Important: Mailbox Auditing is Already ON by Default
Good news! Since 2019, Microsoft automatically enables mailbox auditing for all Exchange Online organizations. This means logging is already active for your mailboxes without requiring any manual configuration.
Should You Enable All Available Logging?
No, you should NOT enable all available logging. Here’s why:
- Microsoft’s Recommendation: Use the default audit configuration, which Microsoft automatically manages and updates
- Storage Impact: Audit logs consume storage space in each mailbox’s Recoverable Items folder (counts against the 30GB default limit)
- Performance Consideration: Excessive logging can impact mailbox performance
- Automatic Updates: Microsoft automatically adds new important actions to the default audit configuration as they’re released
What’s Logged by Default
The default configuration logs these critical actions:
| Action | Admin | Delegate | Owner |
|---|---|---|---|
| Create (Calendar items) | ✓ | ✓ | |
| HardDelete | ✓ | ✓ | ✓ |
| MoveToDeletedItems | ✓ | ✓ | ✓ |
| SendAs | ✓ | ✓ | |
| SendOnBehalf | ✓ | ✓ | |
| SoftDelete | ✓ | ✓ | ✓ |
| Update | ✓ | ✓ | ✓ |
| UpdateFolderPermissions | ✓ | ✓ | ✓ |
| UpdateInboxRules | ✓ | ✓ | ✓ |
Step-by-Step Configuration Guide
Method 1: PowerShell (Recommended)
Step 1: Connect to Exchange Online PowerShell
Install-Module -Name ExchangeOnlineManagement
Connect-ExchangeOnline -UserPrincipalName admin@yourdomain.com
Step 2: Verify Organization-Wide Auditing is Enabled
Get-OrganizationConfig | Format-List AuditDisabled
Result should show False (meaning auditing is enabled)
Step 3: Check Current Mailbox Audit Status
# For a specific mailbox
Get-Mailbox -Identity "user@domain.com" | Format-List Name,AuditEnabled,DefaultAuditSet
# For all mailboxes
Get-Mailbox -ResultSize Unlimited | Format-Table Name,AuditEnabled,DefaultAuditSet
Step 4: Use Default Settings (Recommended)
# Restore default auditing for a mailbox that was customized
Set-Mailbox -Identity "user@domain.com" -DefaultAuditSet Admin,Delegate,Owner
Step 5: Only If Necessary – Customize Specific Actions
# Example: Add MailboxLogin tracking for owner actions
Set-Mailbox -Identity "user@domain.com" -AuditOwner @{Add="MailboxLogin"}
# Example: Set specific admin actions (overwrites defaults - not recommended)
Set-Mailbox -Identity "user@domain.com" -AuditAdmin MessageBind,FolderBind,HardDelete
Step 6: Configure Retention Period
# Default is 90 days, can extend up to 365 days (E5 license required for >180 days)
Set-Mailbox -Identity "user@domain.com" -AuditLogAgeLimit 180
# Apply to all mailboxes
Get-Mailbox -ResultSize Unlimited | Set-Mailbox -AuditLogAgeLimit 180
Step 7: Verify Configuration
# Check what actions are being audited
Get-Mailbox -Identity "user@domain.com" | Select-Object -ExpandProperty AuditAdmin
Get-Mailbox -Identity "user@domain.com" | Select-Object -ExpandProperty AuditDelegate
Get-Mailbox -Identity "user@domain.com" | Select-Object -ExpandProperty AuditOwner
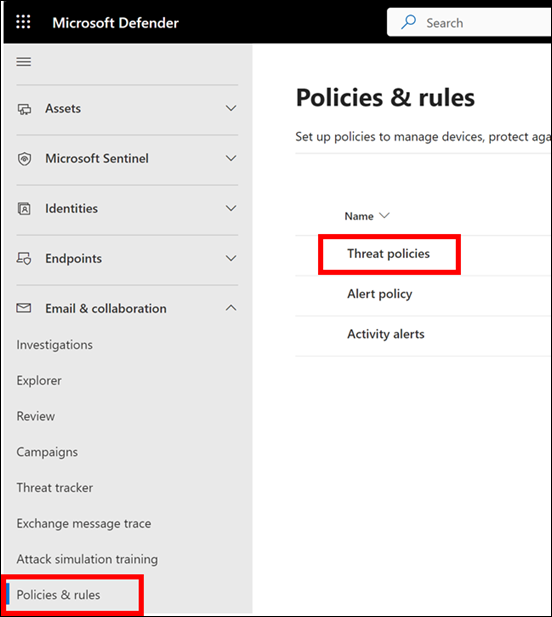
Method 2: Microsoft 365 Admin Center (Limited Options)
Note: The GUI provides limited mailbox audit configuration options. Most settings require PowerShell.
To Search Audit Logs via GUI:
- Navigate to Microsoft Purview compliance portal
- Go to Audit in the left navigation
- Ensure audit log search is turned on (banner will appear if it’s not)
- Use the search interface to query audit logs
- Filter by:
- Activities (e.g., “Mailbox activities”)
- Date range
- Users
- File, folder, or site
- Export results as needed
To Export Mailbox Audit Logs via Classic EAC:
- Navigate to the Classic Exchange Admin Center
- Go to Compliance Management → Auditing
- Click “Export mailbox audit logs”
- Specify date range and recipients
- Submit the export request
Best Practices Summary
- Keep default auditing enabled – It’s already on and Microsoft manages it
- Don’t enable all actions – Avoid FolderBind and MessageBind for owners (creates excessive logs)
- Retention considerations:
- Standard licenses: 180 days retention
- E5 licenses: 1 year retention by default
- 10-year retention available with additional licensing
- Monitor storage: Check Recoverable Items folder size periodically
- Use PowerShell for configuration: GUI options are limited
- Test before mass deployment: If customizing, test on pilot mailboxes first
When to Customize Auditing
Only customize mailbox auditing if you have specific compliance requirements such as:
- Regulatory requirements for specific action tracking
- Security investigation needs
- Tracking mailbox login events (MailboxLogin)
- Monitoring specific delegate activities
Understanding FolderBind and MessageBind Logging for Mailbox Owners
What FolderBind and MessageBind Actually Log
FolderBind
What it logs: Every time a mailbox folder is accessed or opened
- Records when someone navigates to or opens any folder (Inbox, Sent Items, Deleted Items, custom folders, etc.)
