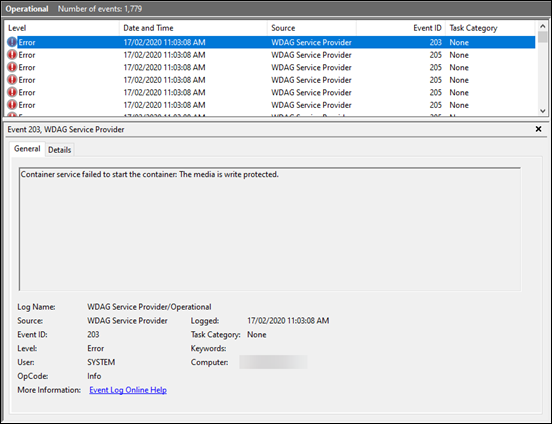
No interview this episode only news with Brenton and myself. Been a little while since we have chatted so a few things to cover off in the Microsoft Cloud and in general.
This episode was recorded using Microsoft Teams and produced with Camtasia 2019
take a listen and let us know what you think – feedback@needtoknow.cloud
You can listen directly to this episode at:
https://ciaops.podbean.com/e/episode-232-updates/
Subscribe via iTunes at:
https://itunes.apple.com/au/podcast/ciaops-need-to-know-podcasts/id406891445?mt=2
The podcast is also available on Stitcher at:
http://www.stitcher.com/podcast/ciaops/need-to-know-podcast?refid=stpr
Don’t forget to give the show a rating as well as send us any feedback or suggestions you may have for the show.
Resources
What’s new with Microsoft 365 February 2020
Staying on top of Office 365 updates
Update to Microsoft Authenticator