Ok, so you are telling me you have time on your hands and want to improve the security of your Microsoft 365 tenant? Ok, if you are only kind of serious, I’d tell you to go to:
https://security.microsoft.com/securescore
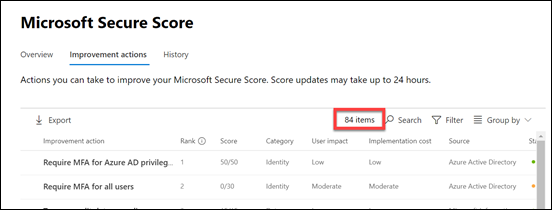
and select the Improvement actions as shown above.
That will show you a filtered view of items based on what hasn’t yet been completed in the tenant. In the case above, that equates to 67 items.
Oh, you want more to do you say?
Ok, if you remove that filter you’ll see the number in the list increase. In this case up from 67 to 84. That’s 36% increase in things you can address. Enough?
What? You want even more? Are you sure? Really sure?
Well, if you are, then the good news is that I have written a script for you that uses the Microsoft Graph to go in and grab all, and I mean ALL, of the secure score items. You’ll find the script in my Office 365 GitHub repo:
https://github.com/directorcia/Office365/blob/master/o365-ssdescpt-get.ps1
Now before you run this scripts, you’ll need to follow the instructions I have written about before:
Access the Microsoft Graph with a script
and set yourself up an OAuth token to access your tenant. You only need to do this once.
You’ll then need enter the values from this configuration into the script prior to running it:
You get these three items from the oAuth token set up I set out.
When run, the script will connect to the Microsoft Graph and start reading information from the Secure Score of YOUR tenant. It will also save the output to a text file in the parent directory. Why you ask?
Well, as you can see from the output from my tenant above, there are now potentially 6,972 items that I can go look at and configure to make my tenant more secure. That’s a 8,200% increase in things to keep you busy.
Remember, you did ask for more after all.






I suspect you may want to do some validation on the object returned by that call being made to the Graph and then recheck the total number of items actually available for remediation as a part of the Secure Score. The GET to /security/securescores returns an array of Secure Score collections for the target O365 tenant. Each collection is a snapshot of the tenant’s Secure Score assessment at a specific point in time (the visible when you open the History view in the Secure Score GUI), and each collection contains assessment data for that snapshot. When your script iterates through each of those collections to return their ControlScore descriptions, it does not only look at the most recent snapshot or remove duplicate entries and results in what looks like a greatly inflated final total count of items that can be secured.
LikeLike
Still an easy way to get lots of things you should check.
LikeLike
I believe that the list of items returned for a single Secure Score collection by the script you’re sharing should line up to the same unresolved items that the admin can see through the GUI in the Secure Score site. So in the case you show above, it would return 67 different items.
It is possible to query the Graph for *all* of the data points that Secure Score uses for its analysis, which would be via the /security/secureScoreControlProfiles/ endpoint. In my Targeted Release lab tenant I’m seeing about 122 different control profiles, which includes resolved and unresolved data points as well as several that are marked as deprecated (those total 21 items). I suspect that number varies from tenant to tenant, depending on the tenant’s release schedule as well as other functionality or features that have or have not been deployed to the tenant in question.
LikeLike