A while back I made a script available that allows you to find all the external users in your environment. You can learn about this here:
Checking SharePoint External Users PowerShell Script
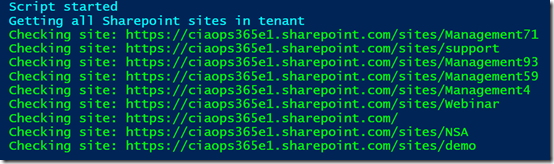
Now when I ran the script on my own tenant I noticed a number of SharePoint sites that didn’t seem right. As you can see from the above screen shot, these typically have the word “management” (e.g.management71, management93, management59, etc).
Hmm…ok, seems like I have some orphaned SharePoint sites. I kinda of remember playing around when Microsoft Teams came out, creating and deleting Teams to test the functionality. So it seems that when I deleted the Teams stuff in the early days it didn’t delete everything.
Ok, time for a clean up

So I started with site Management71 and checked to see whether I could get to it. As you can see from the above, yes I can.
So back in the day, this would have been connected to the Office 365 Group. If I delete the site and it is isn’t fully orphaned (i.e. no Office 365 Group still exists) then I could have issues. So to see whether an Office 365 Group still existed with the word “management” in the title I ran this command to give me a list of every Office 365 Group in my tenant:
Get-UnifiedGroup | Format-List DisplayName,EmailAddresses,Notes,ManagedBy,AccessType
Turns out there still is an Office 365 Group called Management in my tenant as you can see from the results below.
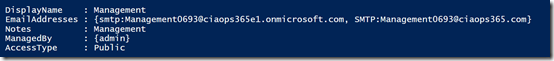
So the question now, is whether the existing Office 365 Group called Management tied to the SharePoint site Management71 or another site also with management in the name? See how confusing I’ve made things?

So next I checked whether I could discover this operational Office 365 Group I see via PowerShell and indeed I could see it in my tenant as you see above.
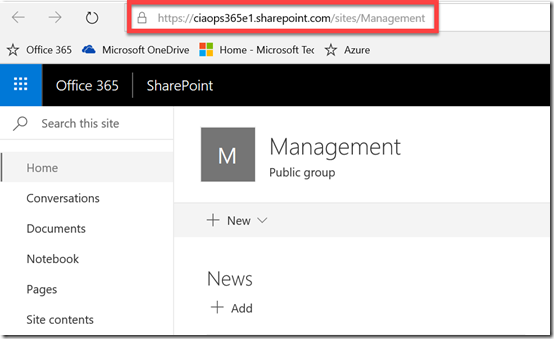
To determine whether this indeed was connected to Management71 I navigated to the SharePoint site connected to the Office 365 Group from the Group page. Low and behold, the Group Site in question is a different site, with a URL that includes the word Management not Management71. Hopefully you get why I’m trying to make all this go away!
So, not needing this valid Office 365 Group I decided the best way to remove it was to use the PowerShell command to delete it which you will find here:
Remove-UnifiedGroup -Identity "Management"
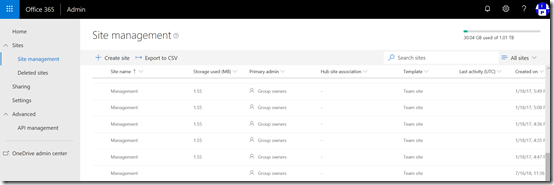
To see the sites created by Office 365 Groups you’ll need to go into the new SharePoint Online Admin console as you see above. Problem is, that this new portal doesn’t as yet allow you to delete sites. That means I’ll have to user PowerShell.
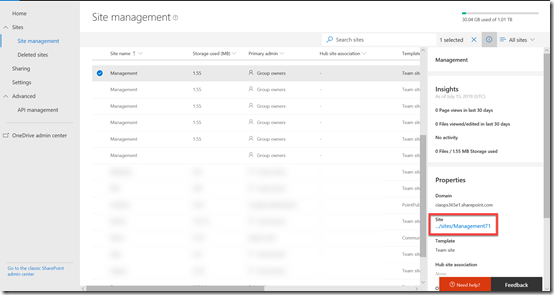
I was then able to locate the orphaned site in question – Management71 as shown above.

But if I look carefully at the properties for the site I see that it still thinks this site is connected to an Office 365 Group.

So I once again ran the PowerShell command to check the Office 365 Groups in the tenant and there is no longer one with the name management. I am therefore going to assume the site in question is orphaned and I’ll remove it using PowerShell.

When I look in the new SharePoint administration console, in the recycle bin for deleted sites I now see the site that was tied to the valid group that I just deleted called Management. To keep things tidy, I decided the best option was to purge unwanted items from here so the rogue SharePoint sites are completely gone from my tenant. To do that I ran:
remove-spodeletedsite -Identity https://ciaops365e1.sharepoint.com/sites/management –NoWait
To remove the other rogue SharePoint sites I firstly run:
remove-sposite -Identity https://ciaops365e1.sharepoint.com/sites/management71 –NoWait
Followed by the initial command to also remove them from the recycle bin and my tenant completely.
In the end, I have been able to remove active SharePoint sites in my tenant that appear to have been created by now defunct Office 365 Groups. I did all this via PowerShell to ensure that they weren’t still connected to something else in Office 365.
I feel much better have a clean tenant without these additional SharePoint sites float around and I got to also user PowerShell to get the job done. Win!