The question of whether you need to backup data (emails and files) stored in Office 365 is one of the most common questions I see. The best answer is that you need to have as many backups of your own data as you feel comfortable with. That comfort level will vary with each person and business, but in general, more is better.
Let’s start by defining what most people consider to be “traditional” backup. A “backup”, for this definition, is a full copy of your data at a point in time that allows you to easily do a single item restore (such as a single email or file) if required, to the original or alternate location, that is retained for an extended (greater than 30 days) period of time. If this is the type of backup you wish to have then you should look at using a third party tool to supplement the way Office 365 retains your data.
Microsoft is indeed able to restore your data if required but how they do is very different from what people may appreciate. Microsoft also does not publicly publish the specific process by which it backups up information in its data centers, however it certainly does backup your data as shown here:
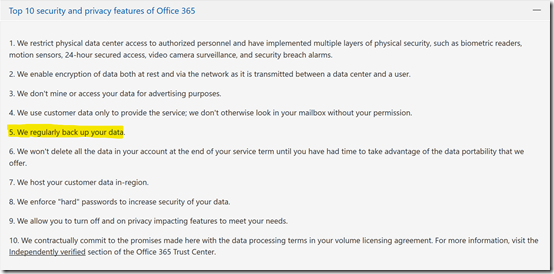
Which can be found at – https://products.office.com/en-au/business/office-365-trust-center-top-10-trust-tenets-cloud-security-and-privacy
Also in “Protecting Privacy and Data” – http://download.microsoft.com/download/2/0/A/20A1529E-65CB-4266-8651-1B57B0E42DAA/Protecting-Data-and-Privacy-in-the-Cloud.pdf (page 3) you will find the following statement about Microsoft Online Services:
“Additionally, each service has established a set of standards for storing and backing up data, and securely deleting data upon request from the customer.”
Office 365 is also certified to many industry standards which you can read about here:
https://products.office.com/en-au/business/office-365-trust-center-compliance-certifications
These contain standards around maintaining data within its services. With all this, you should then feel completely at ease with the fact that Microsoft is indeed protecting your data in many different ways, to industry leading standards or better, one of which is the process of backup. It is important to however understand how the common initial “traditional” definition of backup highlighted above may be different within Office 365.
If needed, Microsoft are not going to restore a single item, such as one email message back into a mailbox. They will however restore a full mailbox for you back to a point in time. Also, they will not be able to restore a whole mailbox from say 12 months ago because, as you can appreciate, the amount of data storage required to provide this across all mailboxes in Office 365 would be enormous. Thus, if you have a need to have Microsoft restore a whole mailbox, you’ll need to typically request that as soon after the event as possible and do so by logging a support ticket with Microsoft.
Likewise with SharePoint. Microsoft won’t generally restore a single file into a document library, they will restore the whole site collection or OneDrive for Business back to a point in time provided it is within a recent time window. To do this, you’ll need to once again raise a service ticket with Microsoft.
Another point to remember with restores completed by Microsoft, for mailboxes and SharePoint sites, is that the restore will be over what is already in place. That is, restored data will be to the original location. Restored data from Microsoft cannot be recovered into an alternate location for comparison.This means that this will erase any current information in that location and replace it with everything from the restore. Thus, the data will be rolled back to that moment in time for a whole mailbox or site collection.
Thus, if you are looking for single item recovery of deleted items like files and email messages and/or items that are beyond the default Office 365 retention periods (for example from 12 months ago), then you need to consider a third party backup tool that you purchase, configure, manage and maintain yourself. Also, if you are looking to restore a whole mailbox, SharePoint site collection or OneDrive for Business without logging a support ticket with Microsoft, then you need to consider a third party tool. Also, if you wish to control where the destination of the backed up data is, you will again need to consider a third party solution. Finally, if you want granular control over the schedule of when backups actually take place, then you need to look at a third party backup solution.
Office 365 typically maintains data using a retention process. This means that Office 365 will make sure the data is made available but it does not generally keep a copy of that data forever. In essence, old deleted data will be aged out and eventually purged from the service after a period of time. That period of time varies by service as well as the license assigned to that data. There are however features that are part of the more advanced licenses and available as add ins, such as Litigation Hold that can be used to retain data indefinitely. The important difference here is “traditional” backup versus retention. For an overview of Office 365 retention policies see:
https://docs.microsoft.com/en-us/office365/securitycompliance/retention-policies
The important thing people need to understand is what protection does Office 365 provide them out of the box and do they need to supplement that? Take OneDrive for Business and SharePoint for example. Every time you update a file in either of these two services a previous copy of the file is kept. This allows the user to easily roll back to a previous version of that file if needed. By default, and this can be changed, Office 365 will retain 500 copies of previous version of a file. Once it reaches that limit it will commence over writing the oldest version.
