Once you have added an Apple certificate to allow device management for iOS as I have detailed previously here:
Adding an Apple Certificate to Intune
the next step in the process to get your iOS device managed is to create a specific iOS compliance policy in Intune.
A compliance policy is basically a set of rules that the device must follow to be considered compliant. If the device fails these rules then it is considered noncompliant and you are able to take action on that such as excluding it from connecting to your corporate data. Compliance for all devices is checked regularly.
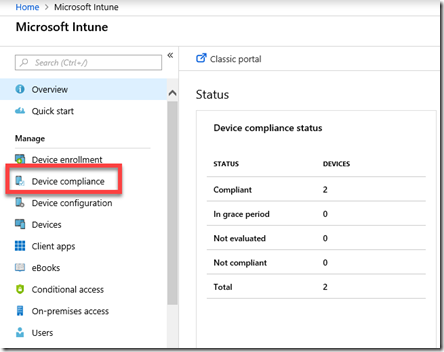
To create this compliance policy you’ll need to login to the Azure portal and navigate to the Intune service. Once there, you’ll find an option in the menu Device Compliance as shown above, that you’ll need to select.
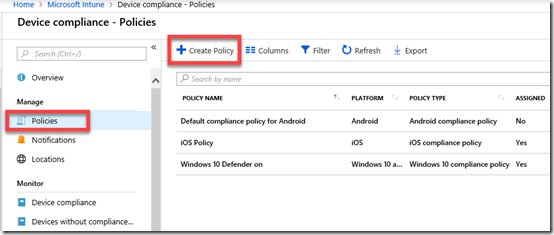
You’ll then need to select Policies on the left and the Create Policy option from the menu on the right that appears as shown above.
You may also see number of other existing policies here for different platforms. Note, that it is possible to have multiple compliance policies for the same platform if desired.

You’ll now need to give the new iOS compliance policy a Name, Description and select the Platform as iOS as shown above.
You’ll then need to select the Settings option below this to configure compliance rules. When you do so another blade will appear on the right with four categories: Email, Device Health, Device Properties and System Security as shown above.

You can configure as many options as you like here but I’m going to cover what I consider the basics for iOS compliance.
In Device Health, set Jailbroken devices to Block as shown above.

In System Security set the Password options as shown above.
Make sure you select OK at the bottom of each setting to update your preferences.
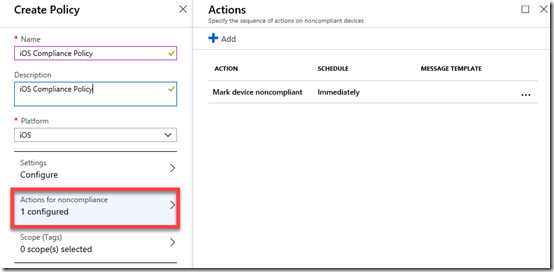
If you go into the Actions for noncompliance you’ll see there is currently a default option to Mark device noncompliant.

You can add more actions here, to Send email to end user and/or Remotely lock the noncompliant device if you wish.
When you have finished making your change, ensure that you Save the policy.

Now that the new iOS compliance policy has been created you’ll need to apply that policy to a group of users. To do this, select the policy you just created from the list of compliance policies. Then select the Assignments option from the menu on the left.
It is probably easiest to apply this new policy to all users but you can certainly select a group of users as well as exclude user if you wish.
Once again, when you have made you selection, ensure you Save any changes to have the policy applied to these users.
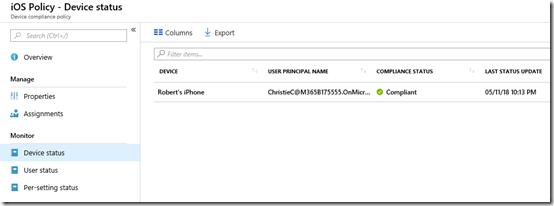
When devices connect to the tenant, they will be evaluated to be compliant or not. When this occurs, you can again examine the options at the bottom of the policy to see the device status as shown above. This will tell you whether connected devices are compliant (here they are).

You can also get the status by user, because remember, some users may have multiple devices.
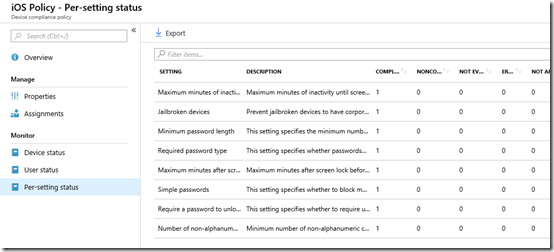
Finally, you can also examine the per-setting status. This is handy if a device has failed compliance and you want to know exactly what setting(s) have caused this failure.

You can also see the compliance by examining the individual device in Intune as shown above.
You’ll see here that there is in fact a default compliance policy as well as any your have created.
Selecting the Built-in Device Compliance Policy will show you its settings like so:

Basically, the Built-in Compliance Policy simply checks whether device is active, the user exists in the tenant and another compliance policy has been assigned. Thus, the device won’t be considered compliant by default until we create at least one compliant policy for the platform.
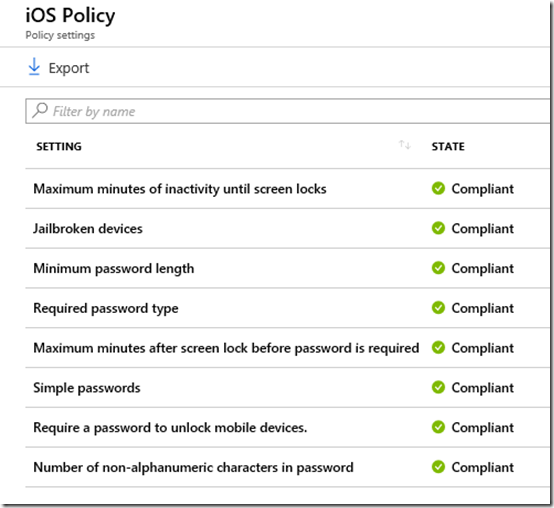
If you instead select any of the custom compliance policies that you created you will see whether each individual setting is considered compliant in that policy as shown above.
So, creating a device compliance policy is important when we wish to use Intune to manage devices. You need to create a compliance policy for each platform with the settings against which devices will be continually checked. This will ensure that devices connecting to your environment maintain the settings you desire.
The next step will be setting up device configuration policies to actually configure how the device operates. That will be covered in an upcoming article.

 =””>
=””>