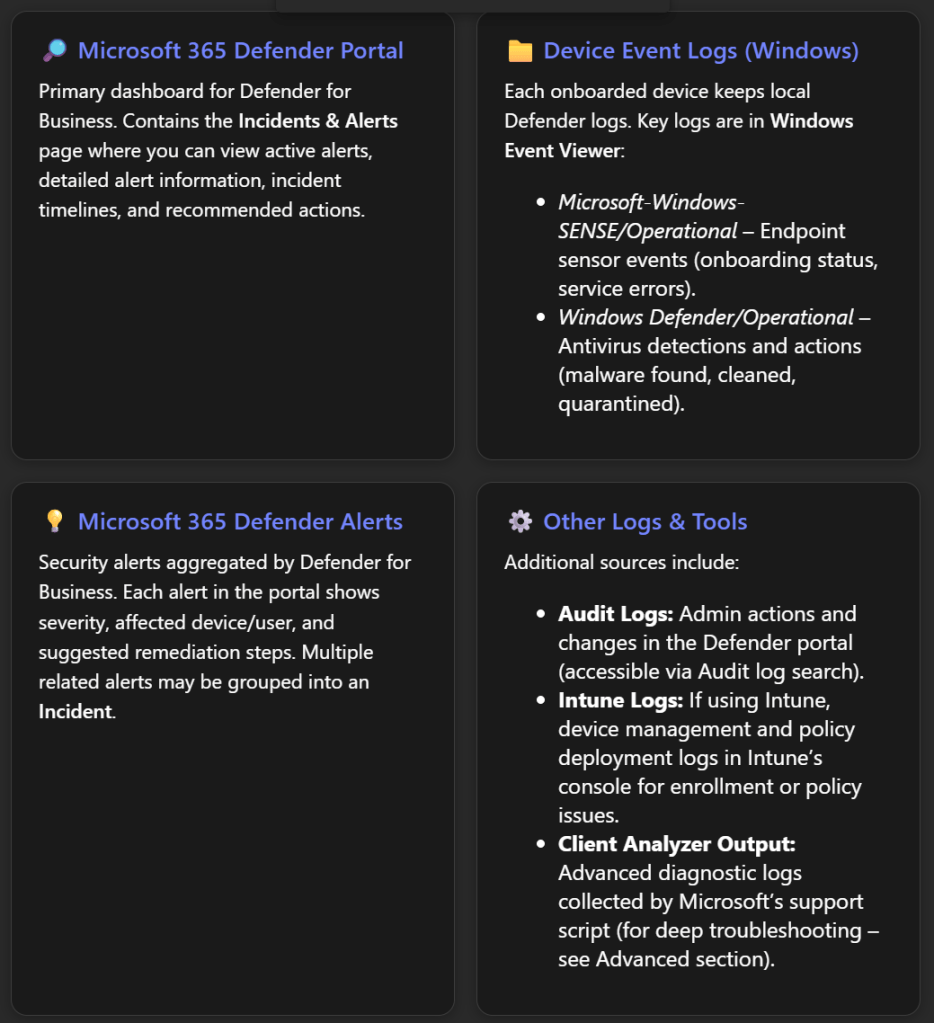
1. What is Automated Response in Cybersecurity?
Automated incident response refers to using software and tools (often powered by AI and machine learning) to automatically detect, investigate, and respond to security incidents with minimal human intervention[11]. Instead of waiting for a security analyst to triage an alert, an automated system can take immediate action – for example, isolating an infected device or quarantining a malicious file – according to predefined rules. This approach ensures faster, consistent responses to threats, helping contain attacks before they spread. In practice, automated response systems continuously analyze data from endpoints, emails, identities, etc., to recognize malicious patterns and then execute remediation steps (like killing processes, blocking IPs, or removing malware) in real time[11]. By reducing manual effort and human error, automation has become a backbone of modern cybersecurity defense, enabling even small IT teams to handle large volumes of alerts quickly and uniformly.
2. Automated Response Features in Microsoft Defender for Business
Microsoft Defender for Business (MDB) – included with Microsoft 365 Business Premium – provides enterprise-grade automated response capabilities tailored to small and medium businesses. Key features include:
-
Automated Investigation & Remediation (AIR): Defender for Business will automatically investigate alerts and remediate threats across your endpoints. When malware or suspicious behavior is detected, the system initiates an automated investigation – gathering logs, analyzing affected entities, and determining the scope of the threat. It then takes immediate action to contain and neutralize the threat, often without needing admin approval[9][7]. This means that common attacks (like virus infections or ransomware behaviors) are shut down quickly – Defender can kill malicious processes, isolate the device from the network, or quarantine harmful files on its own.
-
Endpoint Detection and Response (EDR) with AI-Powered Automation: Defender for Business includes an EDR component that uses behavior monitoring and cloud-based AI to detect advanced threats. Unusual patterns (e.g. a legitimate process spawning a script to download unknown software) trigger alerts which the system can auto-investigate. 24×7 automated responses mimic the steps a skilled analyst would take, but at machine speed[7]. For example, if a suspected memory-based attack is encountered, Defender for Business will analyze running processes and memory, then automatically apply actions like terminating processes or rolling back changes.
-
Automatic Attack Disruption: Microsoft has built in automated attack disruption specifically to combat rapid threats like ransomware. Defender for Business can in real time detect ransomware encryption activity and automatically isolate that endpoint or stop the encryption process, effectively halting an in-progress attack without waiting for human input[8]. This capability brings down response times to seconds, greatly limiting damage.
-
Out-of-the-Box Policies and Cloud Intelligence: Upon deployment, Defender for Business comes with pre-configured security policies that enable a baseline of protection and automated actions[8]. These policies (which can be customized) govern what remediation actions to take. Under the hood, the solution leverages Microsoft’s vast threat intelligence – the same cloud-based AI and global threat data used in enterprise Microsoft Defender – so it can automatically identify new malware or attacker techniques and respond appropriately[8].
Overall, Defender for Business is designed so that many routine threats are handled automatically, reducing the number of alerts administrators must deal with manually. Microsoft reports that it can “automatically resolve most cyberthreats” on devices using these capabilities[8].
3. Comparison with Other Antivirus Solutions’ Automated Response
Microsoft Defender for Business goes beyond traditional antivirus solutions by incorporating these automated EDR and remediation features. Traditional third-party antivirus products for SMBs have typically focused on malware detection (often signature-based) and basic cleanup, with limited ability to automatically investigate wider threats or coordinate with identity/email signals. In contrast, Defender for Business offers multi-layered protection (AV + EDR + AIR) similar to enterprise-grade systems[2].
Some points of comparison:
-
Integration and Signal Sharing: Defender for Business is natively integrated with the Microsoft 365 ecosystem (Azure AD identities, Office 365 email, etc.). It shares threat signals across endpoints, email, and identities, all visible in one security dashboard. A third-party antivirus usually has a separate console and does not automatically share intelligence with Microsoft 365 services[8]. For example, if a user’s account is compromised and then that user’s machine shows malware, Microsoft’s tools correlate those events; a standalone AV might miss that bigger picture.
