Executive Summary: Small and mid-sized businesses (SMBs) increasingly rely on cloud services and remote work, raising the question: Is it still worthwhile to invest in expensive firewall appliances, or can Microsoft 365 Business Premium’s security features suffice alongside a basic router firewall? This report finds that with Microsoft 365 Business Premium fully configured for security, most SMBs can rely on its comprehensive protections and a standard network firewall, rather than purchasing high-priced dedicated firewall devices. Modern security has shifted from perimeter-focused hardware to a multi-layered “Zero Trust” approach built into cloud and endpoint solutions[1][2]. We detail how Microsoft 365 Business Premium’s advanced security—identity protection, device and endpoint defense, email threat filtering, and data controls—can reduce or eliminate the need for standalone firewalls, especially for distributed workforces. A comparison of features, costs, and effectiveness is provided to guide decision-making.
The Traditional SMB Firewall Approach: Role and Limitations
High-priced firewall appliances (often called “next-generation firewalls” or unified threat management devices) have long been a staple of SMB IT security. These hardware devices sit at the network perimeter (e.g. office internet gateway) to inspect and filter traffic. Key capabilities of a typical advanced firewall include:
- Network Traffic Filtering & Intrusion Prevention: Scanning incoming/outgoing data packets for malicious signatures or anomalous patterns, blocking attacks before they reach internal systems. For example, a firewall can stop external hacking attempts or deny access to known malicious IP addresses[1].
- Web Content Filtering and URL Blocking: Many SMB firewalls offer category-based filtering to block dangerous or inappropriate websites enterprise-wide. This helps prevent users from accessing malware-hosting sites—but only when device traffic passes through the firewall.
- VPN Server for Remote Access: Firewalls often provide VPN capabilities so remote workers can “tunnel” into the office network securely. This was crucial when on-premises servers and network drives were the norm.
- Application Control and QoS: High-end models recognize and control applications (e.g. blocking peer-to-peer file sharing, prioritizing VoIP traffic) to secure and optimize network use.
- Email/Spam Filtering and AV Proxy: Some UTM devices can scan email or web downloads for viruses and spam (though in cloud email setups, this may be bypassed).
- Segmentation and Monitoring: They allow creating network zones (e.g. guest Wi-Fi vs internal) and monitoring internal traffic flows for suspicious lateral movement.
Value: In a classic office-centric environment, these capabilities provided a strong perimeter defense. A firewall can act as a single choke point to enforce security policies for all devices on the office LAN. For example, it might stop a ransomware attack from reaching a vulnerable PC, or log an intrusion attempt on the server.
However, the traditional firewall model has significant limitations in today’s SMB context:
- Dissolving Network Perimeter: With many employees now working from home offices, coffee shops, and client sites, much of their internet traffic never traverses the office firewall[1]. If remote users connect to cloud apps (Microsoft 365, Salesforce, etc.) directly, a firewall at HQ doesn’t see or filter that traffic. The perimeter “doesn’t exist” when data is spread across cloud services and roaming devices[1].
- VPN Dependency: Firewalls can protect remote users only if those users VPN into the office network consistently. In practice, forcing all remote traffic through a VPN and firewall is cumbersome and can slow things down. Many SMBs find users connect via VPN only for specific internal resources, leaving general internet use uninspected. Stolen or weak VPN credentials have also become a common breach vector[1].
- Blind Spots to Identity and Devices: A firewall makes binary decisions based on IP addresses and ports, but it cannot verify user identities or device health. Once a connection is allowed (e.g. an employee VPNs in), traditional tools assume trust internally[1]. If an attacker steals a valid user’s credentials or if a legitimate laptop is infected, the firewall might not detect the resulting malicious activity.
- Encrypted Traffic and Cloud Services: An increasing share of traffic is encrypted (HTTPS). Firewalls can perform deep inspection only by doing SSL decryption (complex to set up and a potential privacy issue) or relying on reputation feeds. They also can’t inspect data stored in cloud services (e.g. files in OneDrive) for sensitive info leaks – that requires cloud-native solutions.
- Cost and Complexity: A quality next-gen firewall appliance can be expensive (several thousand dollars plus annual subscriptions for threat updates). Managing it requires expertise to tune rules and review alerts. For resource-constrained SMB IT teams, this can be challenging. Misconfigurations or missed updates can undermine the very protection it’s supposed to provide.
