DLP or Data Loss Prevention is a way inside Office 365 (E3 suites or above) that you can protect data from leaving the organisation. You can use DLP to protect not only email attachments but also files in SharePoint Online Team Sites and user’s OneDrive for Business.
Office 365 provides a number of standard templates for protecting standard information, such as credit card information as detailed here, but you can also customise the DLP policies to protect any custom data you wish.
The first step in using DLP is to set up and enforce the policies you wish to use. To do this you’ll need to login to the Office 365 portal as an administrator with the appropriate rights. You’ll then need to navigate to the tenant Admin area. From the menu on the left hand side of the screen expand the Admin centers option. From the options that appear select the Security & Compliance item.
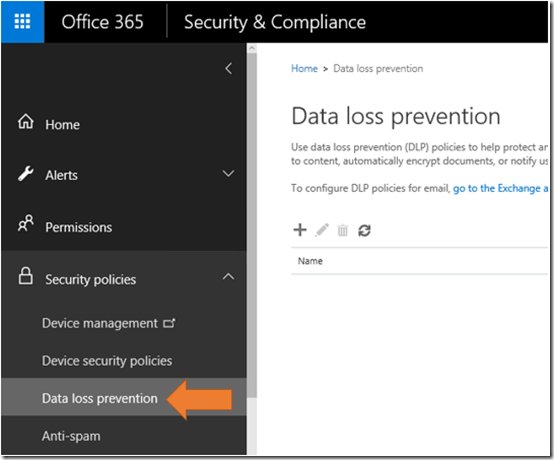
From the Security and Compliance console select Security policies on the left. From the options that then appear below this select Data loss prevention. If this menu item doesn’t appear then you current don’t have an Office 365 plan that supports DLP.
On the right hand side you will probably see that the list is empty. Select the Plus icon to create a new policy.
You can select from a number of templated policies if you wish but in this case select Custom and then the Next button.
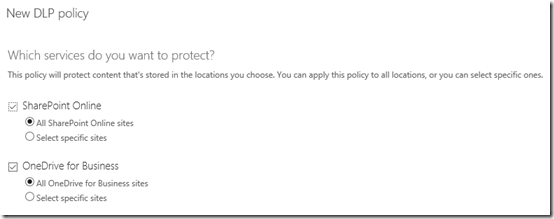
You now need to select the areas in which this policy will apply. You can specify unique locations but for this example we’ll simply select all locations and then continue.
At the next screen select the Plus icon to set the rules for which you wish to test.
In the new window that appears select the Add condition button.
From the pull down menu that appears select Content containing sensitive information.
Select the Plus icon that appears to enter the actual rules.
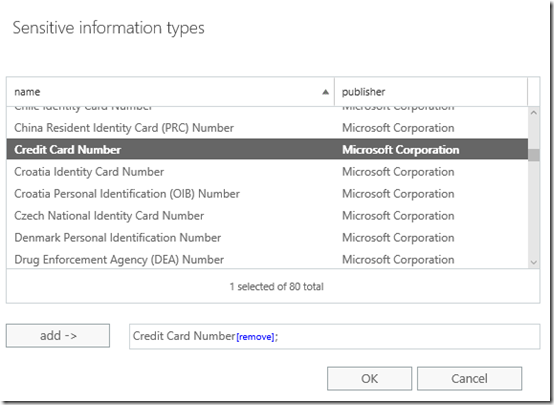
Scroll down the list that appears and select Credit Card Number. You can select other items here but in this case all we want this example DLP rule to test for is credit card numbers.
Select OK to continue.
You should now see the entry appear in the list as shown above. You can edit this entry if you wish by selecting it and then pressing the Pencil icon (edit).
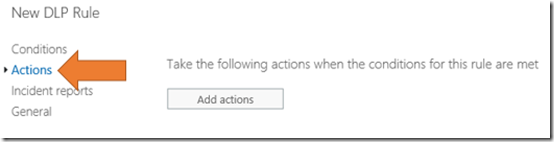
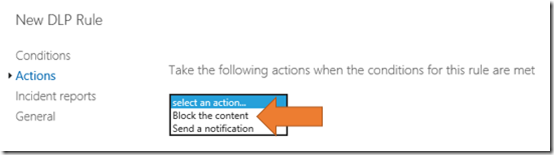
Select the Actions item from the menu on the left.
Select the Add actions button on the right.
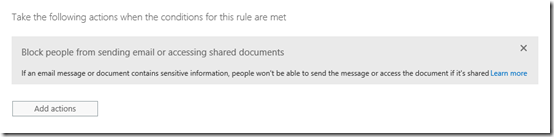
In this example, select Block the content. This will prevent anything that matches this rule from being shared.
You should now see the blocking Action listed as shown above.
Select the Incident report option from the menu on the left. Enter the details if you wish to receive a report of any actions on this policy.
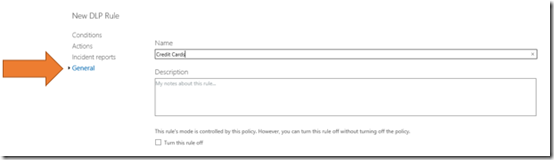
Select General from the menu on the left. Give this set of rules a name and save them.
You should now see the rules listing appear as shown above in the DLP policy you just created. You can create as many of these rules inside a single policy as you wish. However, best practice is always to keep it simple.
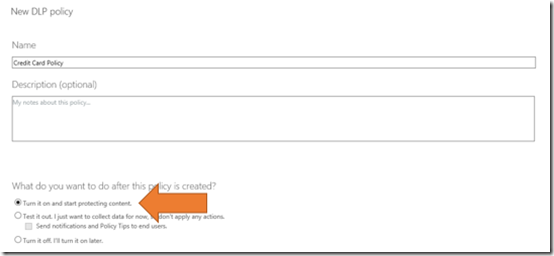
Give the DLP policy and name and select the option to Turn on the policy.
Select the Create to complete the policy creation process.
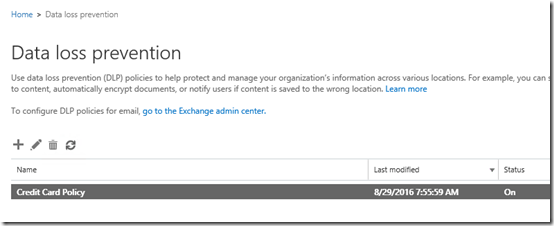
You should now see the policy listed in the DLP area as shown above. You should also see that the Status is set to On.
The DLP policy will not come into effect immediately. It will take a little while (15 – 30 minutes typically in my experience) to roll out through your tenant.
To test the policy, create a document in your OneDrive for Business that contains credit card numbers as shown above. The numbers used here are verified public ‘test’ card numbers.
Now create a public View link that requires no sign-in as shown above. This should allow anyone who clicks on that link direct access to the file without the need of a login or password.
When the DLP policy is active anyone trying to access that link will have the content blocked as shown above. This confirms that teh DLP policy is working as expected.
If you also elected to get alerts you should fine one in your inbox as shown above.
Thus, DLP is a way to protect your Office 365 information by examining the contents against a set of rules that you create. It can examine both email and file data then take actions which you determine.
DLP is part of the E3 or better suite in Office 365.