-
EDR & Automated Remediation: Many leading third-party endpoint security products now offer their own EDR and automation, but often as add-ons or higher-tier packages, and not as deeply tied into your IT environment. Defender for Business includes EDR with automated response by default. Notably, Microsoft’s automated remediation can work in tandem with Office 365 threat protection – e.g. an email-born threat that lands on a device can trigger device remediation and also retroactively delete phishing emails. Competing AVs lack this cross-product automation unless you invest in a broader XDR platform from that vendor. By default, a non-Microsoft AV will quarantine a file, but it won’t isolate an Azure AD user or trigger an alert in Office 365 because those systems are separate.
-
Single Pane of Glass: With Defender for Business, admins use the unified Microsoft 365 Defender portal to manage alerts and automated actions across all security domains (endpoint, email, identity). Many third-party solutions require you to monitor a separate portal for endpoint incidents. This separation can slow down response – e.g. your IT staff might clear a malware alert in the AV console but be unaware of related suspicious sign-ins noted in Azure AD. Microsoft’s integration means automated responses are part of a cohesive incident story visible in one place[10].
-
Breadth of Protection: Traditional antiviruses rely mainly on known-malware signatures and perhaps some heuristic or behavior checks. Defender for Business uses cloud-powered AI models and looks at a wide variety of behavior telemetry (process execution, script behavior, memory indicators, etc.). This allows it to act on more sophisticated attacks automatically. Third-party SMB suites might not have an equivalent to Microsoft’s cloud ML, or if they do, they might generate alerts that still require manual handling. In summary, Defender’s automated response is more holistic, leveraging a wide array of data (thanks to integration with Microsoft 365) and acting across prevention, detection, and response stages. Many standalone AV solutions provide excellent virus removal, but they “leave businesses vulnerable to unknown cyberthreats… attackers who can evade detection,” whereas Defender’s approach is to catch those unknowns using behavioral AI and then respond automatically[8].
(It’s worth noting that some dedicated security vendors (e.g. CrowdStrike, Sophos, etc.) do offer strong EDR for SMBs. However, those typically come at extra cost and still may not integrate as seamlessly with your Microsoft cloud environment.)
4. Examples and Case Studies of Automated Response in Action
It’s helpful to see how Defender for Business’ automated response works in real scenarios:
-
Example 1 – Malware Quarantine: One small business IT provider reported a case where a client’s nightly website backup file was found to contain malware. With Defender for Business in place, as soon as the backup was created and scanned, Defender automatically flagged the malware and quarantined the file – no admin needed to intervene[9]. An automated investigation kicked off, which checked the system for any other related threats. Because the malware hadn’t executed yet (it was caught in the backup file), the tool simply contained it and marked the incident as resolved. The IT admin received a notification of what happened, along with details in the portal of what was found and what actions were taken. In a traditional AV scenario, that malware might have sat unnoticed until an admin review or – worse – been restored later and executed. Defender’s automation prevented a potential incident proactively.
-
Example 2 – Ransomware Attack Disruption: Imagine a user inadvertently runs a trojan that starts encrypting files (a typical ransomware behavior). Microsoft Defender for Business will detect the encryption activity as malicious (through its behavior analytics). Immediately, it can isolate the machine from the network and terminate the ransomware process – all automatically[8]. It might also roll back changes if possible (leveraging Volume Shadow Copy). On the admin side, an “incident” is generated showing that “Ransomware behavior was detected and blocked; device isolated.” The security team can then use the portal to further investigate how that ransomware got in. Microsoft has demonstrated that its automated attack disruption can stop ransomware in early stages to limit damage. Many SMB-focused AV products do not have this level of automated containment; they might detect the malicious file but not before some encryption has occurred. In tests, Defender can respond in real-time, often faster than an IT team’s manual actions.
-
Example 3 – Malicious Process Removal: Microsoft provides an example of how Defender for Business mimics a security analyst. If a malicious process is discovered on a device, Defender will automatically “restrict its code execution and remove persistence mechanisms (like registry keys that would allow it to restart)”[7]. In one case, a cryptomining malware was detected on a PC. Defender automatically stopped the running malicious process, removed its scheduled task (which would have relaunched it), and deleted the dropped files. It did this within minutes, and the user only noticed a brief slowdown. The admin portal showed an incident with the verdict that a cryptominer was cleaned and no further action was needed. This showcases that Defender doesn’t just flag threats – it takes the same remediation steps a human would do (kill process, delete autoruns, etc.), but faster[7].
These examples illustrate how Defender for Business reduces the impact of attacks by reacting immediately. In each case, automated actions addressed the threat before IT staff could even triage it, allowing the business to continue with minimal interruption. That said, all actions are logged and visible, so admins retain oversight and can investigate deeper if needed after the fact.
5. User Reviews and Expert Opinions on Effectiveness
Microsoft Defender for Business has garnered positive feedback from industry experts and IT professionals, particularly for bringing advanced capabilities to the SMB segment in an easy package:
-
TechRadar Review (Sept 2023): “Microsoft Defender for Business is designed to offer protection above and beyond traditional antivirus, such as automated protection and response for up to 300 users… The tech giant is uniquely placed to offer the best endpoint protection.”[2]. The review highlighted that it’s reasonably priced and easy to navigate, noting that Microsoft’s experience with enterprise security trickles down to this product. The inclusion of automated response was seen as a major plus that differentiates it from basic AV solutions.
-
MSP/IT Pro Community: Many Managed Service Providers appreciate the value for small clients. For instance, Alex Fields, a Microsoft MVP and MSP owner, noted Defender for Business has a “fantastic feature set, given that it’s included with Business Premium (widely considered the Gold Standard SKU for SMBs)”[6]. This sentiment underlines that features like EDR and automated remediation – which used to require expensive enterprise tools – are now available to small businesses at no extra cost, a game-changer in value.
-
User Feedback: On G2 and other review platforms, users often mention that the integration and automation simplify their security management. One G2 reviewer (an MSP) wrote that they “highly recommend Microsoft Defender for Business. This exceptional security solution provides comprehensive protection… Automated investigation and remediation is huge [because] it’s happening in the background, making our security simple.” This aligns with statements from case studies – for example, Adam Atwell, a Cloud Solutions Architect at Kite Technology Group, said “Automated investigation and remediation is a huge part… it’s just happening in the background. Microsoft Defender for Business makes our security so simple.”[12]
-
Independent Rankings: Microsoft’s Defender technology (the same engine behind Defender for Business) is consistently top-ranked in independent antivirus tests for protection. It often earns perfect or near-perfect scores in AV-Test evaluations and is named a Leader in Gartner and Forrester reports[6]. This gives admins confidence that the automated actions are backed by reliable threat detection capabilities.
In summary, experts praise Defender for Business for bringing enterprise-level automated security to smaller organizations in a cost-effective way. The common theme in reviews is that it significantly reduces the workload on IT teams by handling threats automatically, and does so using Microsoft’s highly-rated security tech. Any criticism tends to be around initial setup complexity (integrating with existing environments) or learning curve, but once running, the effectiveness of its automated defense is well-regarded.
6. Licensing and Upgrades for Full Automated Response
One of the advantages of Defender for Business is that it already includes automated response features out-of-the-box – you do not need to purchase an extra license to get basic AIR (Automated Investigation and Response) capabilities. Microsoft Defender for Business is available as a standalone ($3 per user/month) and is included at no extra cost in Microsoft 365 Business Premium subscriptions[2]. This means if you have Business Premium, you automatically have Defender for Business (which equates roughly to “Defender for Endpoint Plan 1 plus additional SMB enhancements” in Microsoft’s product lineup).