Trend – Beyond the Firewall: Modern security thinking recognizes that “firewalls were built for a perimeter that doesn’t exist anymore”[1]. With data in SaaS apps and employees everywhere, the new approach is Zero Trust: assume attackers might already be in or that any network is unsafe, and verify each user, device, and access continuously rather than relying solely on a gate at the network edge[1][1]. This is where Microsoft 365 Business Premium’s security features come in, aligning security to users and devices instead of a single office pipeline.
In summary, a basic firewall (for example, the built-in firewall on a router or Windows Defender Firewall on devices) is still necessary for baseline protection (blocking unsolicited inbound traffic, network address translation, etc.). But investing in high-priced, feature-rich firewall devices yields diminishing returns if your apps are cloud-based and your workforce is largely remote. The security focus for SMBs has shifted to protecting identities, endpoints, and cloud workflows – areas where Microsoft 365 Business Premium provides extensive capabilities, as we explore next.
Microsoft 365 Business Premium: A Comprehensive Security Suite
Microsoft 365 Business Premium (M365 BP) is an integrated offering that bundles Office productivity apps with a robust set of enterprise-grade security and management tools tailored for SMBs[3]. When fully configured, M365 Business Premium addresses many security layers that a firewall would, and in some cases goes further by protecting beyond the network boundary. Key security components include:
- Azure AD Premium P1 (Identity and Access Management): Business Premium includes Azure Active Directory P1, enabling Multi-Factor Authentication (MFA) for all users and Conditional Access policies[3]. This means you can enforce that only verified users on compliant devices can access company resources, significantly reducing risk from stolen passwords. (MFA alone blocks 99.9% of account attacks[4].) Conditional Access allows policies like “Only allow login to M365 if the device is managed and healthy, or if coming from certain locations”. This identity-centric control is a cornerstone of Zero Trust, and something a network firewall cannot do. Single Sign-On also improves security (users have fewer passwords to manage, reducing phishing risks)[5].
- Microsoft Defender for Office 365 (Email and Collaboration Security): This suite provides advanced threat protection for email, OneDrive, SharePoint, and Teams. It includes Safe Attachments (opening attachments in a detonation sandbox to catch zero-day malware) and Safe Links (URL scanning and rewriting to block phishing links at click time)[2]. It also adds anti-phishing algorithms that detect impersonation or spoofing attempts. These protections address threats (like phishing and ransomware) at the content level, regardless of network path. For instance, an employee working from home gets the same email threat protection as one behind the office firewall[2]. Traditional firewalls alone have limited visibility into such targeted content threats.
- Microsoft Defender for Business (Endpoint Security): This is an enterprise-grade endpoint protection platform now included in M365 Business Premium[2]. It provides next-generation antivirus, behavioral monitoring, and Endpoint Detection and Response (EDR) capabilities across Windows PCs (and extends to Mac, iOS, Android)[2]. Critical features:
- Anti-Malware and EDR: Defender uses AI-driven cloud protection to catch malware (viruses, ransomware, spyware) and suspicious behavior on the device in real time. If malware is detected on a laptop, it can automatically quarantine the threat and alert IT—no matter where that laptop is located or what network it’s on[6].
- Attack Surface Reduction (ASR): Rules to harden the endpoint by blocking vulnerable behaviors (e.g. preventing Office macros from spawning executables, or blocking script abuse) which stop many attacks at an early stage[6]. These act like a personal firewall against exploit techniques, beyond what network devices do.
- Network Protection & Web Filtering: Defender for Business includes Network Protection which extends the idea of a firewall to each device. It can block outbound connections from endpoints to risky domains (e.g. if a user clicks a phishing link, Defender can prevent the connection even if off the corporate network)[2]. It also offers Web Content Filtering by category via the Defender cloud, effectively doing what a web-filtering firewall does, but on the endpoint itself[6]. For example, an Intune policy can enforce that the Windows Defender Firewall is enabled on all profiles and apply web threat protection policies to block phishing sites[6]. This means each laptop has a continuously updated “cloud-informed firewall” for web threats – protection travels with the device.
- Firewall & Device Control: Through Intune (Endpoint Manager), admins can ensure the built-in Windows Defender Firewall is ON and configured on every managed PC[7]. You can set rules or simply rely on Windows’ default-deny of unsolicited inbound traffic (which is akin to basic firewall functionality on each device). In short, M365 Business Premium makes sure every endpoint has its own firewall and AV/EDR sensor active[6] – a distributed security model.
