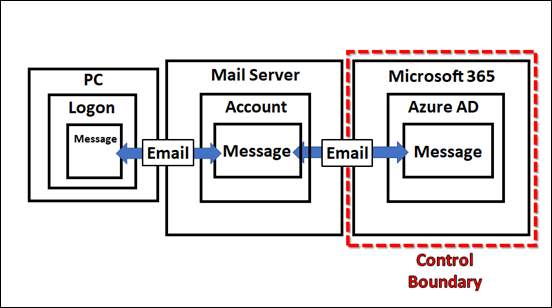
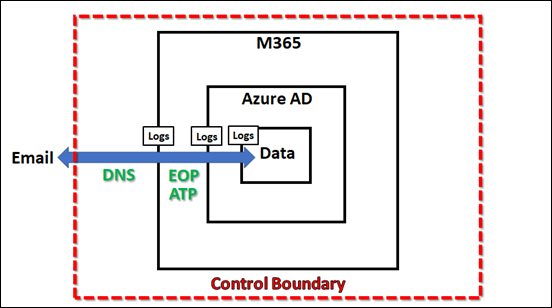
Security is never an absolute and is largely about defence in depth. That is, adding more layers of protection. With this in mind, I was recently made aware of this little gem that can help provide just a little more protection for inbound emails, especially against inbound malicious attachments.
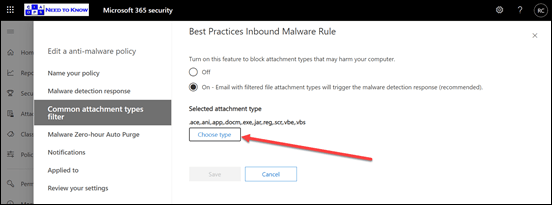
Exchange Online has a Malware policy that you can configure. You’ll find it in the Microsoft 365 security center under policies. When you edit that policy, as shown above, you’ll see an option for Common attachment types filter. You should ensure that this is set to On. If so, you can then select the Choose type button to select which attachment types will be blocked.
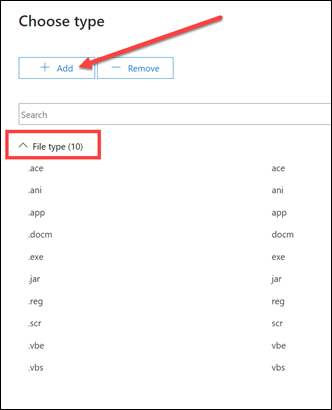
You’ll see there are about ten default file types that will be blocked. What you may not be aware of is that if you press the Add button at the top of the page, as shown above,
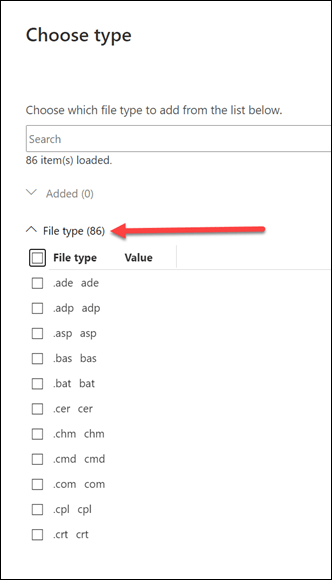
There are an additional 86 file types that Microsoft allows you to directly add.
Just select them all and Add them.
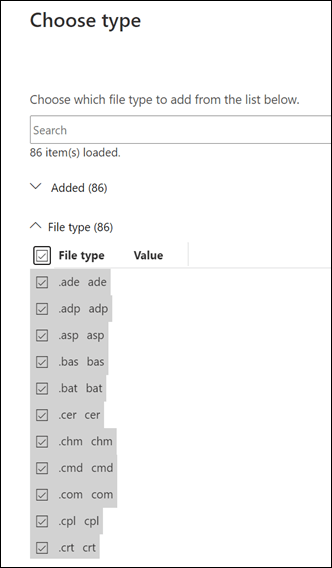
You should then see a total of 96 file types listed in the policy as shown.
I was a little puzzled why Microsoft wouldn’t have added more of the 86 optional files types to the standard 10? Most of the option 86 seem to be developer focused so maybe that is why? Many of the optional 86 are quite antiquated but that doesn’t mean they couldn’t be used somehow to compromise an environment. Thus, it is therefore probably a very good idea to block all these 86 option file types on top of the default 10 it seems.
