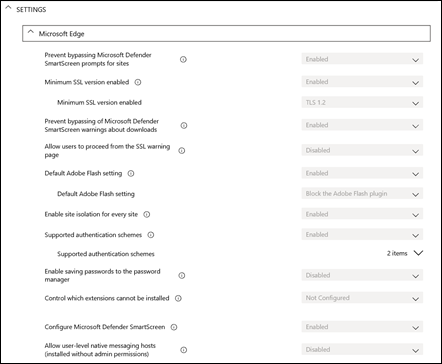
Previously, I have spoken about Cloud App Security being a ‘must have’ add on for any Microsoft 365 environment:
A great security add on for Microsoft 365
I now believe that the next ‘must have’ security add on you should integrate with your tenant is Azure Sentinel.
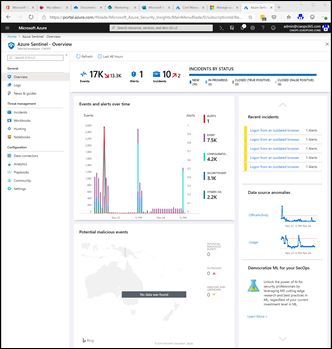
In a nutshell, Azure Sentinel will allow you to monitor, alert and report on you all you logs from just about any location, whether on prem or in the cloud.

Once you have created the Sentinel service and assigned it a log workspace, the first place to go is to the Connectors option as shown above.
Here you can connect up your services. There is a huge range of options from Office 365, Azure, on prem and third parties like AWS, At a minimum I would suggest you connect up your Azure and Office 365 services.

Next, go to the Analytics option, then select Rule templates from those available. These rules are basically queries across your data sources from your connectors. Add in the rules that make the most sense for your environment.

As you create these rules you be stepped through a wizard as shown above.

The Set rule logic step allows you to define the rule based on the data being received. You will notice there are lots of options. The great thing about using the templates is that this is already done for you but you can certainly modify these or create your own.

The real power of Azure Sentinel lies in the Automated response step shown above. Here you define what actions will be taken when a alert is generated by the rule. This means that you can have something automatically execute when an alert happen. This could be a remediation process, advanced alerting and more. This allows the response action to threat to be immediate and customisable.

Next, go into the Workbook options as shown and then the Templates area and add all the options that make sense.

A workbook is basically an interactive dashboard where you can graphically query and report on data as shown above.

When rules are triggered they will appear as Incidents that you investigate as shown above.

You’ll be able to explore incidents in greater depth using the graphical explorer as shown above.

Good security is about being pro-active and Azure Sentinel gives you this via the Hunting option as shown above. This allows you to run standard queries against the data to discover items that may need further investigation and analysis. Note the option highlighted here that allows you to Run all queries at the touch of button. This is yet another hugely powerful option as you can now ‘hunt’ across all your information so quickly. Show me another tool that can do this for both cloud and on prem?

There are lots more features, but by now you are probably wondering what the costs are? As you can see from above, they are based on storage and you can reserve a storage size to suit your needs. However, you can also opt, as I have, for a pay as you go option.

This means the Azure Sentinel cost to analyse all my data is AUD$3.99 per GB of data and

on the pay as you go plan I also need to factor in data ingestion, which is shown above in AUD$. Note that you get 5GB of data ingestion free per month. After that, I’d be paying AUD$4.586 per GB.

As you can see from the above usage figures I am no where near the 5GB ingestion limit, so all I am currently paying for just Azure Sentinel analysis.
The amount of data you ingest and analyse will depend on the services you connect and well as things like data retention periods. All of these can be adjusted to suit your needs. There are also many other Azure pricing tools you can use to control your spend. However, if you are concerned about running up an excessive bill, just connect and few services and scale from there.
In my case, I have logs from Microsoft 365 Cloud services, Azure, on premises machine monitoring, Defender ATP and more all going into Sentinel. Basically, everything I can, is going in there and the costs remain low.
I have always maintained that when you sell Microsoft 365, you should also sell an Azure subscription:
Deploy Office 365 and Azure together
Azure Sentinel is yet further confirmation that you should be doing this to add greater functionality and security to your environment. I will be spending more time deep diving into Azure Sentinel so make sure you stay tuned.