- Automated Investigation and Response: Defender can auto-investigate alerts and even remediate issues across devices (e.g. isolate a machine, remove a malicious file) without waiting for human intervention[2].
- Intune – Mobile Device Management (MDM) and Mobile Application Management (MAM): Intune allows you to manage and secure devices and apps. You can enforce compliance policies: require disk encryption (BitLocker), strong passwords, up-to-date OS patches, enable antivirus and firewall, etc., on all company devices[7]. Non-compliant devices can be blocked from access (via Conditional Access). Intune also lets you wipe corporate data from lost devices or apply App Protection Policies on BYOD (e.g. prevent copy-paste from work apps to personal apps)[8]. By keeping devices in a known secure state and under watch, Intune reduces the risk of infection or data leakage that a firewall at the office couldn’t prevent if the device is off-network.
- Data Protection and Compliance (Microsoft Purview): Business Premium includes features like Information Rights Management, Data Loss Prevention (DLP), sensitivity labeling (via Azure Information Protection P1)[9], and message encryption. These help ensure sensitive info is not leaked or accessed improperly – for example, DLP can block an employee from emailing out a credit card number or uploading confidential files to unapproved services. A firewall might block certain websites, but it cannot understand the content of a file being sent out; Purview DLP can, and it travels with the data (within M365 ecosystem). Email encryption can protect data in transit beyond the firewall’s reach.
- Cloud App Security (Defender for Cloud Apps) – although not fully included in Business Premium, integration points exist (like app discovery logs via Defender endpoint). For many SMBs primarily using Microsoft 365 services, the need for a separate Cloud Access Security Broker (CASB) is reduced since most data stays within M365’s protected environment.
In effect, M365 Business Premium transforms security from a point-in-time network checkpoint to an always-on, holistic defense. Each user must prove their identity (MFA), each device is checked and monitored, each email or file is scanned, and sensitive data is governed. This aligns with the Zero Trust model (never trust, always verify).
Crucially, these protections apply uniformly whether an employee is in the office behind a simple firewall, or on the go using public Wi-Fi. For example, if a user’s home PC is infected with malware, a traditional office firewall can’t help; but if that PC is managed via Business Premium, Defender on the endpoint would catch and contain the malware[6]. Similarly, if an attacker phishes an employee, Safe Links can block the click whether or not they’re on the corporate network[2].
To maximize security, an SMB should ensure Business Premium is fully configured to “maximum” security – it’s not automatic. Out of the box, some features require setup by an admin. In the next section, we illustrate how to configure M365 Business Premium so that an SMB environment is locked down, effectively taking over many duties of a hardware firewall.

Configuring M365 Business Premium to Replace Firewall Functions
To effectively reduce reliance on a dedicated firewall, an SMB must enable and fine-tune M365 Business Premium’s security features. Here is how to configure the suite to achieve a high-security posture (often referred to as “configure to the max”):
- Enforce Multi-Factor Authentication (MFA) for all users: Enable MFA for every account, either via Security Defaults or Conditional Access policy[3]. This ensures that even if passwords are phished, attackers cannot easily use them. (Administrators and remote access accounts must have MFA – these are high-risk targets). According to Microsoft, MFA thwarts 99.9% of automated credential attacks[4].
- Set Conditional Access Policies: Go beyond basic MFA by defining rules in Azure AD:
- Require compliant devices for certain sensitive applications (e.g., allow SharePoint access only from Intune-enrolled devices or through browser sessions with data controls)[10].
- Block access from risky sign-ins or unfamiliar locations unless additional verification is passed.
- Perhaps disallow legacy authentication protocols which bypass MFA. These policies ensure only trusted devices and users access your cloud resources, achieving a role similar to a firewall blocking unknown machines.
- Onboard all devices to Intune and Defender for Business: All company PCs (and Macs, mobile devices) should be enrolled in Intune MDM. This will:
- Push down a Security Baseline configuration (Intune has templates) that enables Windows Defender Antivirus, cloud protection, and the Windows Firewall on each endpoint[6].
- Deploy the Defender for Business endpoint agent (on Windows 10/11, enabling Intune onboarding will automatically enroll them into Defender for Business EDR)[6]. Verify in the Microsoft 365 Defender portal that devices show up as secure and reporting.
- Configure Attack Surface Reduction (ASR) rules via Intune. For example, turn on Controlled Folder Access to protect documents from ransomware encryption, and enable rules like blocking Office from creating child processes[6]. These settings harden devices against threats that might slip past network controls.
