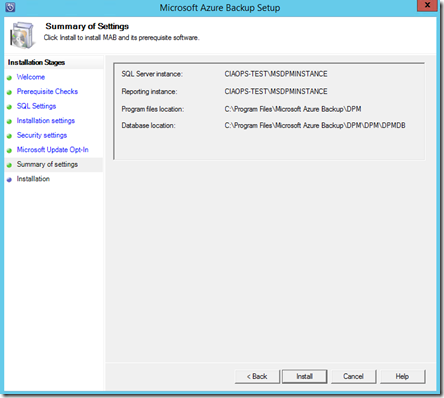
The configuration information is displayed. Select Install.
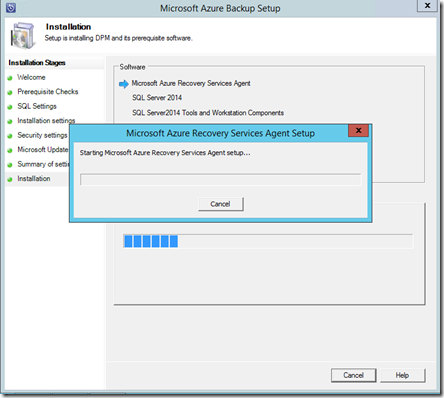
The selected software components will now be installed.

You’ll now be prompted to complete the Azure Recovery Services Agent Setup Wizard as you would with the normal Azure Backup option.
Enter any proxy details and select Next.

If additional software is required to support this agent it will be displayed.
Select Install.
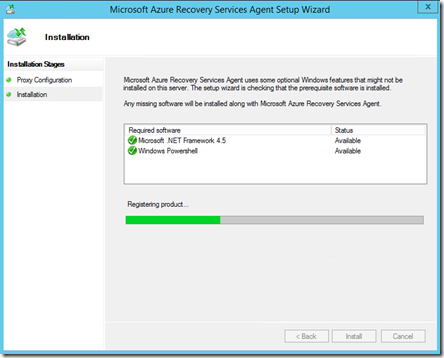
Supporting software will then be installed.

When the required supporting software has been installed select Next.

You’ll then be prompted for the location of the Vault credential file.

You download this file from the console of the Backup Vault as shown above by selecting the Download vault credentials link.

Once the vault credential file has been verified select Next.

You’ll now need to generate a unique encryption key for this backup. In most cases you will select the button Generate Passphrase to create a secure key.
You will also be prompted for a location to save a text file of this encryption key. Ensure that this key is recorded and a copy of the file is saved to another system so it can be used if recovery is required.
When all this is complete, select Next.

The installation process will continue.

You will receive a confirmation message as shown above that the process is complete.
Press the Close to complete the installation.
You should now find an icon on your desktop like that shown above for Microsoft Azure Backup Server. Double click this to launch.

The Microsoft Azure Backup console should now launch as shown above.
Here’s the Microsoft documentation on this configuration process:
Preparing to back up workloads using Azure Backup Server
I’ll look at covering how to use Azure Backup Server to backup and restore files in an upcoming post.









![[image%255B18%255D.png]](https://i0.wp.com/lh3.googleusercontent.com/-Y4P3NpptsUg/VH1WJZoooHI/AAAAAAAATSQ/K1D-PUBl118/s1600/image%25255B18%25255D.png)