However, Microsoft’s Defender ecosystem has another tier known as Defender for Endpoint Plan 2 (P2), which is part of enterprise E5 licenses or can be purchased as an add-on. Plan 2 is the full-featured endpoint security suite that large enterprises use. The key difference: Plan 2 includes some advanced features that Defender for Business lacks, such as threat hunting (advanced search of 6 months of data via queries), more granular device timelines, and automated response in more complex scenarios. Defender for Business’ feature set sits between Plan 1 and Plan 2[5]:
-
Defender for Endpoint Plan 1: Core next-gen antivirus only (no EDR, no automated investigation). This is a more limited offering mostly focusing on prevention.
-
Defender for Business: Includes next-gen AV plus EDR with automated investigation & response. Microsoft optimized some features for SMB ease-of-use – for instance, it lacks the advanced hunting query interface and some detailed forensic data that Plan 2 offers, but it does have the same automated remediation engine working on alerts[5]. In essence, MDB does perform automated response for most endpoint threats (malware, suspicious behaviors, etc.) but you may not have the ability to hunt for subtle threats proactively via queries.
-
Defender for Endpoint Plan 2: Full EDR suite – includes everything in Defender for Business, plus advanced hunting, longer data retention, threat analytics, and more automation options. Notably, Plan 2 is required for certain high-end capabilities like Microsoft Threat Experts (a human analyst alerting service) or custom threat hunting rules.
Do you need Plan 2 for “full” automated response? For most SMB scenarios, Defender for Business is sufficient – it will automatically remediate most threats on endpoints without additional licensing. Microsoft has explicitly included automated investigation/remediation in Business Premium’s Defender[8]. However, if an organization wants the more advanced, proactive end of the spectrum (writing custom detection rules, performing deep KQL query hunts on historical data, etc.), or needs integration into a broader enterprise SOC workflow, an upgrade to Plan 2 might be considered. An upgrade could be achieved by moving to Microsoft 365 E5 or by buying a Defender for Endpoint P2 standalone license for those devices/users.
To summarize licensing: Microsoft Defender for Business already gives you automated response as part of the package – there’s no need to pay extra for basic to intermediate level endpoint automation. The upgrade to P2 is only necessary if you require advanced threat hunting, extended incident data, and richer automated playbooks that go beyond the scope of what’s provided to SMB customers[5]. Many businesses up to 300 employees will find Business Premium’s included Defender quite robust. Those that outgrow it (in terms of security operations maturity) can step up to the enterprise license.
(Important note: Microsoft Defender for Office 365 (for email) also has Plan 1 vs Plan 2 differences in automation. But for endpoint “Defender for Business” vs “Defender for Endpoint P2”, the above applies.)
7. Integration with Other Microsoft 365 Services
One of the strongest points of Defender for Business is its tight integration with other Microsoft 365 services. This integration amplifies automated response capabilities and simplifies administration:
-
Azure AD and Identities: Defender for Business is integrated with Azure Active Directory (Entra ID), using your existing user identities and device enrollments. This means any device or alert is automatically associated with a user from your Azure AD. Actions taken by Defender (like isolating a device or detecting a compromised user token) can feed into Azure AD Conditional Access policies. For instance, if a device is flagged as high risk by Defender, Azure AD Conditional Access can automatically block that device from accessing cloud apps. All of this happens through native integration – no custom setup needed – because Microsoft 365 Defender coordinates across identities, endpoints, cloud apps, and email natively[10].
-
Intune (Endpoint Manager): Deployment and policy management for Defender for Business are done via Microsoft Intune (for Business Premium customers) or the Defender portal. Since Intune is included in Business Premium, many organizations use it to configure onboarding of devices. Defender for Business can use Intune to distribute its settings and ensure every enrolled device has the proper Defender configurations. There’s no separate agent to deploy on Windows 10/11 – it uses the built-in Defender sensor, which Intune can activate and manage[9]. This contrasts with third-party solutions where you must install and update a separate agent on each device.
-
Microsoft 365 Defender (XDR) Portal: All the incident data from Defender for Business surfaces in the Microsoft 365 Defender portal (security.microsoft.com), which is the same interface that houses alerts from Office 365 (email/phish), Azure AD Identity Protection, Cloud App Security, etc. This unified portal means an admin can see, for example, that a malicious email was received by a user, the user clicked a link, and then Defender for Business isolated that user’s device due to the resulting malware. The incident is correlated across workloads. In a single view, you get information from Defender for Office 365, Defender for Identity, and Defender for Business. This integration vastly improves understanding the full story of an attack and ensures that automated responses are part of a bigger coordinated defense. Security teams don’t have to swivel-chair between an AV console and an email security console – it’s all in one dashboard with cross-references[3].
-
Secure Score and Compliance: Because it’s integrated with M365, Defender for Business feeds into your organization’s Microsoft Secure Score (a measure of security posture) with recommendations. It also works with the compliance center – all Defender actions and alerts can be audited through the unified audit log. If you need to demonstrate to auditors that threats are being handled, you can pull reports from the compliance portal that include Defender’s automated remediation actions (e.g., “malware X quarantined on device Y at time Z by automated system”). Additionally, Microsoft’s cloud (including Defender for Business) meets various compliance standards (FedRAMP, GDPR, etc.), which can be important for regulated industries[8]. Using the built-in solution can simplify compliance reporting since you’re using a pre-approved security control set.
-
Power Platform and SIEM Integration: Advanced users can integrate Defender for Business with Power Automate or SIEM systems via APIs and the upcoming Streaming API. For example, an alert from Defender could trigger a Power Automate flow to notify an IT channel or create a ticket. And because it’s all cloud-based, exporting events to Microsoft Sentinel (Azure SIEM) or other SIEM tools is supported, enabling a holistic security operations workflow. Microsoft has a streaming API in preview that streams Defender for Business events to Azure Event Hubs for SIEM ingestion[2], which is rarely possible with basic standalone antivirus products.
In essence, Defender for Business doesn’t operate in a silo – it’s part of an ecosystem of Microsoft 365 security. When an issue arises, automated response might involve multiple parts of that ecosystem (for example, disabling an account in Azure AD and cleaning a device, all coordinated). This is a major benefit over third-party solutions, which might protect an endpoint well but can’t natively orchestrate actions on user accounts, email quarantine, or SharePoint files. Defender for Business, being a component of Microsoft 365’s XDR (extended detection and response) suite, provides joined-up defenses across your cloud and endpoint environment.
8. Impact on System Performance
A common concern with endpoint security solutions is performance impact on devices. Microsoft Defender for Business is designed and optimized for Windows at its core, since it uses the built-in Defender engine on Windows 10/11. Microsoft has worked to ensure that the real-time protection and automated actions run efficiently in the background with minimal user disruption:
-
Lightweight Footprint: Because the Defender antivirus is built into Windows, running it doesn’t require loading a heavy third-party service; it’s part of the OS security stack. It uses smart caching and cloud lookups to avoid excessive CPU usage. Most routine scans and updates occur when the system is idle. In fact, Windows Defender AV (which Defender for Business builds upon) receives updates as part of regular Windows Updates – these incremental updates are typically small and quick[4]. This means there isn’t a separate bulky update mechanism hogging bandwidth or CPU; it’s streamlined with Windows’ own updating process.
