One of the great things that Windows 10 Professional and above provide is the ability to connect directly to Azure AD. Hopefully, as you are aware Office 365 identity is built on Azure AD. Thus, if we connect Windows 10 to an Azure AD that is part of an Office 365 tenant we get simplified sign on. This basically means when users open Microsoft browsers (IE or Edge) and navigate to the Office 365 portal they are automatically logged on because their credentials are already part of Windows 10 thanks to Azure AD join. This simplified login also works with desktop applications like Word, Excel, PowerPoint etc plus some third party applications. In short, users get logged directly into applications once they login to their desktop thanks to Azure AD join.
Now there are a couple of ways of joining Windows 10 to Azure AD. I’ve previously covered how to basically ‘add’ your Azure AD/Office 365 credentials to an existing Windows 10 installation here:
Connect Windows 10 to Azure AD
That method isn’t quite as full featured as if you set up your Windows 10 machine to join Office 365 during the setup of Windows 10.
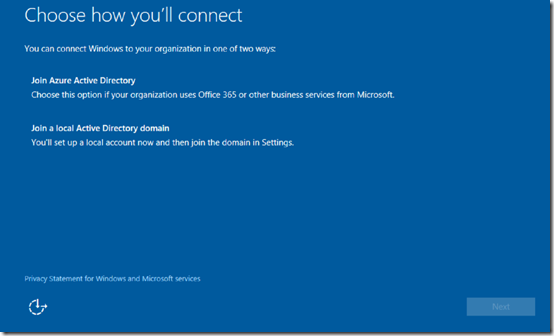
The process for doing that configuration, is that during the installation of Windows 10 onto a machine you’ll receive a prompt like that show above asking you to Join Azure Active Directory or Join a local Active Directory domain.
So what I’m going to assume here is that I want this Windows 10 machine to be only joined to Office 365/Azure AD because there no local AD. So I select the Join Azure Active Directory option.
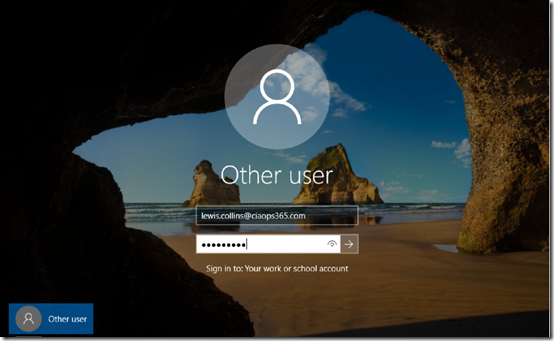
I’m then prompted to enter my Azure AD credentials. Remember, these credentials are what you use to login to Office 365.
I enter the user’s Office 365 details and select Sign in. Now it is also important to note here that this new user will also be, by default, an administrator of the local Windows 10 machine. If you don’t want to allow your users to be administrators of the local desktop then you’ll need to remove this account after setup has completed.
The Windows 10 setup process will continue and eventually you’ll be prompted to login to the machine. You should login with your Office 365 credentials as shown when prompted.
The Windows 10 desktop will then do a little more setup as shown above.
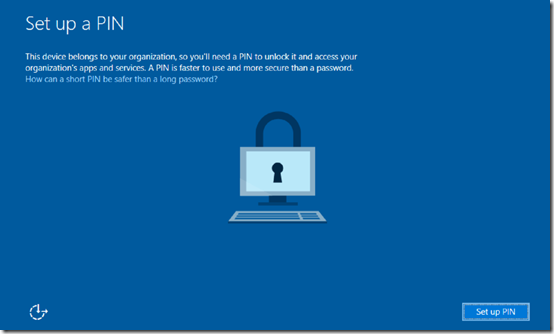
In this case I’m also then prompted to create a 4 digit pin for this machine. I’ll show you more about why this happens shortly but basically because I am joining this machine to Office 365 the Mobile Device Management (MDM) policies I have established are now being applied to this device. One of the policies I have configured is to require a PIN.
If we dig into the local machine name as seen above,
We now see that same machine in the MDM for Office 365 as shown above.
This means it will have the MDM security policies applied to it that I have configured. In this case, as you can see from the above configuration, I require devices to have at least a 4 digit pin password.
Don’t forget that Office 365 MDM is a free and included part of the service.
If I now look at the properties of the user on the directly joined machine just set up, I see the above, basically a single user with an Office 365 identity.
If I then look in the work and school account I see that it is connected to my Azure AD as shown above. Therefore, here I have only one account that logs me into the local machine and my Office 365.
Compare that situation to when I already have a functioning Windows 10 machines and I associate it to Azure AD. When I do that I only see the local user as the identity as shown above. Thus, I am actually logging into this Windows 10 machine with a local account rather than my Office 365 account.
When I look in the work or school account area I again see a connection to my Azure AD. Thus, I login to this Windows 10 device with a local account which is then associated to an Office 365 account. Therefore I have two accounts in operation now, a local account and an Office 365 account.
The big difference here is that by using an Office 365 login during the installation of Windows 10 I get an Office 365 login to my box, whereas if I connect to Azure AD after my Windows 10 is installed I only get a local account login.
In both cases, when I visit a site in an Microsoft browser (IE or Edge) such as the Office 365 portal, I am not prompted to login because these credential are furnished directly from Windows 10.
It is my experience that having just the one Office 365 login associated with a Windows 10 device is more reliable when it comes to this same sign on than if you merely associate an Office 365 login with an existing Windows 10 box. The trade off is, of course, that you only get this single Office 365 login to the box if you install Windows 10 from scratch, which may not always be possible.
So can you add an Office 365 to an existing Windows 10 machine and achieve browser and application same sign on? Yes. However, I would suggest a better option is to actually setup Windows 10 from scratch using an Office 365 account. You’ll get much better same sign on and be prepared for further integration down the track. You also remove the complexity of multiple accounts on the one desktop.
The main reason that you want to join your Windows 10 machines to Office 365/Azure AD is probably to eliminate the need for any local AD. This will also mean the elimination of on premises equipment and ensuing cost savings.
The main reason for retaining a local AD these days is simply for group policy, but in my experience is that most of what needs to be done with group policy can either be done with Office 365 MDM (which is free) out of the box or upgrading to Windows Intune or Azure AD Domain Services. That, in essence, now suggests that there is no real need for a local domain controller on premises at all. It can easily be eliminated with the integration of Windows 10, Office 365 and Azure AD as shown.









This kinda sucks. One of the advantages of AD was roaming user profiles. Any staff member can jump on to any available domain joined machine and sign in with their own credentials and have all their files available to them.
This is several steps backwards. Not only can’t users do that any more, you now have to wipe the machine and re-install everything from scratch?????
LikeLike
They can work like they used to. Roaming is done with a combination of Enterprise state roaming and known folder move. Different age, different approach that’s all. Old style roaming profile are not without their own issues.
LikeLike
um… one drive?
LikeLike