One of the many things I say is that you should not think of Office 365 or Microsoft 365 alone, you should think of incorporating services like Azure as well since they provide a huge amount of additional functionality as I have detailed here before:
Add Azure to Office 365 for more flexibility
As I have also pointed out, I believe you should deploy Azure immediately with Office 365
Deploy Office 365 and Azure together
because until you start using Azure it isn’t going to cost you anything since Azure billing is typically consumption based. That is, you are only billed for what you use.
Now, one of the ways that you can use Azure to take advantage of the automation abilities it has. This is really handy when you want to run repeated process. One such process that you should run regularly I believe is checking for mailbox forwards in Office 365 tenants. I have detailed how to do manually this using a PowerShell script here:
PowerShell script to check email forwards
So, thanks to Azure automation we can take the heart of this script and automate it to run regularly against our tenant and provide an email report on which mailboxes have forwards enabled. Thus, Azure Automation allows us to automate the execution of PowerShell scripts to make life easier.
To enable all this you are going to need to use an Azure account with a paid subscription. It doesn’t have to be the same tenant as the Office 365 one, it just has to be a tenant with a paid subscription because there are costs (very slight) to running Azure Automation.

Once you have logged into you Azure tenant locate the Azure Automation Accounts and select the Add button in the top left to create a new account to use.

Give the new Azure Automation Account a name, paid subscription, resource group and location. Then select Create.
Once created, you’ll see an overview of the new account as shown above.
From the menu on the left locate Modules and select it.

Because this is a new automation account it will only have the standard PowerShell modules included. We need to go and add the one for Office 365.
We can find the Office 365 PowerShell module by selecting the option to Browse gallery from the buttons across the top on the right.

Do a search for “online” and the first result should be MSOnline as you see above.
Select this module to add it.
You should now see more detail about the module displayed. Select the Import button at the to of the page to include that module in this new Automation Account.
In a few moments you should get a message letting you know the module has been imported successfully. Remember, you only need to do this once for any new Automation Account that you wish to run commands against Office 365.

Return to the list of items for the Automation Account and locate the option for Credentials and select it. It is a few below the Modules one you just selected.
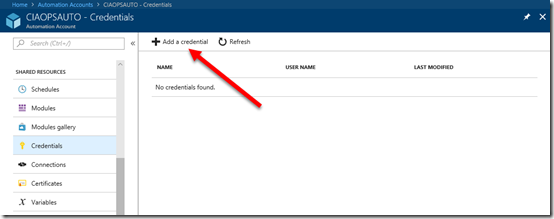
Select Add a credential at the top of the page.
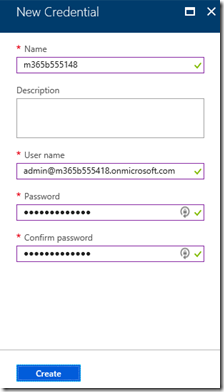
Now enter the user details for the user who is going to login to the Office 365 tenant when executing the script. This will typically be a global administrator that doesn’t have MFA enabled on the account. The credentials are stored securely in Azure and will be accessed with the name of the credential account you used (here m365B555418).
Generally, you will only need one set of credentials in your Automation Account but it is possible to have as many as you want for performing different tasks.
Select Create to complete this process.

From the Automation Account menu locate Runbooks and select it.

From the menu across the top select Add a runbook.
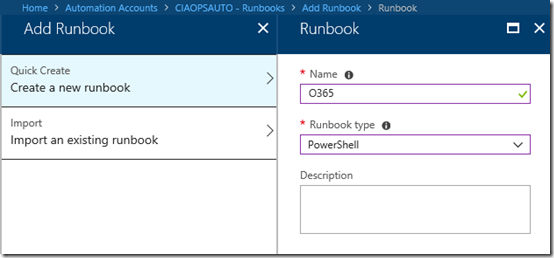
Select the option to Create a new runbook. Give the runbook a Name and select the type as PowerShell. Then select Create to establish the area for your code.

