In the previous parts of this series I have covered:
Office 365 Mobile MDM – Modern Device Management with Microsoft 365 Business Premium–Part 1
Intune MDM – Modern Device Management with Microsoft 365 Business Premium – Part 2
The next step in the step in the process of securing and managing devices with Microsoft 365 Business Premium is Mobile Application Management (MAM) which we’ll look at now.
MAM allows the ability to fully manage select applications, typically business applications like Outlook Mobile, Word Mobile, etc on any device. MAM is handy because it doesn’t require device management (MDM). This makes especially handy when users bring their own personal devices and want access to business data like emails but don’t want the organisation having fully control of their device. Thus, MAM is prefect for the Bring Your Own Device (BYOD) scenario.
We can thus use MAM on any device, independent of whether it is Azure AD joined, registered or stand alone.
The Intune service inside Endpoint Manager is typically what is used for MAM. Application control is once again managed by policies that are pushed down to the individual applications on the device. The first of these policies is known as App Protection policies which is focused on application security.
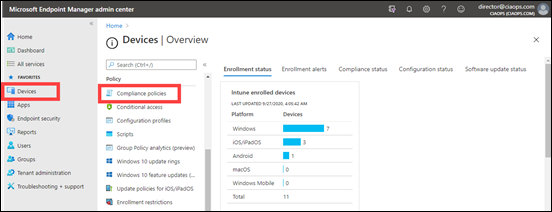
These policies are located in the Endpoint Manager portal under Apps and then App protection policies as shown above.
You can target policies to different device OS versions and here you typically define ‘targeted apps’ (i.e. corporate apps) as well any apps you want exempted from protection policies. Anything not defined by either of these is considered a non-corporate app. In here you also define corporate data locations, which will typically be Microsoft 365 services like OneDrive, SharePoint, etc but may also include on premises and third party cloud based services (say Salesforce). Now with both corporate apps and corporate data locations defined you can set policies around how data is to be stored and managed. For example, you may want to only allow corporate data to be saved to corporate locations or maybe you only want to store corporate data onto ‘secure’ devices. App protection policies allow these configurations and definitions.
App protection policies also give you the ability to selectively wipe data from corporate managed apps. MDM gives you the ability to wipe the WHOLE device remotely, both corporate and personal apps and data. MAM however, gives you the ability to just wipe the data inside Outlook mobile for example. This is why MAM is generally the best option for BYOD devices where the device owner don’t want the business to have access to anything but corporate data on the device.
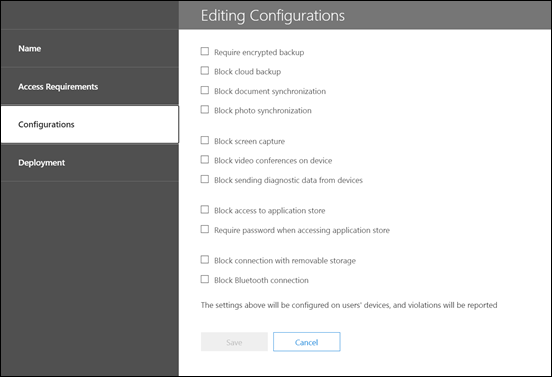
You then have Application Configuration policies as shown above which are also part of Intune MAM. These policies target the options you want configured for applications on devices.
This is again controlled by policy which can be targeted at the device OS. The above is taken from the configuration policy for Outlook for iOS and illustrates the level of detail you can go down to when configuring. You can ensure that suitably configured apps are made available to user and devices optionally or as a requirement. There is a lot that can be done here to allow you to deploy and manage applications on mobile devices.
You get to these policies via the Apps option in Endpoint Manager and then App configuration policies as shown above.
Many people ask the question about whether you should or can use MDM and MAM together? The answer is most certainly, Yes. The reason you would choose to do that is to provide extra security and convenience. MDM means for example I can ensure that my device storage is encrypted while MAM will prompt me for a pin number when I actually use a corporate app. That makes my data more secure. Do you need to use both MDM and MAM? It all depends on your security and deployment requirements. If you mainly have BYOD devices that don’t want to be device managed then MAM will be your only option. The main thing is that it provides flexibility when it comes to both security and configuration of your devices. The best strategy is defence in depth. The more layers of protection you have the lower your risk.
Given all the options that have been covered in both MDM and MAM so far, hopefully you can now see the huge amount of options available to you when it comes to managing devices. The tricks is to firstly get the device enrolled, apply MDM and then MAM policies.
Don’t think however this is the end of device options available to you. Oh no, Endpoint Manager has a many additional configuration options you can implement to make your devices EVEN more secure. Stay tuned for that upcoming article.
MOdern device Management with Microsoft 365 Business Premium – Part 4













![SNAGHTML14ccbdd9[4] SNAGHTML14ccbdd9[4]](https://ciaopsbloghome.files.wordpress.com/2020/09/snaghtml14ccbdd94_thumb.png?w=552&h=223)