-
Performance in Practice: Modern independent tests show Microsoft Defender Antivirus to be competitive in performance with other top antiviruses. In AV-Test’s evaluations, for example, Microsoft Defender often scores the maximum 6 points in performance or only slightly below top performers. It’s generally recognized as “lightweight for most use cases” in recent years (a notable improvement from a decade ago). There can be particular operations (like the very first full disk scan, or heavy file archiving tasks) where Defender’s impact is noticeable, but for day-to-day work (opening apps, browsing, working with Office documents) it runs quietly. Microsoft’s cloud-based analysis offloads some work from the local machine as well – instead of the CPU spending a long time analyzing a suspicious file, it can query the cloud which has more power.
-
No Double-Scanning Conflict: If you use Defender for Business, you avoid the scenario of having two AV engines vying for resources. Sometimes when third-party AVs are used on Windows, the built-in Defender needs to be disabled to prevent conflicts (otherwise both try to scan files, hurting performance). With Defender for Business, the single Defender engine does the job, so you don’t risk the system slowdowns or instability that can occur if a third-party AV isn’t configured properly alongside Windows Defender[2]. (Microsoft automatically manages the state – if a third-party product is active, Defender steps back; if not, Defender is active.)
-
Optimized for SMB hardware: Many small businesses might not have high-end workstations for all staff. The good news is Defender is suitable even on modest hardware. It has modes to reduce resource usage, and its requirements are the same as Windows 10/11 itself (no extra RAM/CPU beyond what the OS needs). Microsoft also provides an “performance analyzer” utility in the security portal that can help identify if any configuration (like an overly aggressive scan schedule) is affecting performance, allowing tuning. Typically, though, the default setup is balanced.
In field experience, when Defender replaces another antivirus, users often do not notice any change in system speed – which is ideal. In some cases, MSPs have reported improved performance after switching to Defender, particularly on older PCs, because some third-party suites were quite resource-intensive (with multiple components like password managers, system cleaners, etc. bundled in). Defender for Business focuses resources on security tasks and leverages the efficiency of being integrated into the OS.
Overall, the impact on performance is minimal for most users. Microsoft even runs Defender on low-spec devices like Surface tablets without issues. Of course, proper exclusions (for example, if you have software or development tools that generate lots of files, you might add exclusions) can help keep performance high. But out-of-the-box, Defender for Business strikes a good balance between vigilance and performance.
(Keep in mind, any active security scanning will consume some resources – no AV is zero-impact. The key is that Microsoft has optimized Defender to run as part of Windows, whereas some external vendors have had instances of causing slowdowns. With Defender for Business, the maintenance (updates) is seamless and the performance is tuned by Microsoft engineers who build Windows itself.)
9. Configuration and Management of Automated Response Features
Managing Microsoft Defender for Business is intended to be straightforward, even for IT admins who are not security specialists. Microsoft provides simplified configuration options to control automated response behavior:
-
Onboarding Devices: For Business Premium customers, devices enroll via Intune or the onboarding wizard in the Microsoft 365 Defender portal. Windows 10/11 devices can be onboarded in just a few steps; there’s no need to deploy a new agent (on Windows) because it uses the built-in one. For other platforms (Mac, iOS, Android), lightweight Defender apps/agents are available. The onboarding wizard in Defender for Business is wizard-driven and easy to follow[8], helping set up initial policies like what level of remediation automation you want.
-
Automation Levels (Remediation Settings): A key setting is how aggressive the automated remediation should be. In the Defender portal under Endpoints > Settings > Device Groups, you can configure device groups with different automation levels[9]:
- Full – Defender will automatically remediate threats (take action on alerts) without waiting for approval. This is usually recommended for most or all devices to maximize protection.
- Semi (Requires approval) – Defender will investigate and recommend actions, but an admin must approve the actual remediation (like file removal). This might be used on a very sensitive server or device where you want human oversight before anything is removed.
- None – Defender will not automatically remediate; it will only alert. (Not commonly used, except perhaps for testing or highly sensitive systems).
By default, Defender for Business places devices in a group with full automation enabled, since most SMBs prefer the solution just handle issues. You have the flexibility to create, say, a group for executives’ PCs that only does limited automation and assign those devices accordingly. All of this grouping and level setting is done in a simple UI in the portal[9].
-
Policy Management: Beyond automation level, you can configure various protection policies (attack surface reduction rules, web protection settings, firewall settings, etc.) via Intune or the Defender portal’s Endpoint settings. Microsoft provides sensible defaults (e.g., certain known risky behaviors like Office macros downloading executables might be set to block by default). These policies influence what is considered “malicious/suspicious” and thus can trigger automated response. The Secure Score interface also lists if there are recommended policy changes to improve security. Implementing those is a matter of a few clicks, thanks to integration with Intune’s configuration profiles.
-
Viewing and Managing Incidents: When an automated investigation runs, you can view its progress and results in the portal’s Incidents & Alerts queue. Each automated investigation provides a report: what was analyzed, what threats were found, and what actions were taken. From the Action Center, you can see any remediation actions that are pending approval (if you chose semi-automation) or that were automatically executed[9]. Admins can, at any time, intervene – for example, if a file was quarantined automatically and you determine it was a false positive, you can restore it from the portal. Likewise, you can trigger manual actions through the portal (such as isolating a machine, running an AV scan, or collecting an investigation package) if you want to add to what the automation has done.
-
Alerts and Notifications: You can configure email notifications for certain alerts or when many devices have automatic actions taken. This helps keep the IT admin informed about the significant events that automation handled. For instance, you might set a rule: if an incident is classified as “High” severity by Defender (even if it was resolved automatically), send an email to the IT team. That way nothing critical slips by unnoticed, even though automation addressed it.
-
Multi-Tenant Management: If you are an IT provider managing multiple customers, Microsoft 365 Lighthouse integration allows viewing security incidents across clients (with Defender for Business) in one place[3]. This is more for MSP scenarios but underscores that Microsoft has built management tools mindful of SMB needs (many SMBs use partners for IT).
In practice, administrators have found that most of the heavy lifting is done during initial setup (onboarding devices and setting desired policies). After that, day-to-day management largely involves monitoring the dashboard and only occasionally tweaking settings or performing additional manual investigations. The UI is unified and modern, avoiding the complexity of managing separate AV servers or consoles.
Furthermore, Microsoft’s documentation and recommendations (such as enabling certain attack surface reduction rules) are accessible right in the portal, guiding admins to make the most of the automated capabilities. In short, managing Defender for Business is integrated into your normal Microsoft 365 admin experience, and the automated response features can be fine-tuned with just a few configuration choices regarding how much control you want the system to have[9]. This makes it feasible for organizations with limited IT staff to still enforce strong security practices.
10. Compliance and Reporting Related to Automated Response
From a compliance perspective, using Defender for Business can help an organization meet various security control requirements and ease the burden of reporting and audits:
-
Contributing to Regulatory Compliance: Many regulations (like HIPAA, GDPR, etc.) require organizations to have malware protection, incident response processes, and audit trails. Defender for Business, as part of Business Premium, fulfills the malware protection and basic incident response technical controls in a compliant manner. Importantly, Microsoft’s cloud services (including Defender) have industry certifications such as FedRAMP, ISO 27001, SOC 2, etc., meaning the underlying service meets high security standards[8]. If your business needs to show that its security tools are vetted, using Defender can tick that box versus using an uncertified product.