- Ensure Web Protection is active: via Intune security policies, enable Network Protection and, optionally, Web Content Filtering categories (e.g., block known malware sites or adult content company-wide). A check on a test device’s Windows Security > App & Browser Control can confirm these are on[6].
- Firewall rules: Intune can enforce firewall rules if needed (e.g., to block SMB file sharing traffic on public networks, or allow certain ports for an app). At minimum, verify the firewall is enabled on domain, private, and public profiles[6] – Intune’s default Device Compliance policy can flag if firewall or AV is off.
- Enable Office 365 Advanced Threat Protection policies:
- In the Microsoft 365 Defender portal (Security Center), configure Safe Links and Safe Attachments for all users. For Safe Attachments, use “Dynamic Delivery” so users get email body instantly while attachments are scanned in background[3]. Enable Safe Attachments for SharePoint/OneDrive/Teams as well[6].
- Set up Anti-phishing policies to protect high-risk users or domains (e.g., ensure the CEO’s display name can’t be impersonated easily in incoming mail). Also configure Spoof intelligence and Impersonation protection features which come with Defender for O365.
- Train users: Despite technical controls, phishing can still trick users. Use the Attack Simulator in M365 or third-party phishing tests to educate staff.
- Email Security and Spam Tuning: Although Exchange Online Protection (EOP) automatically filters spam/malware, review the policies:
- Ensure ATP Anti-Spam is on and consider stricter thresholds if spam is a problem.
- Enable Outbound spam alerts to catch if an internal account is compromised and sending malicious emails (which a firewall wouldn’t catch).
- Apply DMARC, DKIM, SPF for your email domain to prevent spoofing.
- **Enable and enforce *BitLocker encryption* on all Windows devices via Intune**. This ensures data remains safe even if a device is stolen. (While unrelated to network threats, it’s a critical part of a “fully secure” posture that a firewall doesn’t address).
- Use Data Loss Prevention (DLP) and Sensitivity Labels: In the Purview compliance portal, create DLP policies for sensitive info (credit cards, personal IDs, etc.) to prevent accidental leaks via email or Teams. Configure Sensitivity Labels (with encryption if needed) for confidential data, so even if files leave your environment they remain protected[9]. These measures mitigate insider threats and data exfiltration that a firewall could never catch (since they operate at the content level and follow the data).
- Monitor and Respond: Set up alerting in the security portal for important events (e.g., multiple failed login attempts, malware found on a device, user added to admin role). M365 Defender’s dashboards should be regularly checked. Many SMBs use an IT partner or MSP to manage this; if so, the partner can use tools like Microsoft 365 Lighthouse for multi-tenant visibility.
- Incident Response Plan: Even without a dedicated firewall, SMBs should have a plan using M365 tools. For example, if a breach is suspected, use Azure AD to disable the account, Intune to wipe or lock a device, Defender to isolate the device from the network, and then investigate with Defender for Business’ logs[11].
- Maintain a Basic Network Firewall/Router: While M365 covers users and data, you should still have a basic firewall at any office location for fundamental network hygiene:
- Make sure default router passwords are changed and firmware updated.
- Enable basic firewall features (block all unsolicited inbound traffic, only allow necessary ports like VPN or remote desktop if needed – and consider turning those off entirely in favor of cloud solutions).
- If using Wi-Fi, use strong WPA2/3 encryption. Segment guest Wi-Fi from corporate devices.
- This “plumbing” level of security ensures that if employees do come to office or if there are local servers/IOT devices, they have some perimeter protection against internet threats like port scans. However, this box can be a simple device (often provided by the ISP or a low-cost business router) since the heavy lifting of threat detection is handled by M365.
By following the above steps, an SMB will have multiple layers of cloud-driven security active: strict identity verification, well-protected endpoints (with local firewall and global intelligence), and real-time scanning of content and communications. In such an environment, a high-end hardware firewall provides relatively little additional benefit, since there are few gaps for it to cover. The organization’s data is largely on Microsoft’s secure cloud or on encrypted, managed devices; users authenticate through Azure AD with MFA; threats like malware are caught on devices or in emails by Defender.
Importantly, this configuration is also more suitable for remote work: it doesn’t force traffic through a central choke point, which could become a bottleneck or single point of failure. Each device and cloud app is self-secured, allowing direct yet safe connectivity.