Having version history in SharePoint and OneDrive for Business means that you can “recover” older items quickly and easily. You can also recover a whole OneDrive for Business quickly and easily using this recent feature:
https://support.office.com/en-us/article/restore-deleted-files-or-folders-in-onedrive-949ada80-0026-4db3-a953-c99083e6a84f
That same feature will soon be available for SharePoint document libraries.
Next, let’s take a look a what happens when you delete a file in OneDrive for Business or SharePoint online. Once a file is deleted it goes to the user’s recycle bin where it can be recovered if needed. If it is removed from the user recycle bin it goes to an administrator recycle bin. The total time that a file is retained across these recycle bins is 93 days. After that the file is purged from the system. I have outlined this process in depth in this article:
https://blog.ciaops.com/2018/03/using-retention-policies-in-office-365.html
What about deleted emails? An email that is deleted from the inbox is sent to the deleted items folder for that mailbox and retained there indefinitely. If it is removed from the deleted items folder it can be recovered for up to 14 days by default, which can be extended to 30 days via PowerShell. After that the email is purged from the system. I have detailed how to extend the default period to 30 days using PowerShell here:
https://blog.ciaops.com/2018/03/extending-exchange-online-deleted-items.html
Now the time that both of these processes retain for can be extended. In the case of OneDrive for Business and SharePoint you can use labels and retention policies to effectively maintain that data forever. With emails you can add the Litigation Hold feature to achieve basically the same effect. Thus, with either some additional configuration or additional license, Office 365 can retain data for a very long time. However, you need to appreciate that this is retention not backup as we defined it earlier.
What’s the difference between retained and backed up data in this context? If you enable extended retention policies for file data in SharePoint Online and OneDrive for Business beyond the default period, the information is kept in something called a Preservation Library. The challenge with this is there is only one Preservation Library per site. This means all the retained data is lumped into this one location. That can make finding a single file to restore a challenge. Preservation Libraries are also generally only available to administrators not end users.
In the case of deleted emails an administrator would need to use a tool like eDiscovery search to recover the deleted items. The items will certain be available but the structure they resided in would not be. Thus, if you deleted a file from your inbox that was stored a number of sub folders below the inbox, those folders would not typically be recovered using this eDiscovery process typically.
As you can see, there is a difference between what many people consider backup and the way that Office 365 retains data and how it can be accessed. In many cases it can be as good as a backup, however if your requirement for backup is what was defined initially, then implementing a third party tool is probably recommended. The downside to implementing a third party tool is that you need to pay, configure and maintain this. This means the additional cost of this needs to be weighed up against how often it will actually be required and what situations it provides protection above and beyond what Office 365 does. That is a decision that each business needs to make for themselves. This is a risk management decision.
In all of this you’ll also need to consider that Office 365 is fast becoming more than simply emails and files. It is Teams with chat, it is Yammer with discussions, it is Sway with presentations, Planner with tasks, and so on. No third party tools I know of will in fact backup these Office 365 services in any way. As the use of these additional services continues to grow, this means that you are going to have to rely on the processes that Microsoft has in its back end to potentially recover your data if required. At this point in time, there is no other option.
Of course, some features like Litigation Hold require a more advanced license, like Exchange Online Plan 2 but generally you don’t just get the one feature with these advanced licenses, you get a range of additional features. Thus, if you want Litigation Hold and upgrade a mailbox to Exchange Online plan 2 not only do you get Litigation Hold but you also get unlimited archiving as part of that upgraded license. Compare this for paying for a third party backup solution which generally only gives you the option to backup data and doesn’t provide much in the way of end user functionality. Also, chances are that you will rarely need that backup however the added features of advanced license can improve productivity for your end user every day.
In a perfect world, yes, you would add additional backup capabilities to Office 365 because more backups are better. However, we live in a world where compromises need to be made for different business reasons. We need to make decisions based on business risk. Thus, you need to balance risk with the offset mitigation cost and return on investment. Personally, if I had to choose between having a third party backup solution or upgrading an existing Office 365 license to include more functionality, I’d fall into the camp of providing users with additional day to day functionality. This is because I understand what Office 365 does. I understand how to get the maximum retention and recovery from what is provided out of the box and by adding advanced licenses to Office 365 and I am happy with that. I don’t believe adding third party backup software provides more value than what Office 365 can provide. Yes, I understand there maybe circumstances that may not be optimal but given how likely that circumstance may be, I believe that choice to be circumspect.
In summary then, yes, Office 365 does backup your data. However, the way that backup takes place and how it can be used to recover information is probably different many people’s “traditional” concept of backup. It is therefore important to understand:
- What Office 365 provides out of the box
- What additional configurations can be made to Office 365 to improve that
- What Office 365 services can be added to improve or enhance what is provide by default
Only after completing these steps should you consider adding additional third party backup solutions if appropriate.
 =””>
=””>