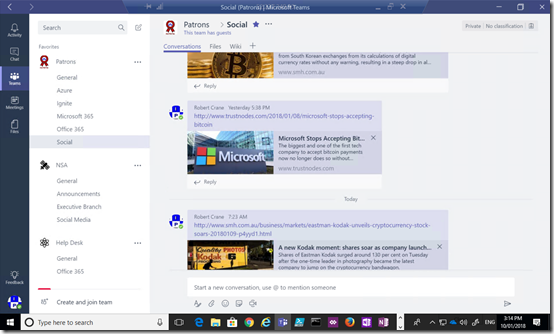
I have a Microsoft Team in my tenant called “Patrons”. In there is a channel called “Social”. In this area CIAOPS Patrons chat about things such a cryptocurrency as you can see.
As an administrator what I want to do is find out how I can view information that is shared by others in this chat location. In short, how do I see chat history in Microsoft Teams?
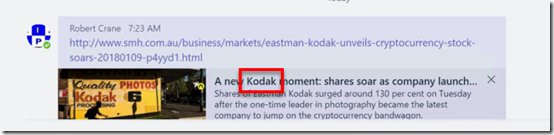
As an example, let’s say I want to find the term ‘kodak’ in these chats. You’ll see from the above that it is part of a link that was pasted into the chat.
All the chat history from Microsoft Teams is saved into a mailbox with the name of the Team. So I’m looking for a mailbox called “Patrons”.
Easiest way is to fire up trusty PowerShell and run:
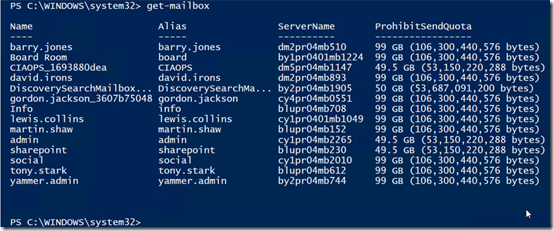
get-mailbox
and as you can see from the results above, I only see user mailboxes.
but if I run:
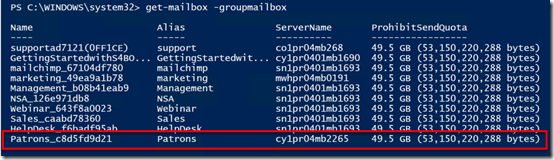
get-mailbox –groupmailbox
I see all the shared mailboxes in my tenant.
As you can see I find one called “Patrons” as shown above.
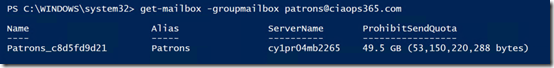
To get the details I run:
get-mailbox –groupmailbox patrons@ciaops365.com
and you can see that I again get all the information but just for that mailbox. So this is the one that is linked to my Microsoft Team.

If I now run:
get-mailbox –groupmailbox patrons@ciaops365.com | get-mailboxstatistics | select-object identity, itemsinfolder, foldersize
I basically get a report of what is inside that Teams mailbox. In there I can see a folder:
\conversation history\team chat
this is indeed where the chats are located. You can see there is currently 344 items of 4.38 MB in size.
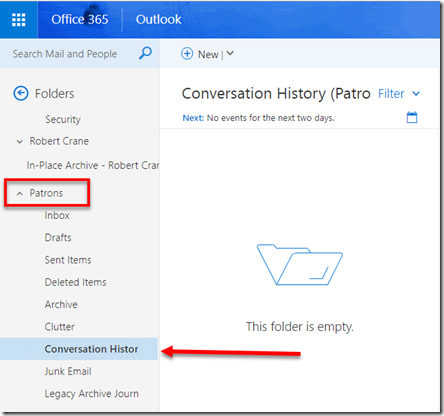
Now I can actually add this mailbox to my Outlook Web Access and view the contents as you can see above. However, I can’t get the folder \Conversation History\Team Chat because it is hidden and probably has other permissions associated with it.

I can’t add this shared mailbox to Outlook 2016 on my desktop as you can see above.