Anecdotally, IT consultants report that well-secured M365 environments experience dramatically fewer incidents. For example, enforcing MFA and device compliance has stopped password-related breaches, and Defender for Business has automatically contained malware that previously might have spread on the network. These successes highlight that investment is better spent on maintaining M365 security (and user awareness) than on firewall appliances.
Comparison: High-End Firewalls vs. M365 Business Premium Security
To summarize the differences, the table below compares a traditional dedicated firewall appliance approach versus the Microsoft 365 Business Premium security approach, across key criteria:
| Security Aspect | High-Priced Firewall Device (Perimeter-Based) | M365 Business Premium Security (Cloud/Endpoint-Based) |
|---|---|---|
| Network Threat Protection | Strong at blocking external network attacks at office site. Intrusion Prevention Systems can detect known exploits, DDoS, port scans, etc. Effective for on-prem servers and LAN. However, provides no protection when users connect from outside networks (unless via VPN)[1]. | Distributed protection on each device via Defender’s next-gen antivirus and network protection. Blocks malware, suspicious traffic, and malicious domains directly on endpoints[6]. Cloud intelligence feeds updated threat info to all devices. Covers users anywhere, not just in office. Azure AD Conditional Access can also block network access based on location or risk. |
| Remote Workforce Coverage | Requires VPN to channel remote traffic through the firewall for full protection. If users don’t use VPN (common for SaaS apps), those sessions bypass the firewall completely. Firewalls have “no visibility into remote users on unmanaged networks”[1]. | Built for remote/hybrid work. Security is tied to user identity and device, not physical network. All policies (MFA, device compliance, Defender) apply equally off-network. Examples: A laptop is protected on public Wi-Fi by its own firewall/Defender; cloud email is filtered by Microsoft’s datacenters[2]. No need for VPN for security – conditional access and app protections govern access. |
| Email & Phishing Protection | Some UTMs can filter SMTP email for spam/viruses if email flows through them. But many SMBs use Exchange Online, meaning email bypasses the on-prem firewall entirely. Firewalls cannot analyze the content of Office 365 emails or Teams chats. | Robust built-in Email security (Defender for Office 365): Always on, scanning every email and link. Phishing emails are blocked or neutralized by Safe Links/Attachments[2]. Impersonation protection and AI detect fraud attempts. These protections don’t depend on user’s network – even a home user clicking a phishing link gets blocked[2]. |
| Web Filtering & Malicious URLs | Yes, can block websites by category or reputation for any user traffic going through it. However, SSL inspection may be needed to see inside HTTPS, which adds complexity. Doesn’t help remote devices off-network. | Yes, via Defender’s Network Protection and Web Content Filtering on endpoints: Blocks access to known dangerous domains enterprise-wide[2]. Configurable categories (gambling, etc.) on each device. Also, Safe Links feature in M365 rewrites URLs in emails and Office docs to prevent clicks to bad sites[2]. These apply regardless of network – essentially each device has a web filter and the cloud services do too. |
| Internal Threats & Lateral Movement | Offers internal network segmentation and can detect some suspicious lateral traffic, but once an attacker or malware is inside the network, a firewall’s ability to stop it is limited (especially if it uses allowed ports). It treats internal traffic as trusted by default[1]. | Uses a Zero Trust mindset: no inherent trust for internal traffic. Every access is verified. If a device is compromised, Defender can flag abnormal behavior (e.g., ransomware-like file access patterns) and isolate that device[6]. Conditional access can force re-auth or block if a user account exhibits risky signs. So, lateral movement is constrained because compromised credentials or devices quickly lose their access. |