-
Audit Trails and Logging: Every action that Defender for Business takes (or recommends) is logged. This includes alert detections, investigation findings, and remediation actions (like “malicious file XYZ quarantined from Device1 by automated investigation”). These logs are accessible through the Unified Audit Log in Microsoft 365. For compliance audits or incident post-mortems, you can export logs of what was done. For example, if an auditor asks “how do you respond to malware incidents?” – you can generate an audit log report showing that on date X malware was detected on a machine and Defender auto-quarantined it within 5 minutes, with details. This demonstrates a documented, consistent incident response process in line with many cybersecurity frameworks.
-
Reporting and Metrics: The Microsoft 365 Defender portal provides security reports that can be useful for compliance and executive oversight. For instance, you can produce monthly or quarterly reports on incidents, including how many were automatically remediated. Business Premium also offers a “Threat Analytics” section (slightly limited in the Business SKU compared to full E5, but still useful) that gives insight into prevalent threats and your exposure. There’s also integration with Secure Score, which is not a compliance metric per se, but often higher secure score corresponds to better alignment with recommended security practices. Organizations aiming for standards like NIST CSF or CIS controls will find that many of the relevant controls (malware defense, incident response, vulnerability management) are supported by Defender for Business’s features, and the evidence of those controls operating (like logs of malware being caught) is readily available[3].
-
Data Residency and Privacy: All data from Defender for Business resides in the Microsoft 365 cloud under your tenant, subject to the same data residency and privacy commitments Microsoft makes for M365. This is important for compliance with data protection laws – you aren’t sending your security telemetry to a third-party cloud of uncertain compliance; it stays within Microsoft’s compliant cloud. Also, by using one vendor (Microsoft) for the suite, you simplify any needed data processing agreements and assessments (since it’s covered under your M365 agreement).
-
Insurance and Governance: Cyber insurance providers increasingly require evidence of certain security measures. Having an endpoint XDR like Defender with automated response can help satisfy insurers that you have an “advanced antivirus/EDR” in place (often a checklist item). The fact that it automates response can be mentioned in policy questionnaires as it indicates a faster reaction time to incidents (which insurers like to see to reduce breach impact). For governance, IT managers can produce internal reports from the tool to show to boards or management: e.g., “Last quarter, 15 malware incidents were detected – 14 were automatically remediated by our security system, 1 required minor manual cleanup. No incidents led to a breach.” This kind of reporting underscores operational maturity.
In summary, Defender for Business integrates with Microsoft’s compliance and reporting ecosystem, making it easier to monitor and document your security posture. You get the benefit of Microsoft’s own compliant infrastructure, plus you can more easily demonstrate that you’re following best practices (thanks to logs and metrics from the Defender portal). If your business ever faces an audit or security assessment, the combination of Microsoft’s certifications and your own security operation evidence from Defender will strongly support the case that you’re managing endpoint security in a responsible and compliant way.
11. Support and Maintenance for Automated Response Features
Support and maintenance of Defender for Business is largely handled by Microsoft as part of the service, reducing the workload on your IT team:
-
Updates and Patches: Microsoft Defender’s antivirus engine and threat definitions receive continuous updates through Windows Update and the cloud. Security intelligence updates (new virus signatures, machine-learning model tweaks, etc.) are pushed out multiple times per day by Microsoft and are usually applied automatically with minimal user impact[4]. Because Defender is built-in, these are classified as security updates for Windows – they can be managed via your normal Windows Update for Business policies or left to auto-install. Additionally, the Defender platform itself can get feature improvements via Microsoft 365 service updates. All of this means you don’t have to manually download definition files or schedule server updates for your AV solution as was common in the past; it’s kept up-to-date by Microsoft’s cloud. Ensuring clients are on the latest protection is essentially hands-off.
-
Maintenance of Infrastructure: There is no on-premises server to maintain for managing Defender for Business. The management console is cloud-based. There’s also no separate SQL database or something you need to backup for security events – that’s all in Microsoft’s cloud. This contrasts with some traditional enterprise AV solutions that required an on-prem management server and regular maintenance of that system. With Defender, Microsoft handles the backend infrastructure health as part of the service (this is the benefit of a cloud service). As long as your devices are connected to the internet and to the service, they’ll be maintained.
-
Vendor Support: Since Defender for Business is included in Business Premium, support is provided by Microsoft under your Microsoft 365 support agreement. You can open support tickets with Microsoft 24/7 if you face an issue (for example, if you suspect an automated remediation didn’t work correctly, or you have trouble with a configuration). Microsoft’s support team is well-versed in their security products. This unified support is convenient – you don’t have to contact a third-party vendor for endpoint security issues and Microsoft for everything else; one support channel covers your whole environment. In scenarios where something isn’t functioning (perhaps an agent isn’t reporting or a portal issue), Microsoft will work on it and even escalate to their product engineering if needed. They have a vested interest in keeping your environment secure and their service running smoothly.
-
Community and Documentation: Microsoft has extensive documentation (on Microsoft Learn) for Defender for Business, and an active community (Tech Community forums, etc.) where you can seek advice. Because many partners and IT pros are adopting it, knowledge-sharing is abundant. This is more of a supplemental “support” – e.g., best practices for tuning automated response can be found via Microsoft’s docs or community posts. Microsoft also regularly updates documentation with new features (for example, if a new automated response capability is added or changed).
-
Maintenance from Admin Side: From the admin side, maintenance is minimal. Key things to ensure: devices remain onboarded (through Intune etc.), and that they regularly receive updates (which you’d ensure anyway as part of Windows patching). You might periodically review policy settings as your org evolves. But you won’t be spending time on tasks like signature distribution, or upgrading server software, or things that one had to do with older AV solutions. The main “maintenance” task is reviewing the security reports and adjusting policies if needed – which is more of an operational task than a technical upkeep task.
-
Service Reliability: Microsoft’s cloud services, including Defender, have high availability. In the unlikely event the cloud portal is temporarily inaccessible, the local Defender clients on devices still function (they have locally cached intelligence and will continue to protect endpoints, then sync logs later). Thus your protection isn’t dependent on constant connectivity to the cloud – it helps for the latest intel, but even offline, devices are protected. This resilient design reduces the worry that a cloud outage could leave you defenseless (it won’t).
In essence, by using Defender for Business, you offload the heavy maintenance to Microsoft. Your endpoints stay updated automatically, and if an issue arises, Microsoft’s support can assist as part of your existing subscription – no separate maintenance contracts with another vendor. Many IT admins consider the “built-in” aspect as a big win: it’s one less separate product to manage.
A practical example: if a definition update ever caused a problem (maybe a false positive outbreak), Microsoft can swiftly issue an update to fix it, and your devices will pick it up automatically. With a third-party, you’d have to coordinate that fix with an external support and distribution mechanism. So the support/maintenance experience is smoother and more integrated with Defender for Business, aligning with Microsoft’s overall management of your cloud services.