This should then take you to an editor where you can enter your code as shown above.
Rather then re-inventing the wheel you can use my code here:
https://github.com/directorcia/Azure/blob/master/runbook/scripts/O365.ps1
which you can just copy and paste in place.
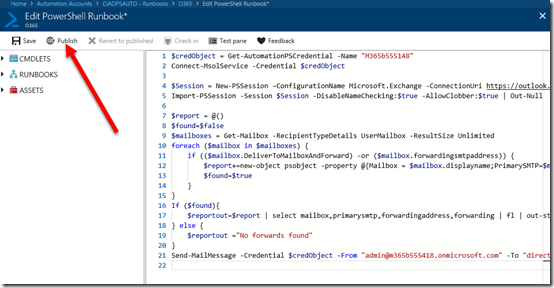
With that done, your screen should look like the above.
A few things to note here. Ensure that you change the name in the first line of the code to match the name of the credential you created earlier because it is from here that the login details for the Office 365 tenant will be sourced. You will also need to change email addresses on the last line of the script to match your environment. Remember, if you don’t I’ll know who it is!
The code is pretty short and sweet. All it does is look for any account that has any sort of forward enabled and sends those details through. If no forwards are found you’ll also get a message indicating that.
Feel free to modify and improve the script as you see fit, this version is simply designed to demonstrate what is possible.
When you have finished editing your script, select Publish in the top left as shown. Remember to always do this anytime your code changes or is updated.
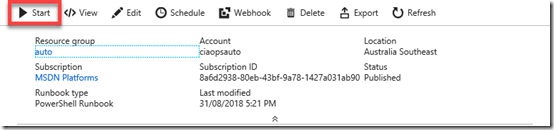
You’ll now be taken back to to the Runbook overview. Here, select the Start button in the menu to run the script immediately.
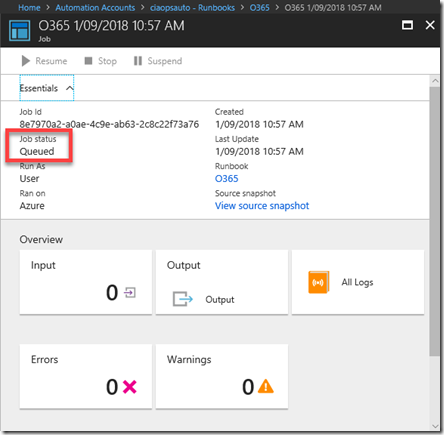
You will now be taken to the Job summary page as shown above. You can check on the progress of the job from the Job Status field as shown.
The job will first be queued and then run.

In a matter of moments the job should complete as you see above. If there are any errors or exceptions with your code then they will be visible in this summary page.

If everything went to plan, you should see an email like that shown above indicating the process has completed successfully.

Each job run is recorded in a log on the summary page as shown above. Clicking on that job will give you more details.

Now, we started this whole process with the aim of automating something so now we need to do this once we have confirmed our script is running as expected.
From the Runbook menu across the top select Schedule.
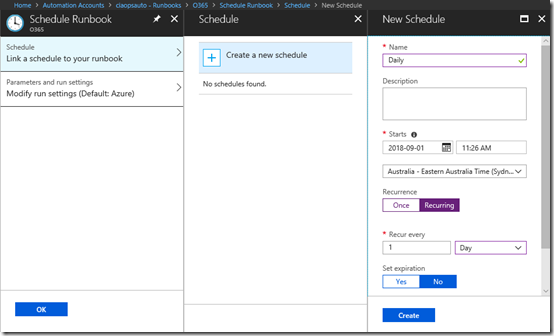
Complete your desired schedule for this process. Typically, it will be daily as shown above. When you have configured the desired options select Create and your job will now run on that schedule.
You can return to Azure Automation at any time to view and adjust your job but always remember to Publish your code if you make any changes.
Hopefully, I’ve shown you how straight forward it is to use Azure Automation with PowerShell scripting to target regular processes for you Office 365 tenants. There are many, many things you can automate thanks to PowerShell and Azure, so go forth and automate!