| Device Security (AV, Firewall) | Not provided by perimeter firewall – you’d need separate endpoint AV on each machine. The network firewall can’t stop an attack that originates from a USB drive or a rogue insider launching malware from within. | Comprehensive endpoint security included: Every Windows PC gets Defender AV/EDR with Business Premium[2]. Intune ensures host firewalls, encryption, and updates are enabled[7]. Threats are stopped at the device. Even if a user runs an infected file, Defender will catch and quarantine it, often before it spreads[6]. |
| Access Control & Identity | Basic network-level control (IP or port-based rules, VLANs). Cannot differentiate users beyond IP/MAC or require MFA. VPN can enforce user auth for entry, but once connected, internal access is broad (unless complex network ACLs set up). | Granular identity-based access: Azure AD Conditional Access can grant or deny access to apps based on user, group, role, device state, location, etc.[3]. Can enforce MFA, device compliance, even time-of-day. This fine-grained control means even if network is open, data access is locked to only authorized, verified sessions – a level of control traditional firewalls don’t have. |
| Data Loss Prevention | Limited. A firewall might block certain file types or large transfers, but it cannot understand the contents of files (e.g. detect IP or GDPR data) leaving the network without complex DLP proxies (generally not in SMB firewalls). | Built-in DLP and encryption: Business Premium includes DLP policies that detect sensitive info in emails or files and prevent it from being shared outside policy[9]. Also, sensitivity labels can encrypt documents so even if they leave approved channels, they remain inaccessible to outsiders. This helps prevent data exfiltration by malicious insiders or malware. The firewall is out of the loop; M365’s cloud services provide this protection at the app/data layer. |
| Management & Maintenance | Dedicated appliance requires setup and ongoing management (rule updates, firmware patches, subscription renewals for threat lists). Needs an expert to interpret logs or tune rules to avoid blocking business traffic. Hardware has capacity limits – may need upgrade if company grows. | Unified cloud management through Microsoft 365 admin portals. Policies are mostly set-and-forget, with Microsoft managing the threat intelligence updates. No physical hardware to patch or replace – Microsoft ensures the security cloud is updated. IT admin focuses on reviewing security reports and adjusting policies, rather than low-level traffic rules. This reduces overhead and error risk. Additionally, one integrated ecosystem means fewer compatibility issues. |
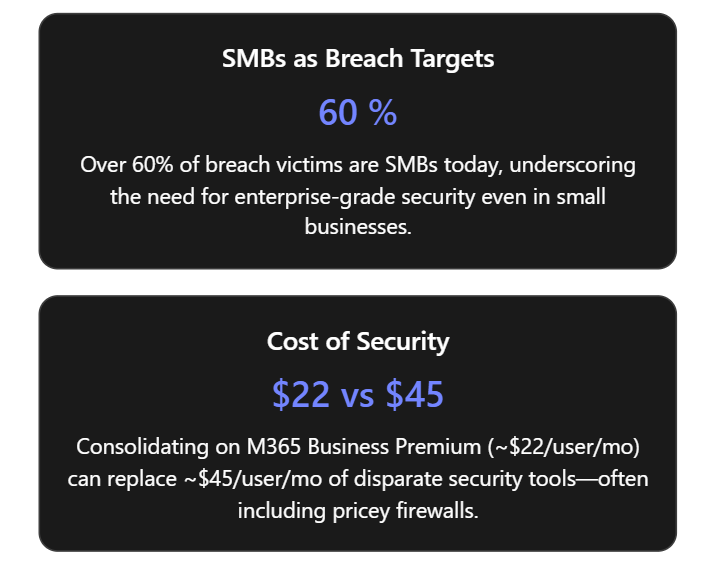
| Cost | Typically a significant upfront cost ($500–$5,000+ depending on model and size) plus annual support/license fees (for security services subscriptions, often a few hundred dollars a year). Costs are mostly fixed, not per user (good for static environments, but costly for small teams relative to usage). If multiple sites, need multiple devices. | Subscription per user – Business Premium is about $22/user/month (versus ~$12.50 for Business Standard with no advanced security)[12]. For an SMB with 20 users, that’s ~$4,400/year, which also includes all Office apps and cloud services. Since many SMBs would already pay for email/Office, the increment for security is smaller. It scales with user count – you pay only for the people you have. No extra charge for deploying on up to 5 devices per user. This can be more cost-effective than a $3000 firewall serving 20 users, especially if those users are rarely in office. Also, consolidation saves costs: Business Premium’s security can replace multiple point products (AV, VPN, email filtering), yielding license savings[5]. |
Table: Comparison of a traditional on-premises firewall approach vs. Microsoft 365 Business Premium’s cloud-centric security in an SMB context[1][2][3].
As the table shows, Microsoft 365 Business Premium provides a broad spectrum of protections that overlap with or surpass firewall capabilities in many areas, especially for securing remote users and cloud-based workflows. High-end firewalls still excel at certain network-specific functions (like protecting legacy on-prem servers or linking office networks via VPN), but if your infrastructure is largely cloud-based (Exchange Online, SharePoint/OneDrive, Teams, etc.), those functions see diminished use.
