In a recent article I covered off how to:
Onboard Windows 10 devices to Microsoft Defender for Business
Two easy methods of onboarding Windows 10 devices to Defender for Business
Now we need to know how to offboard Windows 10 devices from Microsoft Defender for Business.
The first place to start is to review this article from Microsoft:
Offboard devices from the Microsoft Defender for Endpoint service
It details the following points:
– The status of a device will be switched to Inactive 7 days after offboarding.
– Offboarded devices’ data (such as Timeline, Alerts, Vulnerabilities, etc.) will remain in the portal until the configured retention period expires.
– The device’s profile (without data) will remain in the Devices List for no longer than 180 days.
– In addition, devices that are not active in the last 30 days are not factored in on the data that reflects your organization’s threat and vulnerability management exposure score and Microsoft Secure Score for Devices.
– To view only active devices, you can filter by health state, device tags or machine groups.
In essence what this means is that although you offboard a device a lot of information about that device will remain in the portal. Also, even after offboarding a device, if you look in the Endpoint portal, at first glance the device still appears to be there. The reality is that offboarding a device doesn’t make it ‘disappear’ from the portal immediately. This means we’ll need to use another method to verify that the device has actually been offboarded.

The easiest way is to look in the following registry key on the machine:
HKLM:\Software\Microsoft\Windows Advanced Threat Protection\Status
and examine the value of the key:
OnboardingState
If that is set to 1, as shown above, then the device is still considered connected to Microsoft Defender fo Endpoint. Thus, to confirm the device has been offboarded, we need to check that this value is 0.
You’ll also need to have a license for Intune/Endpoint Manager to enable this process from a centralised location.
Although not completely necessary it is best practice to have the integration between Microsoft Endpoint Manager portal and Defender for Endpoint enabled. Visit:
https://endpoint.microsoft.com
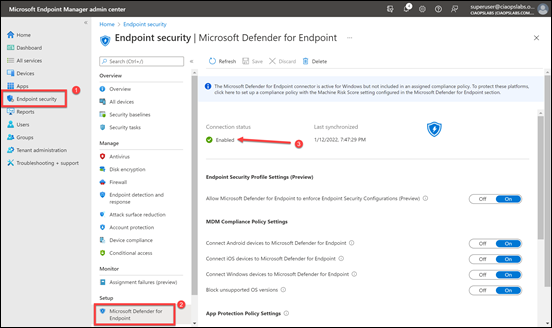
As shown above, here, navigate to Endpoint Security, then Microsoft Defender for Endpoint. Ensure that the option Connection status is enabled. If it isn’t then take a look at my previous onboarding article that shows you how to enable this.
Next, navigate to:
https://security.microsoft.com

You should see the screen above. Scroll down this page.
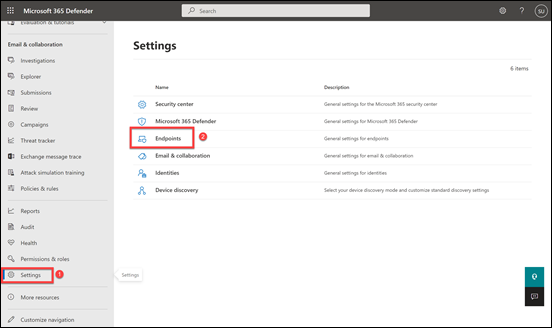
Select Settings as shown above and then Endpoints from the options that appear on the right.

From the menu on left scroll down and select Offboarding. On the right then select Windows 10 and 11 as the operating system. Then select Mobile Device Management / Microsoft Intune. With these selections made a Download package button should appear. Select this to download a zip file that contains a file called WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding
For security reasons, the package used to Offboard devices will expire 30 days after the date it was downloaded. Expired offboarding packages sent to a device will be rejected. That expiry date will be contained in the filename.

Navigate back to Microsoft Endpoint Manager and select Devices | Configuration profiles, then Create Profile.

Select Windows 10 and later for the Platform and Templates from the Profile type.

Select Custom from the list and then Create.

Give the policy a name and description and select Next to continue.

Select the Add button.

Enter the following details into the fields that appear on the right as shown above:
Name = <unique name>
OMA-URI = ./Device/Vendor/MSFT/WindowsAdvancedThreatProtection/Offboarding
Data type = String
Value = <contents of the unzipped file WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding downloaded from Defender for Endpoint portal>

The WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding file can be opened with Notepad and should look like the above.
Press the Save button to continue.

The Configuration settings page should now look like the above with the single entry you just configured.
Press the Next button to continue.

You now need to select which items this policy will apply to. In general, you are not going to be offboard all your devices at the same time from Defender for Endpoint. What we need to do then is target a specific group of devices.
A good approach to achieving this is to create a dedicated device group, with only the devices you wish to offboard with this policy. I detailed how to create such a group in Azure AD here:
Create a dynamic group in Azure AD
In this case, the dynamic group is called To be retired and I will assign it to the Intune policy as shown above.
Continue to select Next and then Create to complete the policy creation process.

If you select the Device status option as shown above, you’ll see whether the policy has been successfully applied to the devices. How long this takes will depend on when the devices ‘check in’ to get the policy.
As mentioned initially, there is no easy way to confirm that the device has successfully been offboarded unless you look at the registry key:
HKLM:\Software\Microsoft\Windows Advanced Threat Protection\Status\OnboardingState
and ensure that it is equal to 0. To assist with this I have created this free PowerShell script:
https://github.com/directorcia/Office365/blob/master/mde-offboard-check.ps1

That will show you the onboarding status as shown above.
Also, remember that the device will continue to be displayed in the Defender for Endpoint unless you use a display filter. Offboarding causes the device to stop sending sensor data to the portal but data from the device, including reference to any alerts it has had will be retained for up to 6 months.
If you want to offboard more devices you simply need to add them to the group you configured the offboarding Intune policy is assigned to. Remember, that after 30 days you’ll need to go and download a new offboarding package from the Defender for Endpoint console and upload the contents of the new WindowsDefenderATP_valid_until_YYYY-MM-DD.offboarding file to the offboarding Intune policy to allow devices to be successfully offboarded going forward. However, you can leave the policy in place and simply update it as and when needed.























