A very common request I see is people wanting to know when users have downloaded a file from SharePoint Online to their desktop. You can configure an alert to let you know when this does happen. However, I will provide a word of caution here. Remember, that alerting on this state could generate quite a number of alerts and finding the needle in that haystack can be a challenge. Thus, if you want to set these types of alerts, you should put as many filters on monitoring these activities so you don’t end up with a screen full of alerts and become overwhelmed.
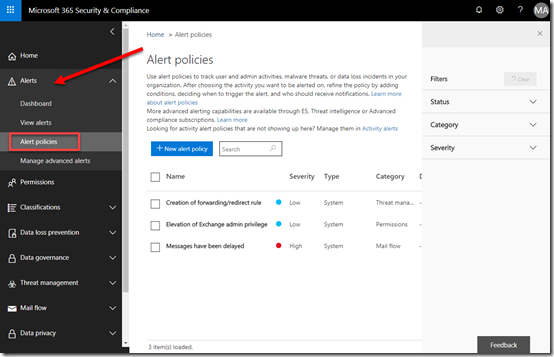
You’ll firstly need to navigate to the Security & Compliance center in the Office 365 web portal. You will also need to have the rights to do this.
Here you’ll need to expand the Alerts section on the left and then select the Alert Policies option from the items that appear.

On the right, you should see a list of the existing policies for the tenant.
Select the New alert policy button.

You’ll now be prompted to enter a Name for your policy, a Description, Severity and Category.
When complete, select the Next button at the bottom of the page.

On the next screen select the down arrow to the right of the Select an activity option to display a list of activities as shown above
Scroll down the list until you locate the Downloaded file option, which is under the File and folder activities heading, and select this.

Below this you can select the Add condition button to filter your alert. This allows you to focus the alert to:

a specific IP Address (i.e. where the user is located) and/or

a specific user account and/or

a specific filename and/or
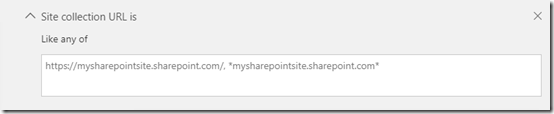
a specific site collection URL and/or

a specific file extension.
You want to take full advantage of these conditions to reduce the number of alerts you’ll receive. Thus, if you are only worried about a single user or perhaps a certain, put those conditions in now.
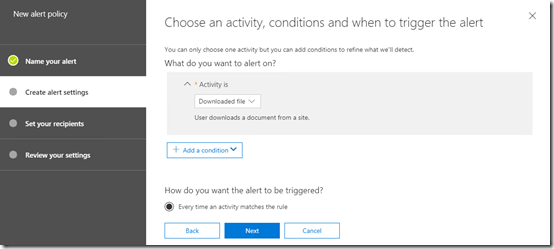
When complete, select the Next button at the bottom of the window.
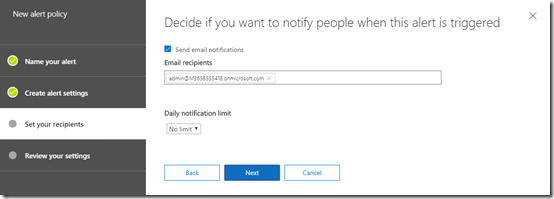
Now enter the email addresses of anyone you wish to receive notifications and ensure the Send email notifications option is set.
if you are expecting to receive lots of notifications (which is a bad idea) you may also wish to set the Daily notification limit.
Select the Next button at the bottom of the screen to continue.

Review the settings, make any changes and then select the Finish button. Generally, you will want to ensure the rule is enabled and turned on immediately.

You should now see that your policy appears in the list as shown above, and that it is enabled.
You can edit the policy simply by selecting it from this list.

Now, when a file is downloaded you should receive an email notification as shown above (assuming you have enabled email notifications of course).
You can get more details about the alert by selecting the Investigate button in the email.

Doing so will take you back to the Security & Compliance center and display the alert as shown above.
If you select the View activity list link you will get more details on the activity that triggered the alert.
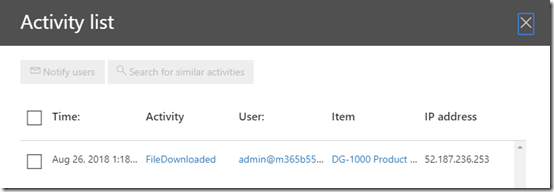
When I do this I can see the time and date, activity, users, item, IP address and so on in a list as shown above, many of which are also hyper linked so you can get more detail.

Select the Item hyperlink, you will see the above screen and in this case see that the item downloaded was a PowerPoint file for the Marketing site collection.

You can return to this list of Alerts and see this item as shown above. Throughout this process please appreciate that alerts make take a few minutes to appear in emails, notifications and lists, so be patient.
You can select the alert item to drill back into the activity of you need to at any time.

You can also change the status of the alert to help your determine what items have been resolved. Simply change the status to suit and then Save the alert. You can always view alerts by changing the filtering options on the overview page.
There are many different types of alert policies you can set here and you therefore need to judicious in how you configure these. Too many alerts is just as bad as too few alerts so ensure you make them as specific as you can to avoid overload.
You can of course always create alert and leave them disabled until you need them activated.
Remember, there are only a few system alerts configured by default in most tenants. If you want more than these, then you need to go in and configure what you need.

