My experience with most Microsoft 365 environments I see is that they fail to make use of all the features that are provided. None more so when it comes to security. For example, most people don’t seem to appreciate that the Defender for Office 365 (which is part of Business Premium) provides impersonation protection for internal AND external email addresses! It just needs to be configured. The details are here:
Impersonation settings in anti-phishing policies in Microsoft Defender for Office 365
and as it says there:
You can use protected users to add internal and external sender email addresses to protect from impersonation.
but it is important to note:
User impersonation protection does not work if the sender and recipient have previously communicated via email. If the sender and recipient have never communicated via email, the message can be identified as an impersonation attempt.
This means, you want to get the configuration of important external email addresses in place as soon as possible so any impersonation against those users can be evaluated. It is too late to do after an internal user is communicating with a scam (impersonated) domain.
You will also see that you can also configure protection for external domains, rather than just specific email addresses, for impersonation evaluation.This means that if the users inside the tenant deal with an important business that has its own email email, that is NOT part of that tenant, you can enter that domain in here. Makes a lot sense when you are working with a business regularly that is doing stuff like invoicing, e-commerce or the like (honestly anything at all really).
Let’s say that I work with a business who’s domain is ciaops.com. By enabling this impersonation protection early, if users in the tenant receive email from c1aops.com then it is far more likely to be detected because the system is looking of for spoofing of that custom external domain I entered in the policy.
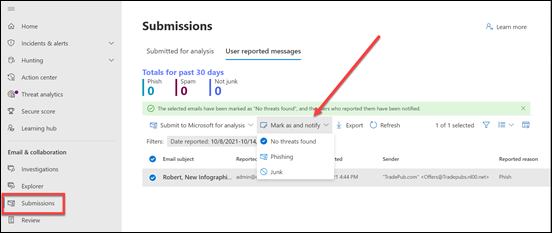
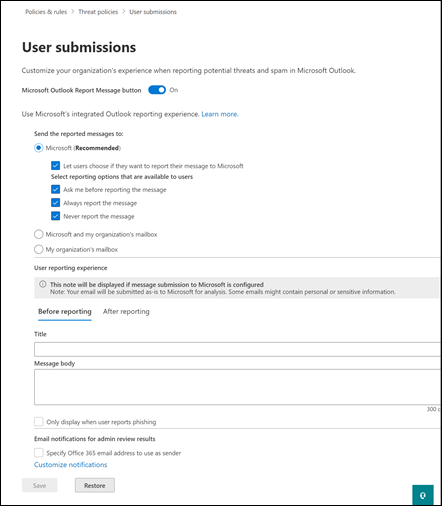
Thus, if you have Microsoft Defender for Office 365 in your environment (and you do if you have Microsoft 365 Business Premium), then you can provide an extra level of protection by configuring the Anti-Phishing policy for impersonation settings for both your important internal AND external usera and domains (i.e. people and businesses you work with regularly). You should do that as early as possible to provide the maximum protection the policy can provide. They key is that someone has to add in the unique email addresses or domains into the policy, they are not added automatically, even internal email address. They ALL have to be added to the policy.
You can protect up to 350 unique email addresses and 50 unique domains, which is probably more that enough to cover everything a smaller business would need for internal and external users. Unfortunately, I rarely see this great capability enabled. It’s available if you have Microsoft Defender for Office 365 so go configure it and reduce the risk to the users in the tenant. Easy!