- Captures the folder GUID and path
- Logs the timestamp, client IP address, and application used
- For delegates, entries are consolidated (one record per folder per 24-hour period to reduce volume)
- Important: Not consolidated for owners – every folder access creates a separate log entry
MessageBind
What it logs: Every time a message is viewed in the preview pane or opened
- Records when someone reads or opens an individual email message
- Captures the message subject and ItemID
- Logs whether the message was previewed or fully opened
- Records the client application and IP address
- Note: For E5 licensed users, this is replaced by the more sophisticated MailItemsAccessed action
Why These Actions Are NOT Enabled for Owners by Default
1. Massive Log Volume
The Reality: A typical user might:
- Access 20-50 folders per day during normal email activity
- View 50-200+ messages daily
- Generate thousands of audit entries weekly
- Create up to 100,000+ audit entries annually per mailbox
2. Storage Impact
- Audit logs are stored in the mailbox’s Recoverable Items folder (Audits subfolder)
- Count against the 30GB default quota (or 100GB with holds)
- Maximum 3 million items can be stored in the Audits subfolder
- Heavy users could hit these limits within months
3. Performance Considerations
- Every folder navigation and message view triggers a write operation
- Can impact mailbox performance, especially for heavy email users
- Increases server-side processing load
- May slow down email client responsiveness
4. Signal-to-Noise Ratio
- 99.9% of owner FolderBind/MessageBind events are legitimate daily activity
- Makes it extremely difficult to identify suspicious activity
- Investigation tools often filter out FolderBind by default because of the noise
Legitimate Scenarios for Enabling FolderBind/MessageBind for Owners
1. Insider Threat Detection
Use Case: Monitoring high-risk individuals or sensitive roles
- Executives with access to M&A information
- Employees on performance improvement plans or termination notice
- Users with access to intellectual property or trade secrets
- Detecting unusual access patterns (e.g., accessing old emails before resignation)
2. Compliance Requirements
Use Case: Specific regulatory mandates
- Financial services requiring complete audit trails (SEC, FINRA)
- Healthcare organizations tracking PHI access (HIPAA)
- Government contractors with security clearance requirements
- Legal hold scenarios requiring complete activity documentation
3. Forensic Investigations
Use Case: Post-incident analysis
- Determining if a compromised account’s emails were actually read
- Investigating data exfiltration attempts
- Proving or disproving unauthorized access claims
- Building timeline of activities during security incidents
4. Privileged Account Monitoring
Use Case: Enhanced monitoring for administrative accounts
- Service accounts that shouldn’t have regular email activity
- Shared mailboxes with sensitive information
- Discovery mailboxes used for legal searches
- Executive assistant mailboxes with delegated access
Best Practices If You Enable FolderBind/MessageBind for Owners
1. Selective Implementation
# Enable only for specific high-risk mailboxes
Set-Mailbox -Identity "CEO@company.com" -AuditOwner @{Add="FolderBind","MessageBind"}
# Create a list of VIP users
$VIPUsers = "CEO@company.com","CFO@company.com","Legal@company.com"
foreach ($user in $VIPUsers) {
Set-Mailbox -Identity $user -AuditOwner @{Add="FolderBind","MessageBind"}
}
2. Increase Retention Period
# Extend audit log retention to accommodate increased volume
Set-Mailbox -Identity "CEO@company.com" -AuditLogAgeLimit 365
3. Monitor Storage Impact
# Check audit folder size regularly
Get-MailboxFolderStatistics -Identity "CEO@company.com" -FolderScope RecoverableItems |
Where-Object {$_.Name -eq 'Audits'} |
Format-List FolderPath,FolderSize,ItemsInFolder
4. Implement Automated Analysis
- Export logs to SIEM systems for pattern analysis
- Set up alerts for unusual access patterns
- Use machine learning to baseline normal behavior
- Focus on deviations from typical patterns
5. Consider Alternative Solutions
- For E5 Users: Use MailItemsAccessed instead (more intelligent, less noisy)
- Microsoft Defender: Use insider risk management policies
- Third-party tools: Consider specialized insider threat detection solutions
- DLP policies: Focus on preventing data loss rather than tracking all access
The MailItemsAccessed Alternative (E5 Licenses)
For organizations with E5 licenses, MailItemsAccessed is a superior alternative that:
- Intelligently aggregates similar activities (reduces noise by 80-90%)
- Provides both sync and bind operation tracking
- Includes deduplication (removes duplicate entries within 1-hour windows)
- Records InternetMessageId for precise message tracking
- Better suited for forensic investigations
- Automatically enabled for E5 users
Summary Recommendation
Enable FolderBind/MessageBind for owners ONLY when:
- You have specific compliance or security requirements
- Monitoring high-risk individuals or during investigations
- You have the resources to analyze the massive data volume
- Storage and performance impacts have been evaluated
- You’ve implemented automated analysis tools
Otherwise: Stick with the default configuration and use alternative methods like DLP policies, insider risk management, and the MailItemsAccessed action (for E5 users) for more effective security monitoring.