I also had a quick look at what all these filetype typically refer to and provide this summary for you:
– ade https://www.file-extensions.org/gadget-file-extension
– adp https://www.file-extensions.org/adp-file-extension
– asp https://www.file-extensions.org/asp-file-extension
– bas https://www.file-extensions.org/bas-file-extension
– bat https://www.file-extensions.org/bat-file-extension
– cer https://www.file-extensions.org/cer-file-extension-internet-security-certificate
– chm https://www.file-extensions.org/chm-file-extension
– cmd https://www.file-extensions.org/cmd-file-extension
– com https://www.file-extensions.org/com-file-extension
– cpl https://www.file-extensions.org/cpl-file-extension
– crt https://www.file-extensions.org/crt-file-extension
– csh https://www.file-extensions.org/csh-file-extension-csh-script
– der https://www.file-extensions.org/der-file-extension
– dll https://www.file-extensions.org/dll-file-extension
– dos https://www.file-extensions.org/dos-file-extension
– fxp https://www.file-extensions.org/fxp-file-extension-adobe-flash-builder-project
– gadget https://www.file-extensions.org/gadget-file-extension
– hlp https://www.file-extensions.org/hlp-file-extension
– Hta https://www.file-extensions.org/hta-file-extension
– Inf https://www.file-extensions.org/inf-file-extension
– Ins https://www.file-extensions.org/ins-file-extension
– Isp https://www.file-extensions.org/lsp-file-extension-autolisp-language-source-code
– Its https://www.file-extensions.org/its-file-extension-internet-document
– js https://www.file-extensions.org/js-file-extension
– Jse https://www.file-extensions.org/jse-file-extension
– Ksh https://www.file-extensions.org/ksh-file-extension
– Lnk https://www.file-extensions.org/lnk-file-extension
– mad https://www.file-extensions.org/mad-file-extension
– maf https://www.file-extensions.org/maf-file-extension
– mag https://www.file-extensions.org/mag-file-extension-microsoft-access-diagram-shortcut
– mam https://www.file-extensions.org/mam-file-extension
– maq https://www.file-extensions.org/maq-file-extension
– mar https://www.file-extensions.org/mar-file-extension
– mas https://www.file-extensions.org/mas-file-extension
– mat https://www.file-extensions.org/mat-file-extension
– mau https://www.file-extensions.org/mau-file-extension
– mav https://www.file-extensions.org/mav-file-extension
– maw https://www.file-extensions.org/maw-file-extension
– mda https://www.file-extensions.org/mda-file-extension
– mdb https://www.file-extensions.org/mdb-file-extension
– mde https://www.file-extensions.org/mde-file-extension
– mdt https://www.file-extensions.org/mdt-file-extension
– mdw https://www.file-extensions.org/mdw-file-extension
– mdz https://www.file-extensions.org/mdz-file-extension
– msc https://www.file-extensions.org/msc-file-extension
– msh https://www.file-extensions.org/msh-file-extension
– msh1 https://www.file-extensions.org/msh1-file-extension
– msh1xml https://www.file-extensions.org/msh1xml-file-extension
– msh2 https://www.file-extensions.org/msh2-file-extension
– msh2xml https://www.file-extensions.org/msh2xml-file-extension
– mshxml https://www.file-extensions.org/mshxml-file-extension
– msi https://www.file-extensions.org/msi-file-extension
– msp https://www.file-extensions.org/msp-file-extension
– mst https://www.file-extensions.org/msstyles-file-extension
– obj https://www.file-extensions.org/obj-file-extension-microsoft-visual-studio-object
– ops https://www.file-extensions.org/oxps-file-extension
– os2 https://www.file-extensions.org/os2-file-extension
– pcd https://www.file-extensions.org/pcd-file-extension-microsoft-visual-test-data
– pif https://www.file-extensions.org/pif-file-extension
– plg https://www.file-extensions.org/plg-file-extension
– prf https://www.file-extensions.org/prf-file-extension-microsoft-outlook-profile
– prg https://www.file-extensions.org/prg-file-extension-program
– ps1 https://www.file-extensions.org/ps1-file-extension
– ps1xml https://www.file-extensions.org/ps1xml-file-extension
– ps2 https://www.file-extensions.org/ps2-file-extension
– ps2xml https://www.file-extensions.org/ps2xml-file-extension
– psc1 https://www.file-extensions.org/psc1-file-extension
– psc2 https://www.file-extensions.org/psc2-file-extension
– pst https://www.file-extensions.org/pst-file-extension
– rar https://www.file-extensions.org/library-ms-file-extension
– scf https://www.file-extensions.org/scf-file-extension
– sct https://www.file-extensions.org/sct-file-extension
– shb https://www.file-extensions.org/shb-file-extension
– shs https://www.file-extensions.org/shs-file-extension-microsoft-windows-shell-scrap-object
– tmp https://www.file-extensions.org/tmp-file-extension
– url https://www.file-extensions.org/url-file-extension
– vb https://www.file-extensions.org/vb-file-extension
– vsmacros https://www.file-extensions.org/vsmacros-file-extension
– vsw – https://www.file-extensions.org/vsw-file-extension
– vxd – https://www.file-extensions.org/vxd-file-extension
– w16 – https://www.file-extensions.org/w16-file-extension
– ws – https://www.file-extensions.org/ws-file-extension
– wsc – https://www.file-extensions.org/wsc-file-extension
– wsf – https://www.file-extensions.org/wsf-file-extension
– wsh – https://www.file-extensions.org/wsh-file-extension
– xnk – https://www.file-extensions.org/xnk-file-extension
Thus, I’d recommend you update your Exchange Online policy to include the complete of file types that Microsoft provides protection for, even if most aren’t enabled.