12. Threat Intelligence and Machine Learning in Defender for Business
Microsoft Defender for Business benefits from the same threat intelligence (TI) and machine learning backbone that powers Microsoft’s enterprise security products. This is a significant strength, as Microsoft’s threat intelligence network is one of the largest in the world:
-
Global Threat Signal Collection: Microsoft processes over 8 trillion security signals daily across Windows, Azure, Office, and its partner ecosystem. Everything from virus encounters on home Windows PCs to nation-state actor tactics observed by Microsoft’s Incident Response teams feeds into their threat intelligence. Defender for Business taps into this rich TI. For example, if a new malware strain is detected on thousands of Windows devices globally, Microsoft can deploy a cloud-delivered update or AI model adjustment within minutes to recognize and stop that malware everywhere. Your Defender for Business endpoints thereby receive knowledge of emerging threats almost in real-time. A third-party AV relies on its vendor’s threat intel; few have the breadth of data that Microsoft does (especially regarding how threats play out in Office 365 or Azure AD). Microsoft specifically notes it leverages cloud intelligence, AI, and machine learning for advanced threat detection and response[8].
-
AI and Machine Learning: The Defender platform uses a layered AI approach. On the endpoint, lightweight machine-learning models inspect suspicious files or behaviors. In the cloud, more complex ML models analyze data from endpoints to catch patterns (for instance, detecting a script that’s launching in many customer environments with similar characteristics might flag it as a malware campaign). These ML models are continuously trained on the vast data Microsoft has. Concretely, this means Defender can detect completely new (“zero-day”) threats because it recognizes malicious patterns or anomaly behaviors – not just via known signatures. When it does, it can automatically create a remediation. An example: through ML, Defender might flag a never-before-seen file as ransomware based on how it operates, and automatically stop it. Many traditional AVs without such AI would miss it until a signature is created post-infection. Microsoft states that “Defender for Business uses the same cloud-based AI and automation as our enterprise Defender – examining suspicious behavior and responding with the ideal analyst actions”[7].
-
Microsoft Threat Experts and Analytics: While the full “Threat Experts” service (human-in-the-loop) is an E5 feature, the insights from Microsoft’s security researchers are folded into the Defender platform for everyone. Defender for Business has access to Threat Analytics reports (somewhat limited version) which inform admins about prevalent threats and if any were seen in their environment. The automated response system is also tuned by Microsoft’s security team – when they discover new attacker techniques, they often update the automated investigation playbooks. Essentially, Defender for Business’ automated responses are informed by the experience of Microsoft’s top researchers who encode their knowledge into the product.
-
Correlation of Signals: The platform doesn’t rely only on one signal. For example, threat intelligence may indicate that if process A spawns process B and contacts domain X, it’s 95% likely to be malware. Defender’s automation will take that TI rule and if it sees it on your endpoint, it will act immediately (kill process, etc.). Another scenario: Microsoft’s TI knows certain PowerShell commands are often used by hackers – if that happens on your PC, Defender’s ML might deem it malicious in context and terminate it. These kinds of compound analytics (correlating multiple low-level events into a high-confidence alert) are powered by Microsoft’s cloud analytics and delivered to your endpoints via the Defender cloud connection.
-
Updates from Attacks on Others: One benefit of a cloud-native solution is that “when one of us is attacked, all of us learn.” If an automated investigation in one tenant finds a new threat and how to remediate it, the intelligence from that can improve protections for other tenants. Microsoft might, for instance, add a hash of a newly seen ransomware file to the block list globally. So SMBs using Defender for Business indirectly benefit from attacks that might be happening elsewhere — the product’s defensive AI improves continuously. This is a network effect that standalone solutions without a big cloud network can’t match.
-
Potential Missing Elements: It’s worth mentioning that while Defender for Business has world-class threat intel for detection and remediation, the advanced hunting feature (where you can write custom queries to search the raw data) is not available in the Business SKU (that’s a Plan 2 feature)[5]. This means the system’s AI is doing the work under the hood, but you, as an admin, can’t manually trawl through 6 months of raw event data looking for specific TI indicators. However, for most SMB needs, the automated TI and alerts suffice. If there’s a specific threat indicator (like an IOC from an ISAC or something), you might not be able to query it directly in Defender for Business, but Microsoft’s analytics likely would catch if that IOC manifested in typical malicious behavior. If custom threat hunting is critical, that might be a case for an upgrade, but otherwise the built-in intelligence covers the bases.
In summary, Microsoft Defender for Business stands on a foundation of extensive threat intelligence and sophisticated machine learning. This gives it an edge in identifying and responding to threats (the automated response logic is “smart” because it’s informed by millions of prior incidents). Small businesses using Defender for Business effectively outsource a huge part of threat research and analytics to Microsoft’s AI and security team. Rather than having to research new threats or tune detection rules yourself, the service delivers those insights to your devices automatically, ensuring you’re protected against even cutting-edge attacks[8]. This level of protection would be very hard to maintain on one’s own or with basic security tools.
13. User Interface and Ease of Use for Managing Defender for Business
Microsoft has put a lot of effort into making Defender for Business easy to deploy and use, especially knowing that small businesses may not have dedicated security engineers. The experience is designed to be familiar to those who manage Microsoft 365, and streamlined so that essential information is front and center without excessive complexity:
-
Unified & Familiar Portal: The management UI for Defender for Business is the Microsoft 365 Defender portal, which has a modern web interface consistent with other Microsoft 365 admin portals. If you’ve used the Microsoft 365 Security Center or Compliance Center, this will feel similar. Navigation is on the left (Incidents, Alerts, Action Center, Reports, Settings, etc.). It’s not an old-school MMC or clunky third-party UI; it’s web-based, responsive, and integrated with things like Azure AD (for login and role permissions). Role-based access can be used so that, for example, an IT helpdesk could only view alerts but not change settings.
-
Wizard-Based Onboarding: As mentioned earlier, initial setup is guided by wizards[8]. For instance, adding devices has a wizard that generates a script or directs you to Intune steps, making what could be a complex procedure (deploying endpoint agents) into a a few guided clicks. The portal also provides tooltips and explanations for various settings, helpful for admins who might not know what “attack surface reduction rule” means – the UI explains it in approachable terms.
-
Out-of-the-Box Defaults: Microsoft enables many protections by default, so the interface won’t overwhelm you with 100 decisions to make on day one. Recommended security policies are activated out-of-the-box[8]. For example, cloud-delivered protection and automatic sample submission (so the AI can analyze suspicious files) are on by default; automated remediation is on full by default. This means from the get-go, you have a good security posture without twiddling lots of knobs. The UI will highlight if there are recommended actions not taken.
-
Incident Queue and Alert Details: The portal’s Incidents page automatically groups related alerts into a single incident view – which drastically simplifies understanding attacks[2]. Instead of a flood of separate alert entries, you might see one incident that says “Emotet malware infection detected” and clicking it shows: 3 alerts (one for a suspicious file, one for a malicious connection, one for a modification in registry) all tied together. It then shows Affected assets (device name, user) and Actions taken (e.g., quarantined file, blocked network connection) as a timeline. This cohesive story is much easier to follow than separate logs. Admins can drill down into technical details as needed, but the high-level summary is non-technical enough that even a less-experienced IT staff member can understand what happened and what was done about it.
