This is part of a series of articles about email security in Microsoft 365. Please check out previous articles here:
End to End email protection with Microsoft 365 – Part 1
End to End email protection with Microsoft 365 – Part 2

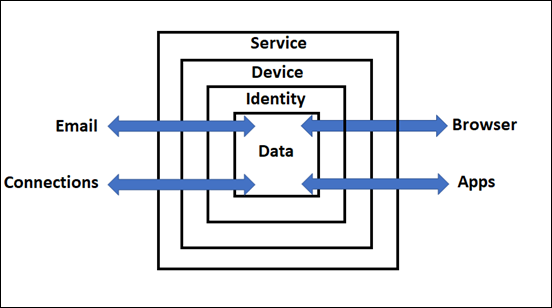
These articles are based on a model I have previously created, which you can read about here:
designed to help better explain expansive security included with Microsoft 365.
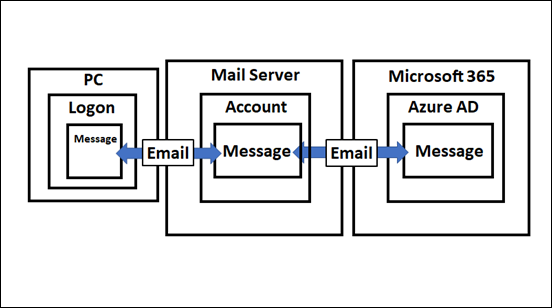
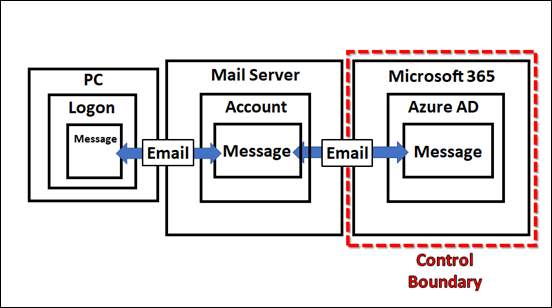
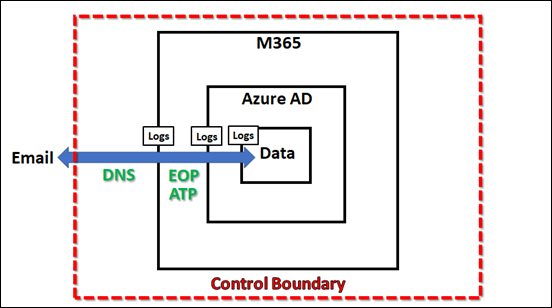
So far, email has travelled from ‘somewhere’ on the Internet (outside the service) through various layers of protection, which I have already spoken about previously. It has now finally come to ‘rest’ in the data container inside the Service (Microsoft 365) as shown above. However, even at ‘rest’, data is still protected thanks to the capabilities in Microsoft 365.
Remember, that as yet, there has been no user interaction with the data so far. The email has simply been delivered to the users inbox awaiting them to log in and view it.
While the email sits inside the data container in Microsoft 365, protection is being provided by Zero Hour Purge (ZAP). As Microsoft says:
In Microsoft 365 organizations with mailboxes in Exchange Online, zero-hour auto purge (ZAP) is an email protection feature that retroactively detects and neutralizes malicious phishing, spam, or malware messages that have already been delivered to Exchange Online mailboxes.
which you can read more on here:
Zero-hour auto purge (ZAP) in Exchange Online
This means that even after an email is delivered to a users inbox it is constantly being monitored as to whether it is phishing, malware, spam or something otherwise nefarious. If it is detected as such, then appropriate action is taken. Such action can be determined by an administrator during configuration things like spam policies per:
Use the Security & Compliance Center to create anti-spam policies
So this means that not only does Microsoft 365 scan inbound and outbound emails as they pass through the service, they continue to scan all emails once delivered thanks to the fact that they reside inside the actual Microsoft 365 service at all times. This is a big benefit over third party scanning services that only do so as the email passes through their filters, no inside the actual inbox.
You can therefore rest assured that if a malicious email is detected at any stage in Microsoft 365, and assuming you have enabled ZAP, you’ll be protected.
While sitting on servers in Microsoft data centers all sorts of additional protections are in place such as being encrypted at rest:
Encryption in the Microsoft cloud
Encryption Risks and Protections
In addition to using volume-level encryption, Exchange Online, Skype for Business, SharePoint Online, and OneDrive for Business also use Service Encryption to encrypt customer data per:
The best reference for all the extensive Microsoft cloud protections is the:
You also might want to take a look at virtual tour of a Microsoft datacenter:
Take a guided tour of a Microsoft datacenter to learn how Microsoft delivers your cloud services
and read about how Microsoft meshes all these datacenters together to provide the Microsoft 365 service:
Azure facilities, premises, and physical security
Hopefully now you are comfortable with the fact that the protection Microsoft 365 provides for your inbound email data (as well as all your other data) is rigorous, from the moment that it enters the Microsoft 365 service until it sits ready for a user to interact with it.
The next stage in the journey will be for a device (i.e. PC) to connect to the Microsoft 365 service and then for a user to log into that device and run an app, like Outlook, to read the delivered email. Spoiler alert – there is even more protection involved here and I’ll start covering that in upcoming articles, so stay tuned for a closer look at what happens during user interaction with the data inside Microsoft 365.