Financially, the value proposition is clear: instead of spending thousands on an appliance and separate security software, an SMB can invest in Business Premium licenses that cover everything. A rough cost comparison: A UTM firewall for ~50 users might cost $2,000 upfront + $500/year, and you’d still purchase anti-virus for endpoints at maybe $30/device/year – over 3 years, that totals ~$5,500. In contrast, upgrading 50 users from a basic Microsoft 365 plan to Business Premium at +$9.50/user/month costs ~$17,100 over 3 years[12], but that also replaces email security subscriptions, separate VPN services, and provides far more capability (and productivity tools). For smaller teams (10–20 users), the math often favors skipping the big firewall; for larger, one might do both, but even then, the firewall is just one layer.
Conclusion: Basic Firewall + M365 Business Premium = Strong, Cost-Effective SMB Security
For a typical SMB with a distributed workforce and heavy reliance on cloud services, investing in Microsoft 365 Business Premium’s security stack offers more bang for the buck than purchasing high-priced firewall hardware. Business Premium, when properly configured, functions as a security shield that envelops each user and device, rather than just the office network perimeter. This modern approach is better aligned to current threats and work patterns:
- Remote and roaming users stay protected by cloud-driven security no matter where they work, something an on-premises firewall cannot achieve[1][6].
- Identity- and device-centric controls in M365 prevent breaches (through MFA, conditional access, endpoint hardening) rather than simply reacting at the network edge[3][6].
- Integrated threat protection across email, endpoints, and cloud apps stops phishing, malware, and other attacks more comprehensively than a perimeter device scanning traffic[2].
- Simplified management and scalability reduce the need for dedicated network security appliances and their upkeep, which is a relief for small IT teams.
That said, a basic firewall device is still recommended as part of a layered defense – essentially to handle what M365 doesn’t, such as: providing a minimal barrier between your office network and the wild internet (blocking unsolicited inbound connections), ensuring reliable site-to-site connectivity if needed, and offering fail-safe protections (for example, if a device isn’t yet enrolled in Intune, the network firewall might catch something). Fortunately, most SMB routers include these basic firewall features out-of-the-box. Thus, you likely do not need an expensive “next-gen” upgrade; a stable, basic firewall/router plus the security of M365 is sufficient in most cases.
In scenarios where an SMB still hosts significant on-premises assets (file servers, PBX systems, etc.) or has compliance requirements for network monitoring, a higher-end firewall or unified threat device might remain worthwhile. Additionally, some businesses add a cloud-based firewall-as-a-service (as part of a SASE solution) if they want to extend network-style controls to roaming devices without hardware. But for many, leveraging the security you already pay for in M365 Business Premium is the most cost-effective strategy.
Bottom Line: If your organization has maximized Microsoft 365 Business Premium’s security features – MFA on every account, Intune-managed and Defender-secured endpoints, up-to-date policies against phishing and data leaks – then pouring additional budget into a premium standalone firewall has diminishing returns. Your security posture will be strong with just a reliable basic firewall at any office Internet junction and the rich, cloud-backed protections in M365 guarding your users and data. In other words, Business Premium can legitimately reduce or eliminate the need for dedicated firewall hardware for a cloud-oriented SMB environment, allowing you to reallocate resources to other critical areas (like user training, incident response readiness, or improving infrastructure). This aligns with the industry shift to cloud-first security for SMBs, where trust is placed in platforms like Microsoft 365 to deliver comprehensive protection as a service[1][3], rather than piling on more physical devices.
References
[1] Beyond The Firewall and VPNs: The Ultimate SMB Guide
[2] Microsoft365BusinessPremiumPartnerOpportunityDeck
[3] Convincing SMBs to Invest in M365 Business Premium Strategies and Steps
[4] Here’s the Cybersecurity Verification Playbook you requested
[5] Renew-and-Upsell-SMB-Customers-with-Microsoft-365-Business-Premium-and-Microsoft-Defender-for-Business English Deck 1
[6] Onboarding a Windows Device into M365 Business Premium Step-by-Step Checklist
[7] Identifying and Securing Externally Shared Information in M365 Business Premium
[8] Onboarding Checklist for BYOD Windows Devices (Microsoft 365 Business Premium)
[9] Azure Information Protection (AIP) Integration with M365 Business Premium Data Classification & Labeling
[10] Require Managed Devices in M365 💻
[11] Handling a Breach in M365 Business premium
[12] CSP Masters – S2 – Overview
4 thoughts on “Security Without the High‑Priced Firewall: M365 Business Premium vs Traditional Firewalls for SMBs”