-
Action Center and Recommendation Cards: The Action Center surfaces things that need admin attention, like remediation actions pending approval or items that were prevented but awaiting confirmation. The UI uses simple language, e.g., “Approve file removal: Trojan:Win32/Something was found and is pending removal.” With one click (“Approve”), you can execute the recommendation. The Secure Score section will have cards like “Turn on rule X to block Office from creating child processes – this will improve security”, with an option to enact that change right from the portal. This guided improvement approach means you don’t have to be a security expert to harden the system; the UI literally walks you through it.
-
Ease of Use for Day-to-Day: In daily use, most admins will set up email notifications or check the portal periodically. The learning curve to interpret the dashboards is not steep – Microsoft uses a lot of visual aids (charts for trend of malware, etc.). The Device inventory shows at a glance which devices are healthy vs have alerts. Each device page can show its risk level and if any action is needed. Many have likened the experience to using a modern IT management SaaS rather than a clunky AV program. For example, contrast reading raw antivirus log files vs. opening an incident in Defender where it says in plain English “Malware X was detected and removed from , no further action is needed” – clearly and in one place.
-
Cross-Platform Consistency: If you do have Macs or mobile devices, those report into the same portal. So you’re not dealing with separate tools per OS. The portal abstracts it – a device is listed with its OS, but the security events all come through similarly. This unified view contributes to ease of use, since you don’t have to mentally switch contexts for different device types.
-
Training and Support within UI: Microsoft has embedded a “Learning hub” in the Defender portal with how-to guides and even quick playbooks for investigating incidents. If you’re unsure what to do when you see a certain alert, Microsoft often provides a link like “Learn about this threat” which goes to documentation or community posts. This helps newer admins react properly.
Overall, Defender for Business’ UI is geared towards simplicity and clarity, automating the complex correlations and presenting the admin with straightforward information and choices. Many small business IT admins who have used it remark that after initial setup, it requires very little babysitting – they glance at the dashboard maybe daily or get email summaries, and most of the time it’s all green or automatically handled. In the cases where something isn’t automatic, the portal’s guidance (recommendations, one-click fixes) makes it easy to address.
This is in stark contrast to some legacy AV management, which might require digging through event logs or manually running scans on clients. With Defender for Business, the heavy analysis is done by the system, and the interface yields insights, not just raw data[2]. This design focus on ease is crucial in SMB environments, and Microsoft has largely succeeded in creating a user-friendly security management experience.
14. Cost Implications of Using Defender for Business’ Automated Features
In terms of cost, Microsoft Defender for Business is highly attractive, especially when compared to third-party security solutions offering similar capabilities:
-
Included Value in Business Premium: If your organization already subscribes to Microsoft 365 Business Premium (which many do for the productivity suite and email), Defender for Business is included at no extra cost. You are essentially getting an advanced endpoint protection and response suite “for free” as part of your subscription[2]. Previously, a small business might have had to pay for an additional EDR product or an antivirus license per device on top of their Microsoft 365 licensing. Now, that extra expense can be eliminated, translating to direct cost savings. For example, if a Business Premium customer was paying $5 per device per month for a third-party endpoint security solution, they can save that entire cost by switching to the included Defender – which over a year for, say, 50 devices, is a substantial amount saved.
-
Standalone Pricing: Even if you don’t have Business Premium, Defender for Business as a standalone is priced at ~$3 per user/month (covering up to 5 devices per user)[2]. This is very competitive. Many third-party business antivirus/EDR products are notably more expensive for equivalent coverage. For instance, some leading SMB security suites might be $5-6 per device/month or more for EDR functionality. Microsoft’s scale and bundling strategy allow them to offer Defender at a low price point.
-
No Double-Purchase Needed: One hidden cost with third-party solutions is that you might end up “paying twice for endpoint protection” if you already have Microsoft 365. Essentially, you’ve paid Microsoft for Windows Defender as part of your OS and for basic security in your suite, but then you pay another vendor for a similar service. Using Defender for Business consolidates this – you fully utilize what you’ve paid Microsoft for, instead of sidelining it and paying extra elsewhere. This was mentioned in the context that Business Premium customers should leverage Defender because otherwise they’re “effectively paying twice for endpoint protection (since Defender is included)”[2].
-
Lower Total Cost of Ownership: Beyond the raw licensing costs, consider operational costs we discussed: With Defender for Business, there’s no separate server or infrastructure to maintain (saves IT admin labor/time, which is money), and the automation can potentially reduce incident recovery costs (by stopping breaches faster, you avoid expensive recovery or downtime). If a third-party solution had less effective automation and an incident went further, the business impact cost could be higher. Also, unified support (one vendor) can shorten resolution times, indirectly saving money.
-
Competitive Differentiator: For Microsoft partners or MSPs, having Defender for Business included can be a selling point to customers – “We can upgrade you to Business Premium and secure your endpoints without additional licenses.” Before, MSPs might have had to upsell a separate security product. Now it’s bundled, which can make your offering more cost-competitive for clients. Microsoft often cites that moving to Business Premium (with Defender) can consolidate and replace multiple point solutions, resulting in 50%+ cost savings over a patchwork of separate products. This “license consolidation” story is strong: one subscription covers office apps, email, device management, and security, which is financially simpler and usually cheaper overall.
-
Scaling and Flexibility: The cost is per user (up to 5 devices). This is beneficial if users have multiple devices (laptop, desktop, phone) – you’re not paying per device. Small companies with device/user ratios >1 especially gain here. Microsoft doesn’t charge for “servers” under Defender for Business except if you opt for the server add-on ($3 per server). Competing endpoint solutions often charge separately for server endpoints at a higher rate. So if you have a couple of Windows servers, adding them under Defender’s protection is relatively cheap with the add-on.
-
No Surprise Fees: All features of Defender for Business (the whole automated response, etc.) are included in that cost. Some other vendors segment features – e.g., basic AV vs. an “EDR” add-on at extra cost. With Microsoft, you get the full feature set in one plan. The only time you’d pay more is if you decide to step up to E5/Plan2 for more features, but that’s a deliberate choice, not a hidden fee scenario.
In summary, Defender for Business offers excellent cost efficiency. It leverages the economy of scale of Microsoft’s cloud to give enterprise-grade defense at SMB-friendly pricing. If you’re already invested in the M365 ecosystem, it’s essentially a built-in benefit that can reduce the need for other security expenditures. Organizations that switch to using Defender for Business commonly find they can eliminate separate antivirus subscriptions, simplify their billing (fewer vendors), and possibly channel those saved funds into other IT needs. Considering the high cost of cyber incidents, having strong protection included without breaking the bank is a significant advantage.
15. Future Developments and Roadmap for Defender for Business
Microsoft has been actively improving Defender for Business since its launch, and there’s a clear roadmap to continue enhancing its capabilities. Some points about its future:
-
Closing the Gap with Enterprise Features: As of now, Defender for Business is very close to the full Defender for Endpoint Plan 2 in functionality, with a few exceptions (advanced hunting, etc.). Microsoft has indicated that some of the features “have been simplified for SMB” but they plan to bring additional capabilities over time as appropriate[1]. For example, Threat Analytics (detailed reports on big threat campaigns) is partially available – they might expand that. Device timelines and forensic data might be enriched in the future as they optimize the portal for SMB usability. Essentially, Microsoft is likely to continuously backport relevant enterprise features into Defender for Business, as long as they can be made user-friendly.