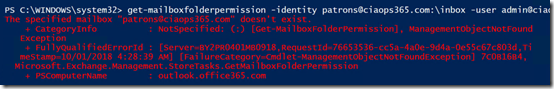
So now if I try to view/change the permissions on the mailbox using:
get-mailbox –groupmailbox patrons@ciaops365.com | get-mailfolderpermission
I get the message that the mailbox doesn’t exist.
If I now try:
get-mailfolderpermission –identity patrons@ciaops.com:\inbox
I again get the message that the mailbox doesn’t exist.
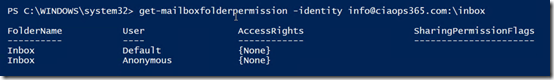
If I use that same command on another ‘standard’ shared mailbox the command works. So I know my command does work, it just doesn’t work with a Microsoft Teams mailbox.
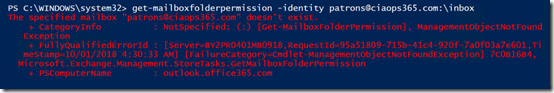
Again, just changing mailbox identity confirms that the command can’t even see the mailbox.
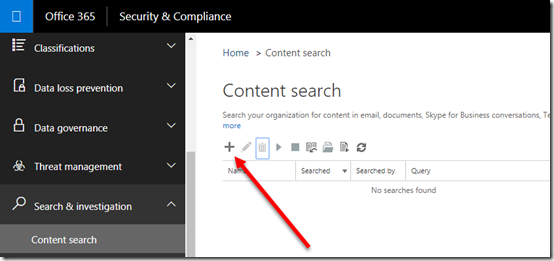
The way to actually see what the contents of the Teams chats are is to use the Content Discovery component of the Security & Compliance center in Office 365 which you’ll find under the Search & Investigation heading on left hand side. You need to be an administrator with appropriate rights to access this area.
You start by creating a new Content Search by pressing the + icon as shown above.

Give the new Content Search a title and select the locations where you wish to search. In this case I’ll simply look through all email data.

Next, I enter what I want to search for. Here, I’m only looking for the word ‘kodak’.

After I finish my configuration, the search commences and I need to wait a few moments while it searches all the nominated locations and generates the results.

When the process is complete I select the Preview search results hyperlink on the right as shown above.
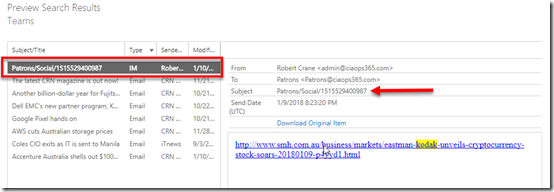
Another window opens and I can locate the item I’m after as the type is ‘IM’ as shown above. When I select that item on the left I see the full context on the right. I confirm that the search does display the link that is the Microsoft Team chat.
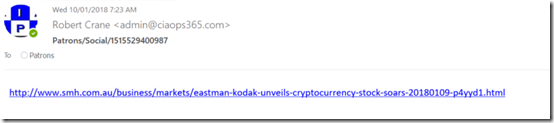
If I elect to download the item, it does so as an .EML file which I can open in any mail client as shown above. This indicates that each chat message appears to be a separate email in a sub folder in a shared mailbox in Exchange Online effectively.
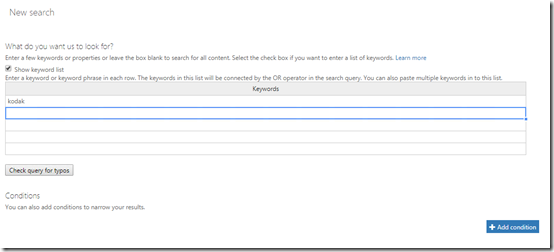
So I went back in and changed the content search terms to make it broader to encompass more chats.
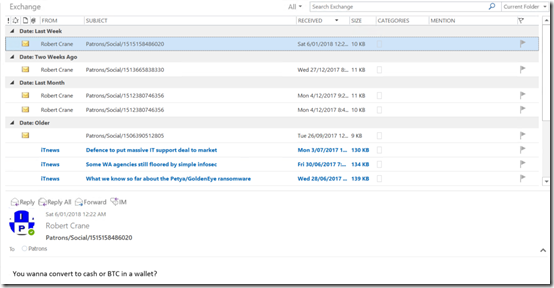
I ran the search and exported the data from the Security & Compliance center into a .PST file and then imported that into Outlook.
Thus, as you can see above, I can now view all the chats that match my search criteria as an administrator.
The problem with this is, from a pure ‘overwatch’ point of view, it is a very manual process to get to the information and secondly you can only look at things you specify in your content search. It would be nice to have the ability for an administrator to export the whole chat content from a Microsoft Teams channel into a single document that could then be viewed.
However, at the end of the day, rest assure that your Microsoft Teams chats are being saved and you can access them if you need to. Hopefully, the above has shown you how to do exactly that.