-
Server Protection Integration: Microsoft recently introduced a Defender for Business Servers add-on. Initially in preview and now generally available, this allows protecting Windows and Linux servers with the same simplicity (for $3 per server). Going forward, we can expect tighter integration for server scenarios – possibly bringing more server-specific automated response actions. The roadmap likely includes making the experience for servers as seamless as clients. This is important for SMBs that might have a couple of on-prem servers; soon they will be first-class citizens in the Defender for Business portal with similar automated investigations. The add-on was on the roadmap and it got delivered, showing Microsoft’s commitment to expanding coverage[3].
-
Multi-Tenant Management & MSP Features: Microsoft 365 Lighthouse already started showing incidents from Defender for Business across multiple customer tenants for partners. The roadmap mentions additional management capabilities coming to Lighthouse integration[3]. This likely means better multi-tenant alerting, perhaps policy templates MSPs can deploy across all clients, etc. Microsoft knows MSPs are key in the SMB space, so features that help MSPs manage Defender for Business at scale are in development.
-
Deeper Automation and XDR: Microsoft is heavily investing in the concept of XDR (extended detection and response). We can expect that Defender for Business will continue to get more “XDR” capabilities, meaning even more integration of signals and automated playbooks that cut across products. For instance, automated cross-domain remediation (like disabling a user account when their device is owned by ransomware) could get smarter and more configurable. Additionally, as Azure services and cloud apps multiply, Defender for Business might incorporate more signals from those (for example, integration with Defender for Cloud Apps for SMB, if that becomes feasible). Microsoft’s Security Copilot (an AI assistant for security) is an emerging tech in preview for enterprise; down the line, scaled versions of such AI assistance might reach Business Premium customers too, to help interpret and advise on incidents.
-
User Experience Tweaks: Based on feedback, Microsoft will likely refine the UI and workflows. They might add more granular roles (so that, say, a Tier1 support can only view basic info while a Global Admin can tweak policies). They might also introduce simpler reports geared for executives or compliance. These are minor, but as the product matures in the SMB market, UI/UX adjustments are expected to make it even more approachable.
-
Staying Ahead of Threats: On the threat intelligence side, the service will evolve to address new attack techniques. For example, as more attackers abuse cloud apps or IoT, Microsoft may integrate relevant signals or release updates to the automated logic to handle those. Being cloud-delivered, these improvements happen continuously rather than in big version jumps.
-
Licensing and Packaging: Microsoft could potentially offer Business Premium “add-ons” for more security. For instance, if an SMB wants advanced hunting without going full E5, Microsoft might consider some mid-range addon in the future. While nothing concrete is announced, Microsoft’s general strategy is flexibility – so future licensing options might appear to let SMBs opt into certain advanced features à la carte.
Microsoft often shares broad updates at its conferences (Ignite, Inspire). The trajectory for Defender for Business is that it will be the go-to security solution for SMBs, and as such, Microsoft will ensure it keeps up with the threat landscape and customer needs. Comments from Microsoft security teams reinforce that “we are bringing enterprise-grade capabilities to SMBs” and they will continue to do so[1].
Given the rapid advancements we’ve already seen (the product GA’d in 2022 and has since gotten server support, Lighthouse integration, more policies, etc.), we can be confident that Defender for Business will only get more powerful over time. For an SMB, that means investing in it carries the benefit that your protection will improve without you having to switch solutions or pay more, aligning with Microsoft’s cloud-delivered continuous improvement model. In summary, the roadmap points to more integration, more intelligence, and more tools for admins, all while keeping the service approachable for its target audience. Using Defender for Business today sets you up to automatically receive these future enhancements as they roll out, ensuring your security keeps evolving to face new challenges.[3][1]
References: The information and claims in this report are supported by Microsoft documentation, independent reviews, and expert commentary:
[11] ReliaQuest – Definition of automated incident response and its use of software/ML/AI for automatic detection and response.
[9] ThirdTier – Statement that Defender for Business includes automated investigation and response, shutting down malware when detected.
[7] Microsoft BDM Pitch Deck – Explains Defender for Business automatically investigates alerts, mimics analyst steps, tackles file/memory attacks, and scales with 24×7 responses.
[8] Microsoft Security (Defender for Business page) – Confirms Defender for Business offers automated investigation and remediation to automatically resolve threats, leveraging cloud intelligence and AI.
[2] TechRadar Pro Review – Notes Defender for Business is above and beyond traditional AV with automated protection and response for up to 300 users.
[10] MS Learn (MS 365 Defender) – Describes how Microsoft 365 Defender coordinates detection, prevention, investigation, and response across identities, endpoints, etc. in a central portal.
[9] ThirdTier – Guide snippet on configuring Defender for Business for automated investigation and remediation via device groups and full automatic remediation setting.
[9] ThirdTier – Describes the Action Center in Defender portal listing ongoing and completed automated investigations with details for each incident.
[9] ThirdTier – Real-world example where a malware in a client’s website backup was automatically quarantined by Defender for Business, with details provided for additional action.
[8] Microsoft Security (Defender for Business page) – Mentions “AI-powered EDR with automatic attack disruption to disrupt in-progress ransomware attacks in real-time.”
[7] Microsoft BDM Pitch Deck – Gives example: if malicious process found, Defender for Business will restrict its execution and remove persistence (registry keys), acting 24/7 with no human needed.
[6] MS Partner Deck – Cites Alex Fields (MSP) praising Defender for Business’ feature set and inclusion in Business Premium as the gold standard.
[2] TechRadar – Observes that Defender for Business groups alerts into single incidents for easier response, and mentions a slick interface and summary reports.
[5] Practical365 – Explains differences: Plan 2 covers automated investigation & response, Plan 1 is limited AV, Defender for Business sits between with EDR but no advanced hunting.
[5] Practical365 – Notes Defender for Business lacks threat hunting and certain detailed data compared to Plan 2, implying those are enterprise-only unless upgrading.
[4] Microsoft Q&A – Clarifies that Windows Defender updates are part of security updates (Windows Update), including intelligence and platform updates to enhance Windows Defender’s capabilities.
[3] Partner Opportunity Deck – Indicates that in Lighthouse (multi-tenant tool) you can view incidents from Defender for Business and that “additional security management capabilities are planned on the roadmap.”
[2] TechRadar – States pricing: $3/user/month standalone, included in M365 Business Premium at no extra cost for subscribers.
[1]
References
[1] CSP Masters – S4 – SeamlessSecurity
[2] AV-Comparatives, AV-TEST show how Defender, McAfee, Norton … – Neowin
[3] Microsoft-Defender-for-Business-Partner-Opportunity-Summary
[4] Is Windows defender update included in this? – Microsoft Q&A
[5] How does Microsoft Defender for Business compare to Defender for …
[6] Microsoft-Defender-for-Business-Partner-Ready-Deck
[7] Microsoft-Defender-for-Business-Customer-Pitch-Deck-BDM
[8] Microsoft Defender for Business | Microsoft Security
[9] Setup up automated investigation and response – Third Tier
[10] Module 02 – Security – RDC
[11] Understanding Automated Incident Response – ReliaQuest
[12] Microsoft-Defender-for-Business-To-Partner-Objection-Handling